6.4: Exploitation tools (Pt 1)
Por um escritor misterioso
Last updated 19 setembro 2024

Computer security - Wikipedia

Automated Multi-Dataset Analysis (AMDA): An on-line database and analysis tool for heliospheric and planetary plasma data - ScienceDirect

Prevalence of anxiety and post-traumatic stress (PTS) among the parents of babies admitted to neonatal units: A systematic review and meta-analysis - eClinicalMedicine

WordPress 6.4 Release Leads: Charting a Path for Diversity

Breaking Fortinet Firmware Encryption
How to Stay Anonymous on Kali Linux in Every Step You Take?
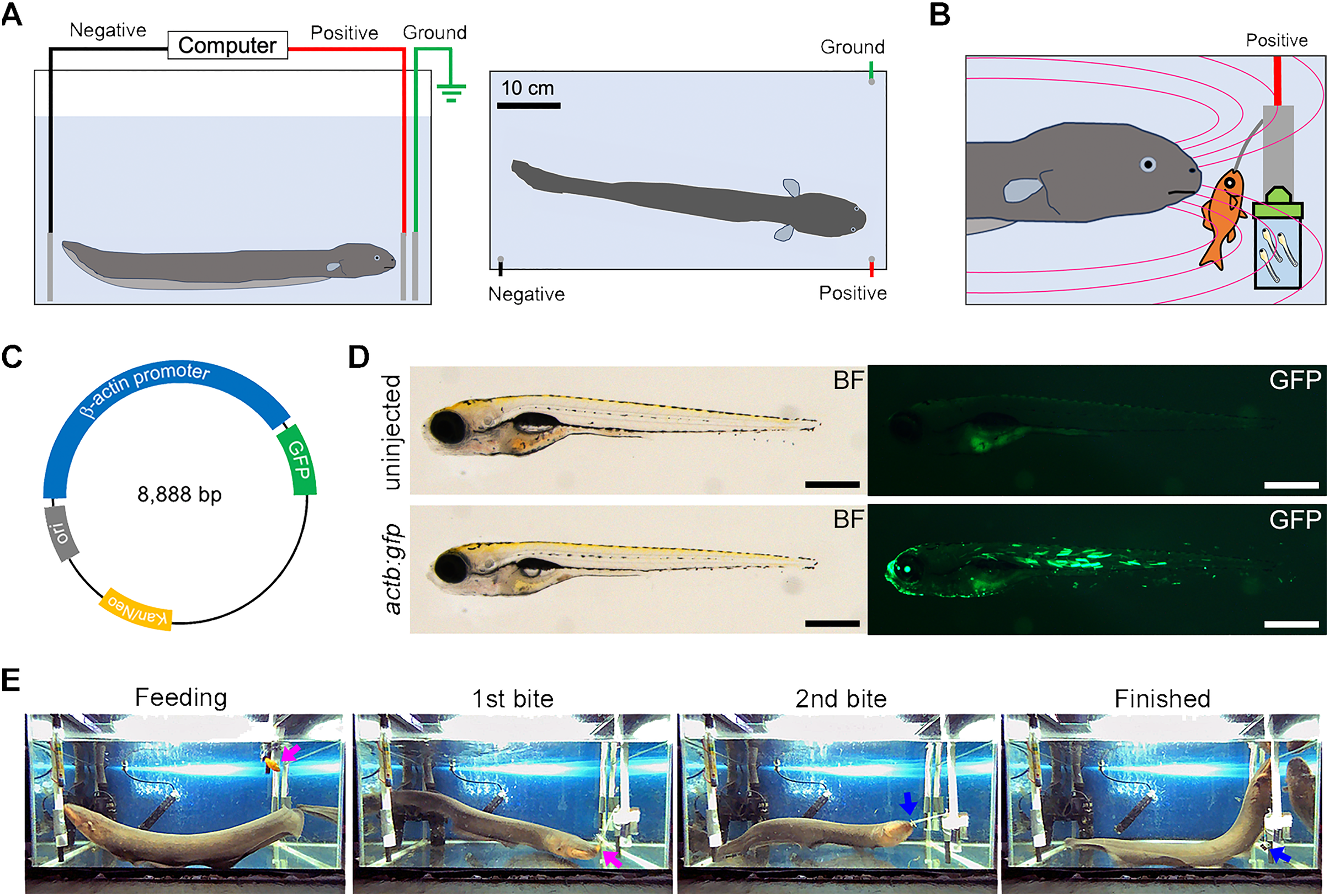
Electric organ discharge from electric eel facilitates DNA transformation into teleost larvae in laboratory conditions [PeerJ]

