Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Last updated 05 novembro 2024

In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.
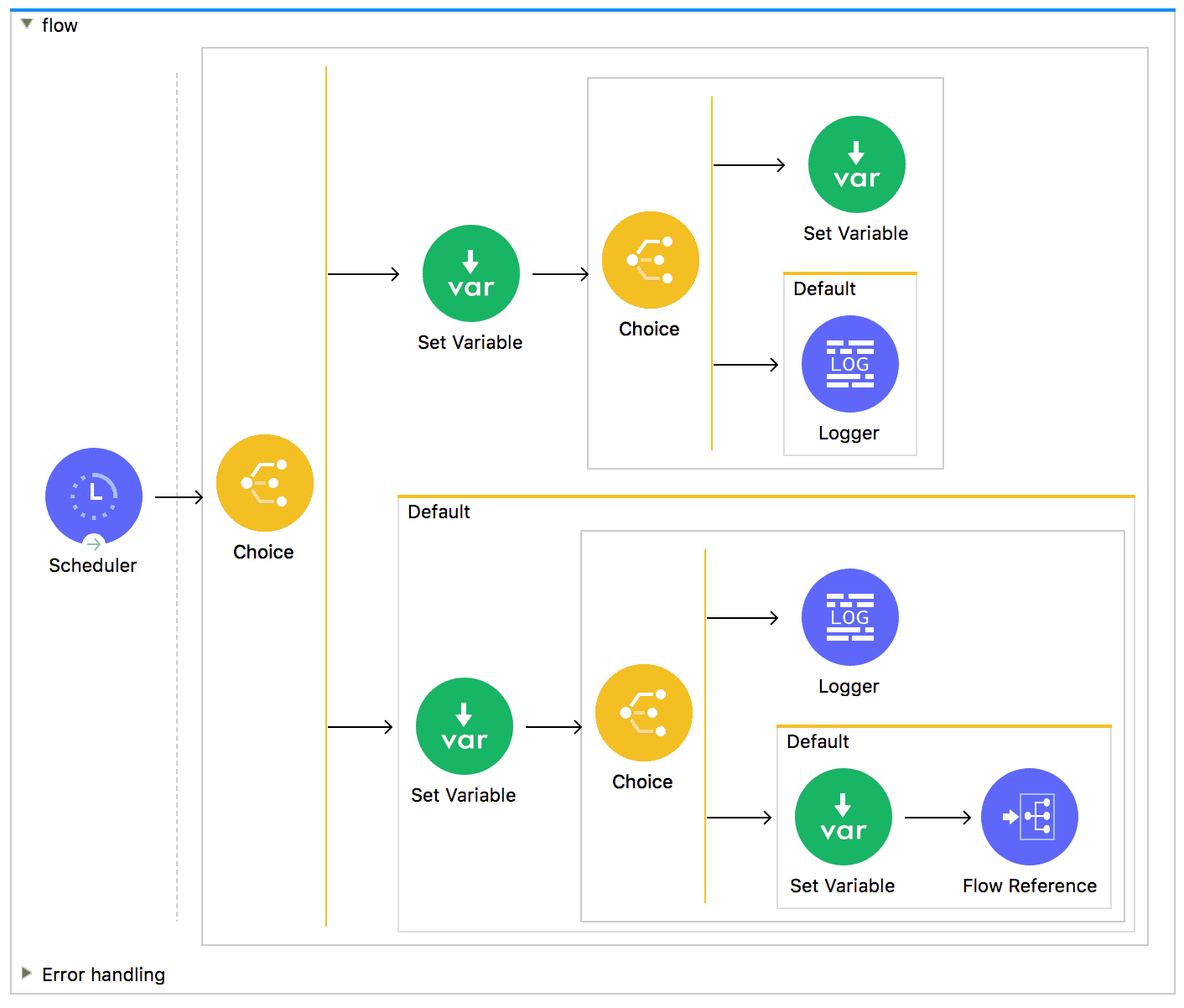
Mule programming style guide: stop abusing the choice router
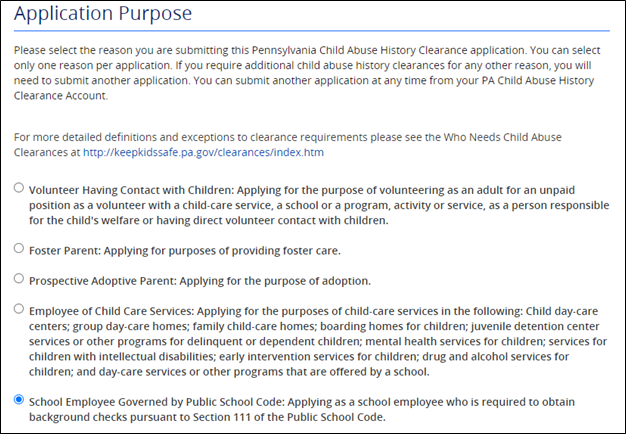
Instructions for Obtaining a Pennsylvania Child Abuse History

