Collecting XSS Subreddit Payloads
Por um escritor misterioso
Last updated 22 dezembro 2024
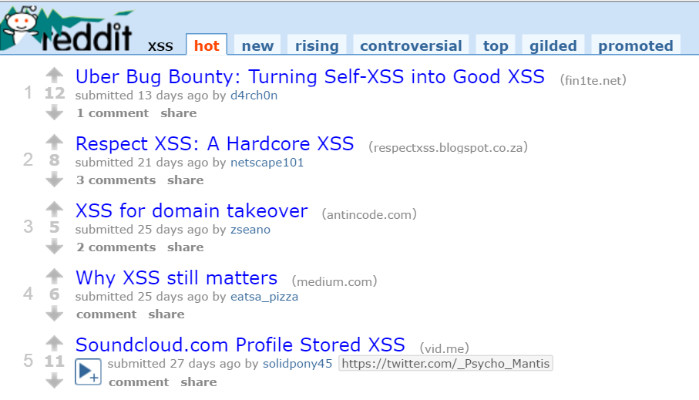
Having a good collection of Cross-Site Scripting (XSS) payloads is useful when you want to thoroughly test a web site’s ability to defend itself from being exploited. In most cases you can just run any one or more open source and/or commercial scanning tools to test your web site.

Phillip Maddux

Bypassing Character Limit — XSS Using Spanned Payload : r/InfoSecWriteups

Stored XSS vulnerability in image alt attribute to steal cookies (Bug Bounty) - Cybr

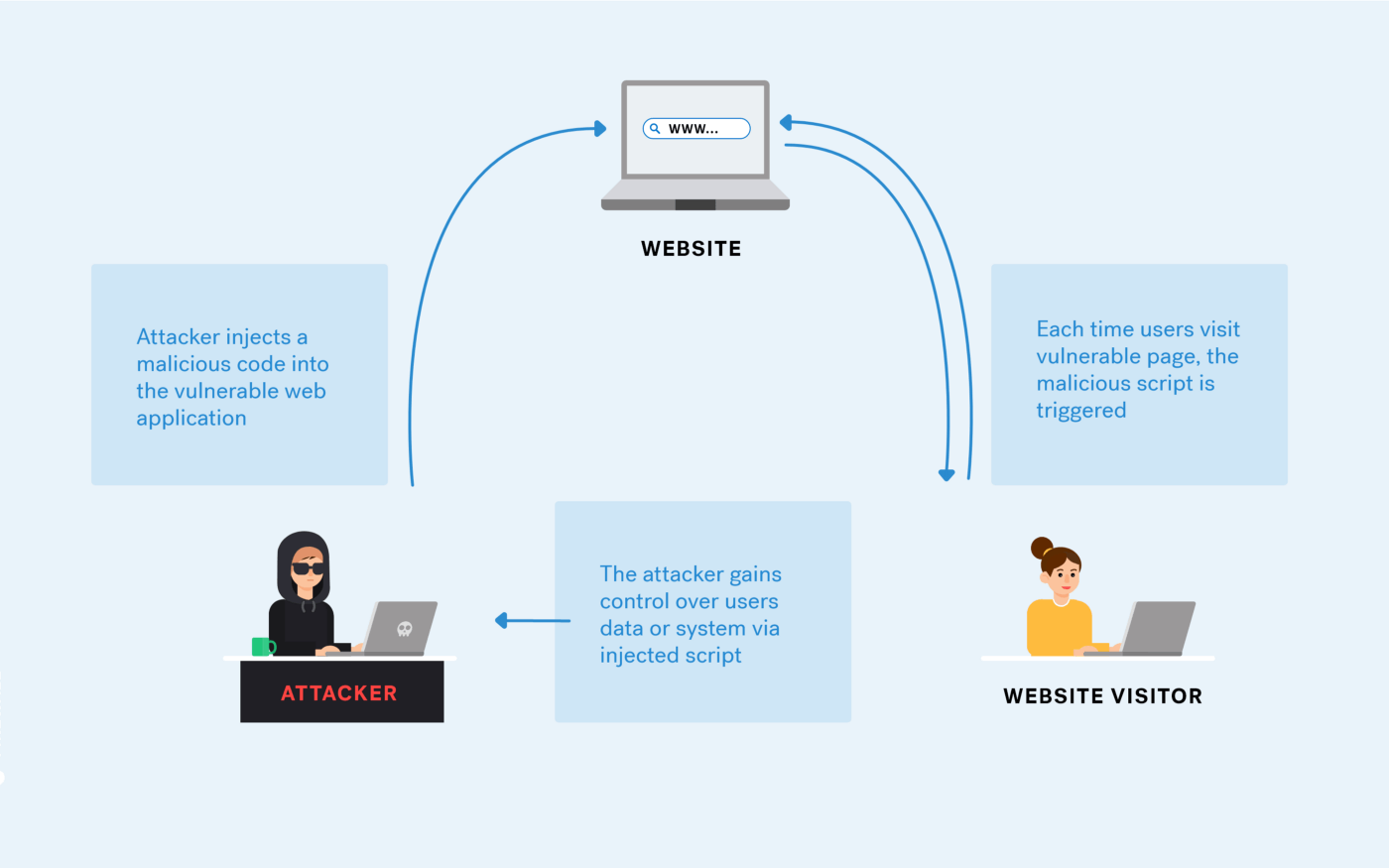
What is a Cross-Site Scripting (XSS) attack: Definition & Examples
Using Payload CMS to build a blog - LogRocket Blog

A Census of Deployed Pulse Connect Secure (PCS) Versions, NCC Group Research Blog