Controlling a Chemical Coupling Reaction on a Surface: Tools and Strategies for On-Surface Synthesis

WordPress 6.3.2 Security Release - What You Need to Know

6.4L: Long List of Failures - Diesel World

Windows 10 Nt Heap Exploitation (English version)
Top 18 tools for vulnerability exploitation in Kali Linux

The most exploited vulnerabilities in 2022
Recomendado para você
-
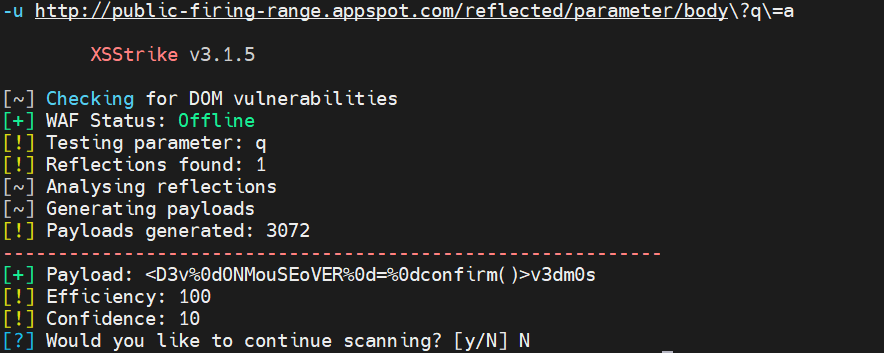
 XSStrike – XSS Detection and Exploitation Suite - Latest Hacking News19 setembro 2024
XSStrike – XSS Detection and Exploitation Suite - Latest Hacking News19 setembro 2024 -
 txt3rob/xsstrike-docker - Docker Image19 setembro 2024
txt3rob/xsstrike-docker - Docker Image19 setembro 2024 -
Usage · s0md3v/XSStrike Wiki · GitHub19 setembro 2024
-
 XSStrike Usage Example (v3.x)19 setembro 2024
XSStrike Usage Example (v3.x)19 setembro 2024 -
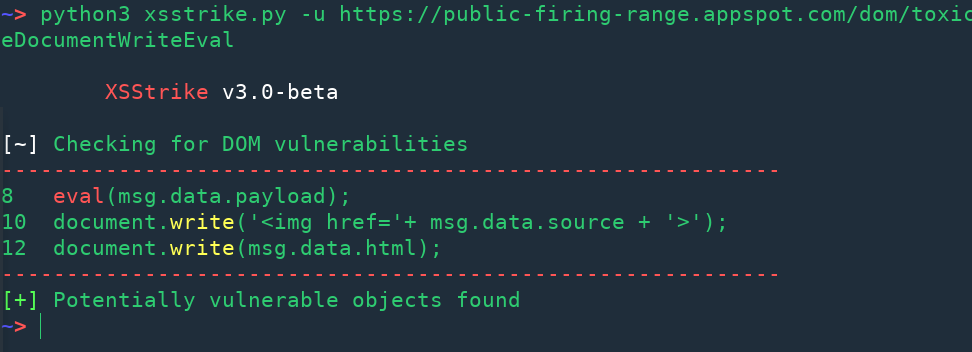 XSStrike v3.0 - Most Advanced XSS Detection Suite19 setembro 2024
XSStrike v3.0 - Most Advanced XSS Detection Suite19 setembro 2024 -
Kappala Roshan on LinkedIn: XSSTRike (Cross-Site Scripting Scanner)19 setembro 2024
-
 xsstrike 源码分析-安全客- 安全资讯平台19 setembro 2024
xsstrike 源码分析-安全客- 安全资讯平台19 setembro 2024 -