How to Prevent and Deal With Referral Fraud and Abuse

Microsoft Defender Attack Surface Reduction recommendations
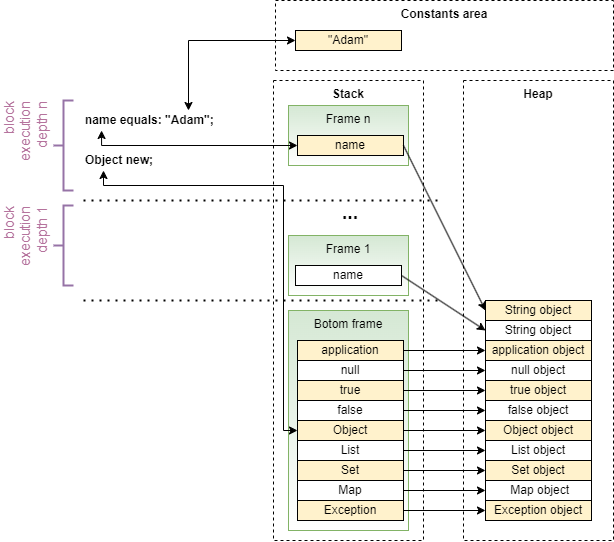
Smallscript - A Smalltalk-Inspired Scripting Language - CodeProject

Why Instagram Threads is a hotbed of risks for businesses

Coders' Rights Project Reverse Engineering FAQ

Malware Analysis: GuLoader Dissection Reveals New Anti-Analysis
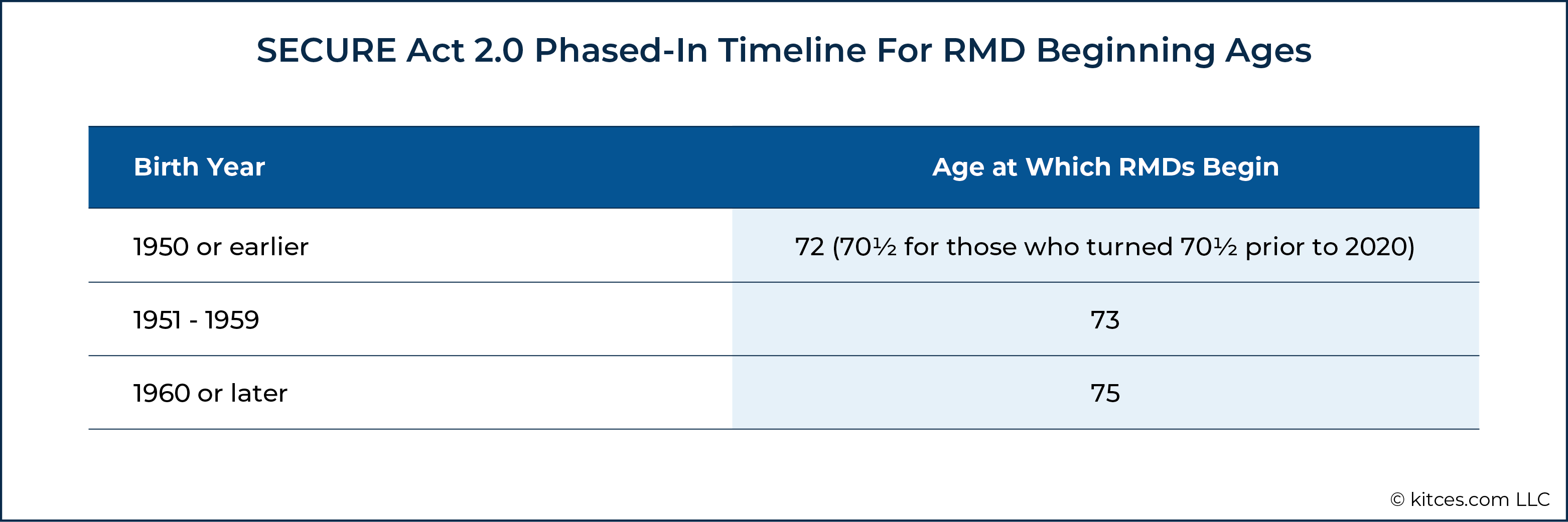
Secure Act 2.0: Detailed Breakdown Of Key Tax Opportunities