Researchers Discover Numerous Samples of Information Stealer 'Stealc' in the Wild

Collecting Payloads From CTF PCAPs
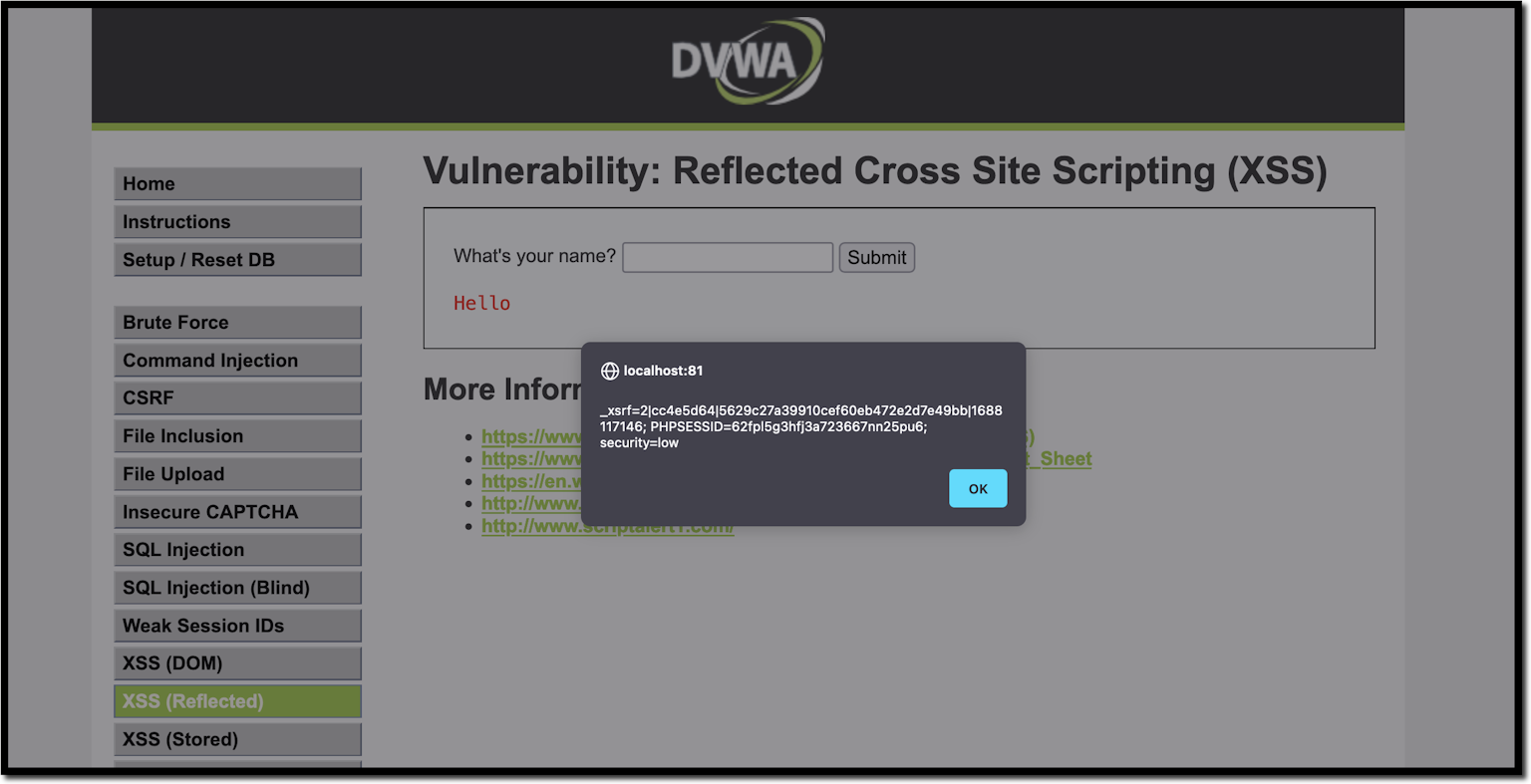
10 Practical scenarios for XSS attacks

A Detailed Guide to Cross-Site Scripting (XSS)
OWASP Juice Shop OWASP Foundation
Recomendado para você
-
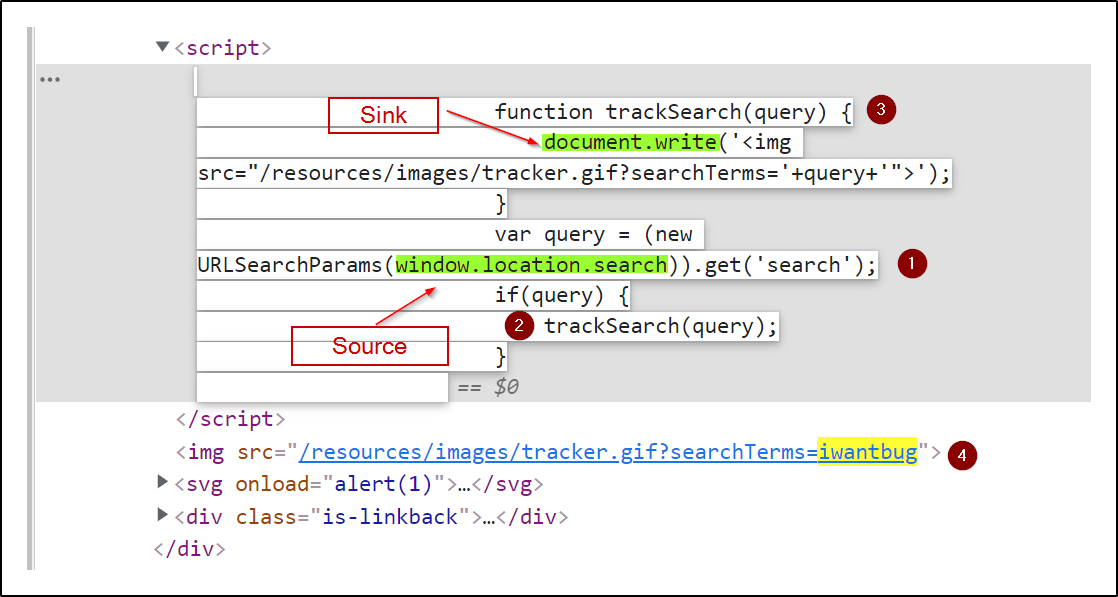 How DOM-based Cross-Site Scripting (XSS) Attack Works22 dezembro 2024
How DOM-based Cross-Site Scripting (XSS) Attack Works22 dezembro 2024 -
xss-payloads · GitHub Topics · GitHub22 dezembro 2024
-
GitHub - XSSPayloads/XSS: XSS Payloads22 dezembro 2024
-
 Obfuscated/Polyglot XSS Payloads Simplified with references.22 dezembro 2024
Obfuscated/Polyglot XSS Payloads Simplified with references.22 dezembro 2024 -
