Hackers Target Gamers With Microsoft-Signed Rootkit
Por um escritor misterioso
Last updated 22 dezembro 2024

Kernel mode driver can download second-stage payload directly to memory, allowing threat actors to evade endpoint detection and response tools.

Hackers Target Gamers With Microsoft-Signed Rootkit
Chinese hacking group uses new 'Fire Chili' Windows rootkit

What is a Rootkit and How to Detect It? - Shiksha Online

What is Malware? Examples & Prevention Tips

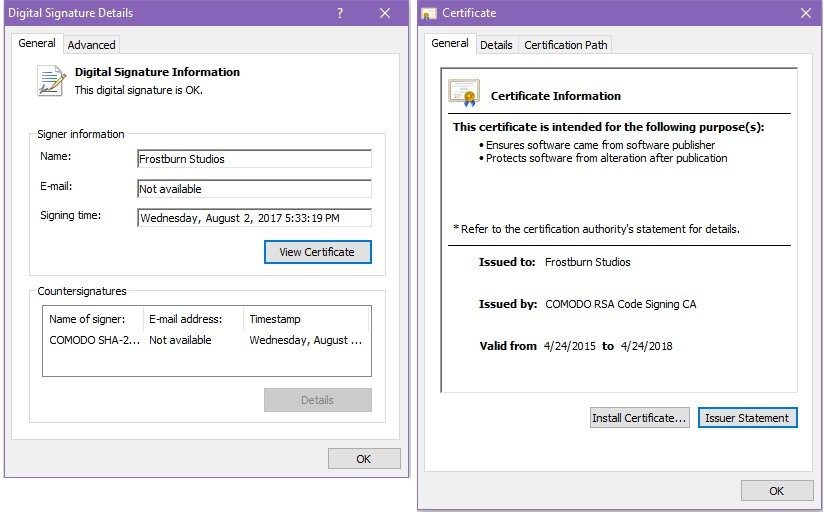
Hackers somehow got their rootkit a Microsoft-issued digital

Online Gamers Beware: Hacker's Microsoft-Signed Rootkit Malware

Microsoft Blocks Iran-linked Lebanese Hackers Targeting Isra

Microsoft Warns of the StrRAT Malware Campaign Targeting Windows

Retliften: How Microsoft Wound Up Certifying Malware - TeamWorx

Please Be Aware About The New Netfilter Driver Rootkits! - The Sec
:max_bytes(150000):strip_icc()/GettyImages-1323900927-d4b8e26cf28f44129e189465fa5a73a8.jpg)
Rootkit Malware Found in Signed Windows Driver
Recomendado para você
-
Top Roblox Leaders Who Creators and Developers Should Know22 dezembro 2024
-
 Hackers steal over $615 million from network running Axie Infinity22 dezembro 2024
Hackers steal over $615 million from network running Axie Infinity22 dezembro 2024 -
 Roblox is letting game creators sell 3D goods, looks to boost revenue22 dezembro 2024
Roblox is letting game creators sell 3D goods, looks to boost revenue22 dezembro 2024 -
 How To Get Rid of Roblox Viruses22 dezembro 2024
How To Get Rid of Roblox Viruses22 dezembro 2024 -
lms-hacker-tools/EV3/lmsdisasm.py at master · ev3dev/lms-hacker22 dezembro 2024
-
 Programmer and hacker geek - Programmer - Sticker22 dezembro 2024
Programmer and hacker geek - Programmer - Sticker22 dezembro 2024 -
Diary of a Roblox Pro: Dragon Pet (Paperback)22 dezembro 2024
-
 Black Hat Hacker T-Shirt : Clothing, Shoes & Jewelry22 dezembro 2024
Black Hat Hacker T-Shirt : Clothing, Shoes & Jewelry22 dezembro 2024 -
Watch LankyBox Ultimate Mishmash Streaming Online22 dezembro 2024
-
 Hacker Find The Hackers Sticker - Hacker Find The Hackers Roblox Find The Hackers - Discover & Share GIFs22 dezembro 2024
Hacker Find The Hackers Sticker - Hacker Find The Hackers Roblox Find The Hackers - Discover & Share GIFs22 dezembro 2024
você pode gostar
-
 FREE! - Desenhos para Colorir para o 2º Ano22 dezembro 2024
FREE! - Desenhos para Colorir para o 2º Ano22 dezembro 2024 -
How the AI Revolution Impacted Chess (1/2)22 dezembro 2024
-
 Yuusha Party ni Kawaii Ko ga Ita node, Kokuhaku shitemita. / Манга22 dezembro 2024
Yuusha Party ni Kawaii Ko ga Ita node, Kokuhaku shitemita. / Манга22 dezembro 2024 -
 Pôster 15ª temporada - Pôster 58 no 1087 - AdoroCinema22 dezembro 2024
Pôster 15ª temporada - Pôster 58 no 1087 - AdoroCinema22 dezembro 2024 -
 Manga Icons Wallpapers - Wallpaper Cave22 dezembro 2024
Manga Icons Wallpapers - Wallpaper Cave22 dezembro 2024 -
 The Callisto Protocol Hardest Difficulty Trophy Can Be Cheesed With Simple Trick22 dezembro 2024
The Callisto Protocol Hardest Difficulty Trophy Can Be Cheesed With Simple Trick22 dezembro 2024 -
 Essential Madeira Islands N.º 87 by Open Media Atlantic - Issuu22 dezembro 2024
Essential Madeira Islands N.º 87 by Open Media Atlantic - Issuu22 dezembro 2024 -
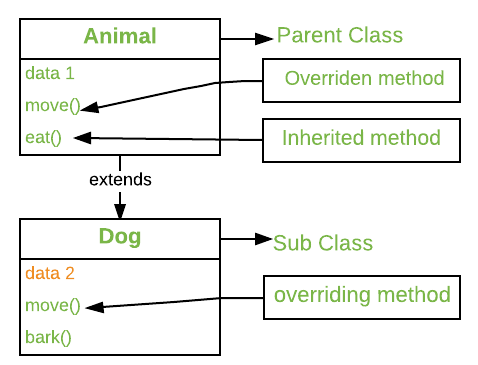 Method Overriding in Python - GeeksforGeeks22 dezembro 2024
Method Overriding in Python - GeeksforGeeks22 dezembro 2024 -
 How to download and install subway surfers in pc22 dezembro 2024
How to download and install subway surfers in pc22 dezembro 2024 -
 Alphabet lore but cursed by Randomguy103940 on DeviantArt22 dezembro 2024
Alphabet lore but cursed by Randomguy103940 on DeviantArt22 dezembro 2024