What is a Buffer Overflow Attack Types and Prevention Methods

Code of Ethics for Government Services Poster

How to protect, prevent and mitigate buffer overflow attacks

FastJSON deserialization bug can trigger RCE in popular Java
Recomendado para você
-
 Types of Exception in Java - Javatpoint05 novembro 2024
Types of Exception in Java - Javatpoint05 novembro 2024 -
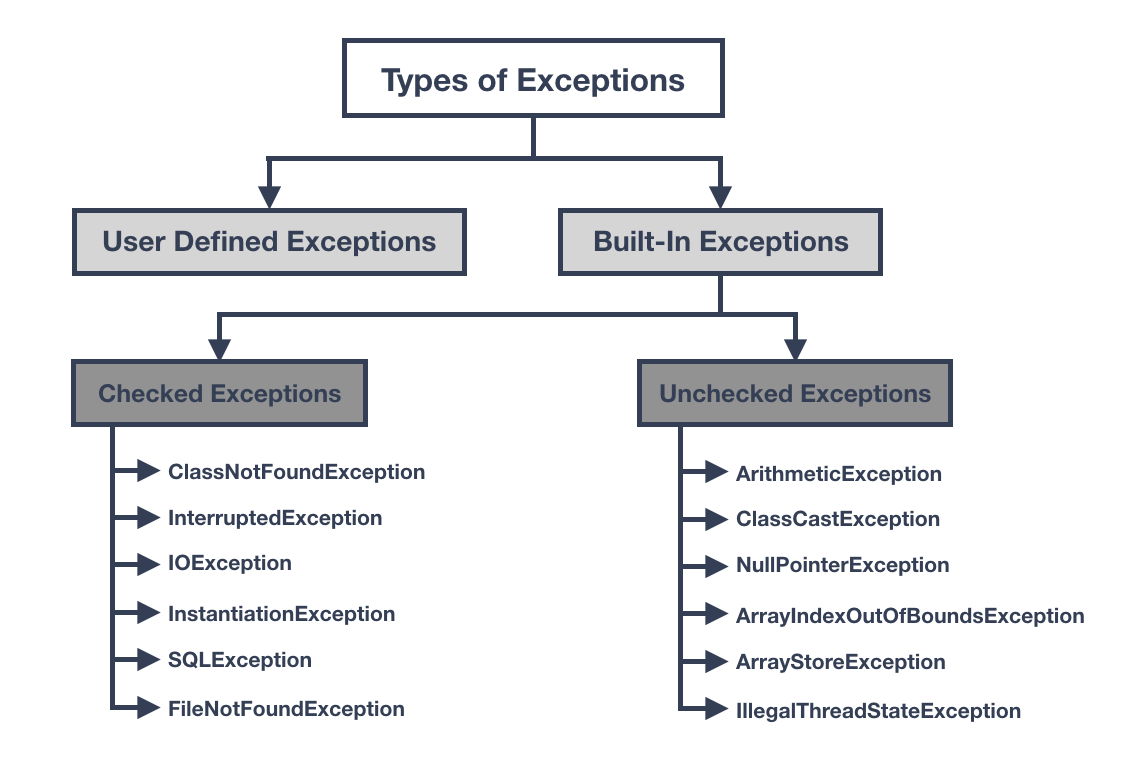 Checked and Unchecked Exceptions in Java, by Serxan Hamzayev, Javarevisited05 novembro 2024
Checked and Unchecked Exceptions in Java, by Serxan Hamzayev, Javarevisited05 novembro 2024 -
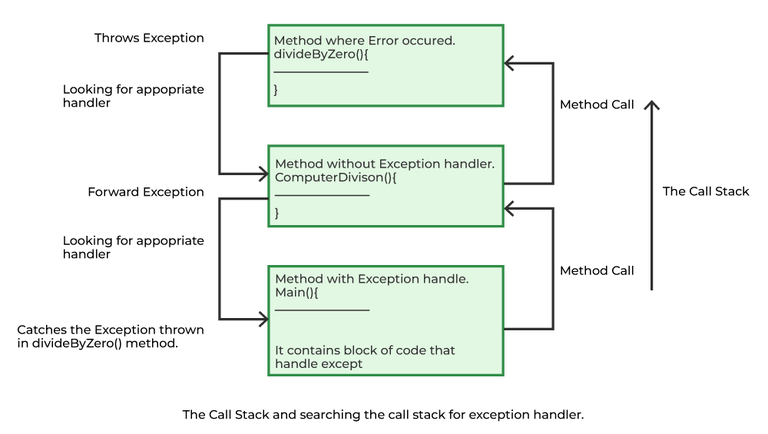 Exceptions in Java - GeeksforGeeks05 novembro 2024
Exceptions in Java - GeeksforGeeks05 novembro 2024 -
 JDBC Exception Handling - How To Handle SQL Exceptions05 novembro 2024
JDBC Exception Handling - How To Handle SQL Exceptions05 novembro 2024 -
 Best Exception Royalty-Free Images, Stock Photos & Pictures05 novembro 2024
Best Exception Royalty-Free Images, Stock Photos & Pictures05 novembro 2024 -
 Handling Exceptions in Dart & Flutter: Everything you need to know - QuickBird Studios05 novembro 2024
Handling Exceptions in Dart & Flutter: Everything you need to know - QuickBird Studios05 novembro 2024 -
Handle Exceptions - OutSystems 11 Documentation05 novembro 2024
-
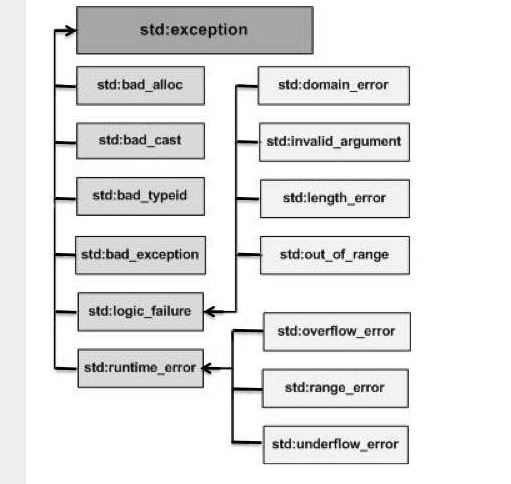 C++ Exception Handling. Back to, by Tech Notes05 novembro 2024
C++ Exception Handling. Back to, by Tech Notes05 novembro 2024 -
 Abusing Exceptions for Code Execution, Part 105 novembro 2024