 利用XSStrike Fuzzing XSS漏洞- FreeBuf网络安全行业门户19 setembro 2024
利用XSStrike Fuzzing XSS漏洞- FreeBuf网络安全行业门户19 setembro 2024 -
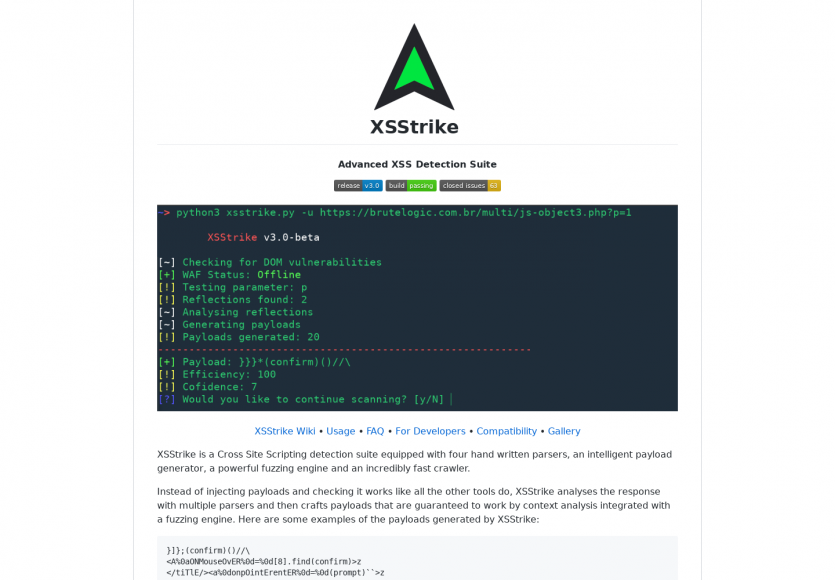 XSStrike : une suite de détection de failles XSS avancée - La Ferme du Web19 setembro 2024
XSStrike : une suite de détection de failles XSS avancée - La Ferme du Web19 setembro 2024 -
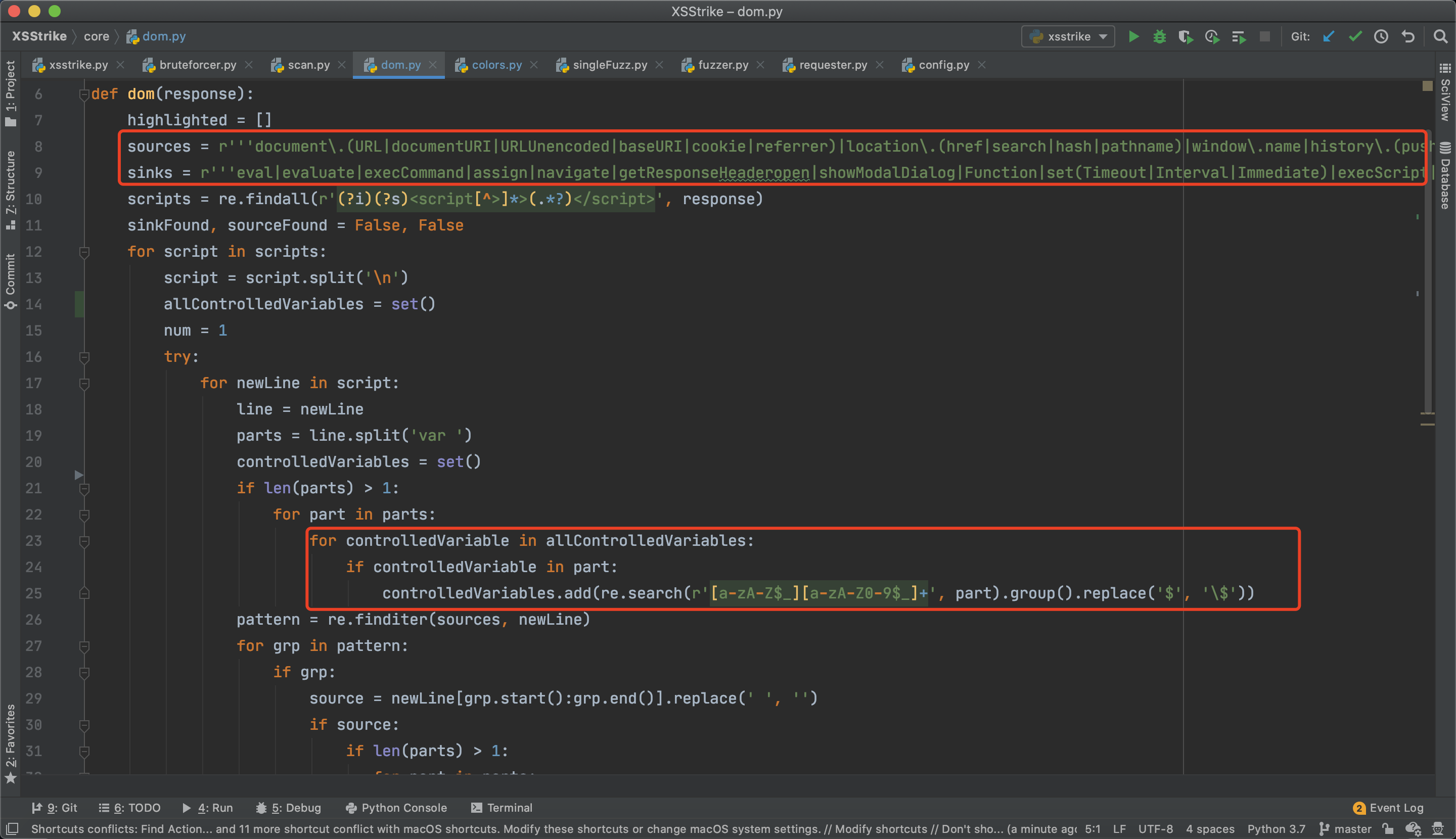 XSStrike源码分析-上19 setembro 2024
XSStrike源码分析-上19 setembro 2024
você pode gostar
-
 Eddy Sectional Sofa19 setembro 2024
Eddy Sectional Sofa19 setembro 2024 -
 ASEBEX on X: Vocês conhecem as bolsas Shichoson? São bolsas oferecidas aos descendentes das cidades da província de Okinawa. Estão abertas as inscrições para descendentes da cidade de Okinawa-Shi ! Maiores informações19 setembro 2024
ASEBEX on X: Vocês conhecem as bolsas Shichoson? São bolsas oferecidas aos descendentes das cidades da província de Okinawa. Estão abertas as inscrições para descendentes da cidade de Okinawa-Shi ! Maiores informações19 setembro 2024 -
 Assistir Five Nights At Freddy's Online Dublado by ila36 on DeviantArt19 setembro 2024
Assistir Five Nights At Freddy's Online Dublado by ila36 on DeviantArt19 setembro 2024 -
 Animan - Meme by Nose01927 :) Memedroid19 setembro 2024