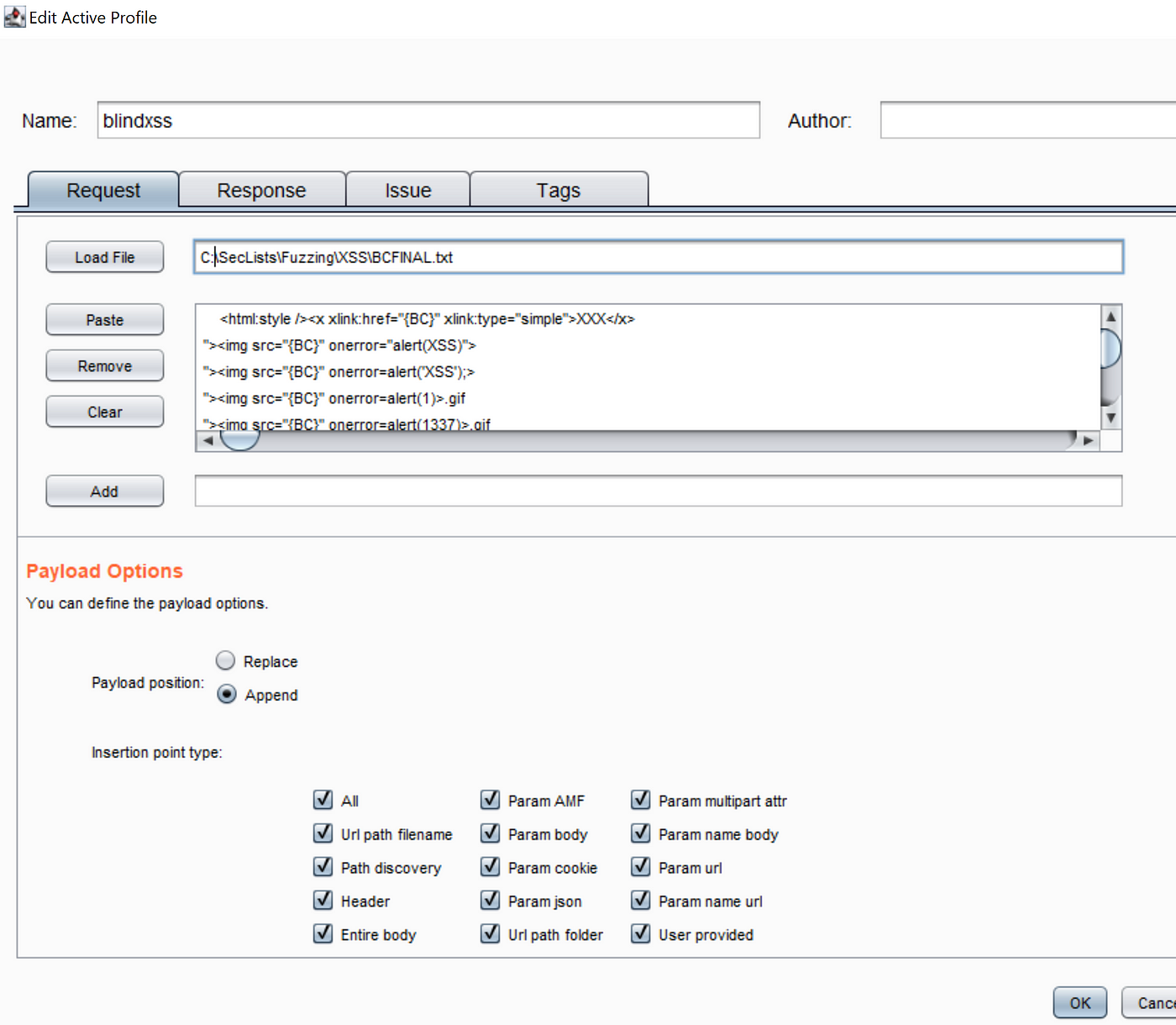 Testing Blind XSS Payloads. Get the payloads list and load it up22 dezembro 2024
Testing Blind XSS Payloads. Get the payloads list and load it up22 dezembro 2024 -
 The Art of XSS Payload Building Archives - Brute XSS22 dezembro 2024
The Art of XSS Payload Building Archives - Brute XSS22 dezembro 2024 -
 Transforming Self-XSS Into Exploitable XSS22 dezembro 2024
Transforming Self-XSS Into Exploitable XSS22 dezembro 2024 -
 A Pentester's Guide to Cross-Site Scripting (XSS)22 dezembro 2024
A Pentester's Guide to Cross-Site Scripting (XSS)22 dezembro 2024 -
 XSS cookie stealing - refabr1k's Pentest Notebook22 dezembro 2024
XSS cookie stealing - refabr1k's Pentest Notebook22 dezembro 2024 -
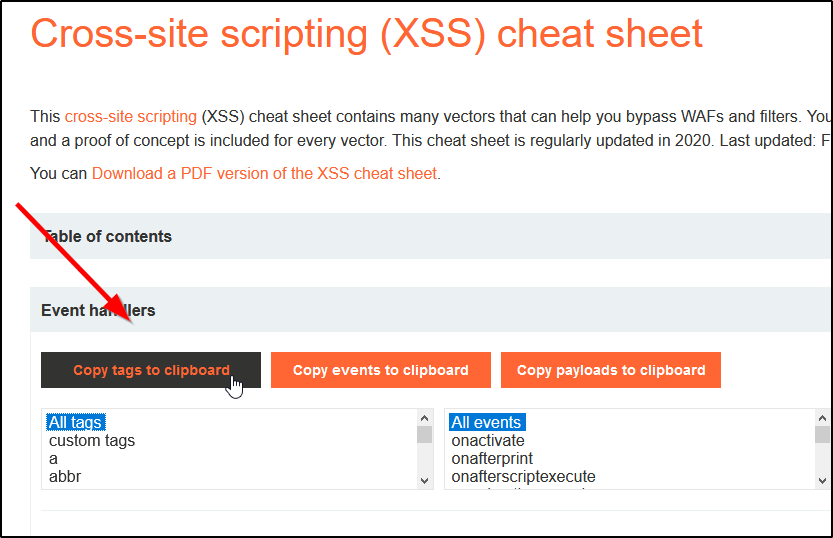 XSS Infinite Logins22 dezembro 2024
XSS Infinite Logins22 dezembro 2024