Abusing Exceptions for Code Execution, Part 105 novembro 2024 -
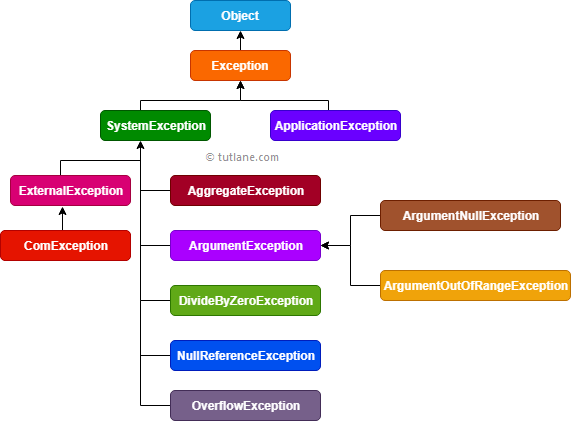 Visual Basic Exception - Tutlane05 novembro 2024
Visual Basic Exception - Tutlane05 novembro 2024
você pode gostar
-
 sfm Fnaf ucn) Withered Chica Mugshot v1 by xXMrTrapXx on DeviantArt05 novembro 2024
sfm Fnaf ucn) Withered Chica Mugshot v1 by xXMrTrapXx on DeviantArt05 novembro 2024 -
 Manchester United Have World's Most Expensively Assembled Squad: CIES05 novembro 2024
Manchester United Have World's Most Expensively Assembled Squad: CIES05 novembro 2024 -
 B32774H, 6H, 8H Series by EPCOS - TDK Electronics Datasheet05 novembro 2024
B32774H, 6H, 8H Series by EPCOS - TDK Electronics Datasheet05 novembro 2024 -
 Autism overload — Fucked up kids05 novembro 2024
Autism overload — Fucked up kids05 novembro 2024 -
Zoro (Zolo), Anime Mania (Roblox) Wiki05 novembro 2024
-
 Easy 3D Text Maker, 3D Logo Maker, Cool Logo Creator05 novembro 2024
Easy 3D Text Maker, 3D Logo Maker, Cool Logo Creator05 novembro 2024 -
 25+ Fun Games for 2 players - Suburban Wife, City Life05 novembro 2024
25+ Fun Games for 2 players - Suburban Wife, City Life05 novembro 2024 -
 Roblox changes after their avatar after 6 years, players react05 novembro 2024
Roblox changes after their avatar after 6 years, players react05 novembro 2024 -
Bruno De Blasi - Repórter de Tecnologia - Giz Brasil05 novembro 2024
-
 Genshin Impact: 60 Gemas essenciais e 10k mora (novo código/março05 novembro 2024
Genshin Impact: 60 Gemas essenciais e 10k mora (novo código/março05 novembro 2024