Animan - Meme by Nose01927 :) Memedroid19 setembro 2024 -
 Arlo, Animated Character Database19 setembro 2024
Arlo, Animated Character Database19 setembro 2024 -
 Ódio ou paixão? Hater de One Piece cria 300 emails para dar Nota ao Anime Você Sabia Ani Q - iFunny Brazil19 setembro 2024
Ódio ou paixão? Hater de One Piece cria 300 emails para dar Nota ao Anime Você Sabia Ani Q - iFunny Brazil19 setembro 2024 -
 Pastor Xbox 🙏🏽💚 on X: Microsoft Responde Aprovação da Activision Blizzard pelo CADE 🇧🇷 A decisão do SG-CADE está alinhada com a visão de que a proposta de Aquisição da Activision Blizzard19 setembro 2024
Pastor Xbox 🙏🏽💚 on X: Microsoft Responde Aprovação da Activision Blizzard pelo CADE 🇧🇷 A decisão do SG-CADE está alinhada com a visão de que a proposta de Aquisição da Activision Blizzard19 setembro 2024 -
 CONFIRMAN LA 2 TEMPORADA DE KAMI TACHI NI HIROWARETA OTOKO ! ! !19 setembro 2024
CONFIRMAN LA 2 TEMPORADA DE KAMI TACHI NI HIROWARETA OTOKO ! ! !19 setembro 2024 -
 what is dragon trade value? : r/bloxfruits19 setembro 2024
what is dragon trade value? : r/bloxfruits19 setembro 2024 -
 Moo Moo I'm 2 Set Cow 2nd Birthday Pink & Blue Fence Farm19 setembro 2024
Moo Moo I'm 2 Set Cow 2nd Birthday Pink & Blue Fence Farm19 setembro 2024