você pode gostar
-
 Stream Summer Walker & Jacquees - Playing Games Remix, @DJBroox by DJ BROOX22 dezembro 2024
Stream Summer Walker & Jacquees - Playing Games Remix, @DJBroox by DJ BROOX22 dezembro 2024 -
 Legion Anime APK Mod Download Latest Version For Android22 dezembro 2024
Legion Anime APK Mod Download Latest Version For Android22 dezembro 2024 -
 Dragon Ball Z Games - Giant Bomb22 dezembro 2024
Dragon Ball Z Games - Giant Bomb22 dezembro 2024 -
 Benoni ou Benjamim?22 dezembro 2024
Benoni ou Benjamim?22 dezembro 2024 -
 Mr. Pancho Gourmet Hot Dog at Miami International Mall - A Shopping Center in Doral, FL - A Simon Property22 dezembro 2024
Mr. Pancho Gourmet Hot Dog at Miami International Mall - A Shopping Center in Doral, FL - A Simon Property22 dezembro 2024 -
 Review of Fairy Gone Episode 01: A Twisted Friend from the Past and Fairy Primordials - Crow's World of Anime22 dezembro 2024
Review of Fairy Gone Episode 01: A Twisted Friend from the Past and Fairy Primordials - Crow's World of Anime22 dezembro 2024 -
 Dvd John Wick 2 MercadoLivre 📦22 dezembro 2024
Dvd John Wick 2 MercadoLivre 📦22 dezembro 2024 -
 Sao Paulo, Brazil. 03rd Apr, 2022. SP - Sao Paulo - 03/04/202222 dezembro 2024
Sao Paulo, Brazil. 03rd Apr, 2022. SP - Sao Paulo - 03/04/202222 dezembro 2024 -
 Laura bailey model hi-res stock photography and images - Alamy22 dezembro 2024
Laura bailey model hi-res stock photography and images - Alamy22 dezembro 2024 -
 Jogos piratas: 5 problemas que podem causar em sua máquina22 dezembro 2024
Jogos piratas: 5 problemas que podem causar em sua máquina22 dezembro 2024