Group Behind Cisco Device Hijackings Changes Tactics to Evade
Por um escritor misterioso
Last updated 23 dezembro 2024

Evidence is emerging that the hacking group has updated its techniques to better conceal which Cisco devices have been hijacked.

Group Behind Cisco Device Hijackings Changes Tactics to Evade Detection

High-profile hacks emphasize the threat of social engineering

Abusing Windows Container Isolation Framework to avoid detection by security products

How CISCO got Attacked by Yanluowang Ransomware Gang

Session Hijacking Prevention : Essential Steps, Benefits And Practices - ITU Online

What is BGP Hijacking? Definition and Protection - IDStrong

Bad password policies and how to avoid them

How To Pwn2Own The Cisco RV340 Router

Computer security - Wikipedia
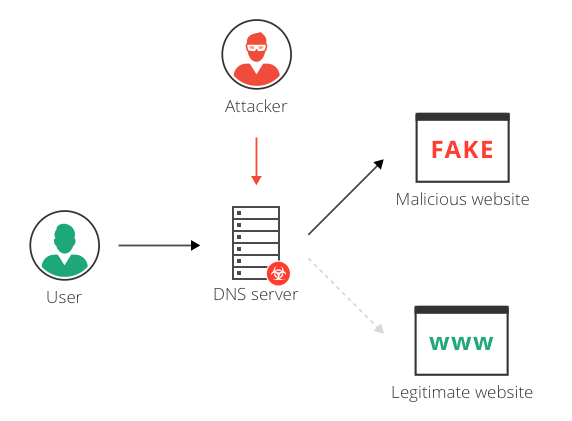
What is a DNS Hijacking, Redirection Attacks Explained
Recomendado para você
-
 Holiday Event, Roblox Evade Wiki23 dezembro 2024
Holiday Event, Roblox Evade Wiki23 dezembro 2024 -
The 1 Billion Visits Update, Roblox Evade Wiki23 dezembro 2024
-
Evade - Roblox23 dezembro 2024
-
 Evade Roblox – What is it, How to play, Codes, and More23 dezembro 2024
Evade Roblox – What is it, How to play, Codes, and More23 dezembro 2024 -
evade controls roblox|TikTok Search23 dezembro 2024
-
 u evade on Steam23 dezembro 2024
u evade on Steam23 dezembro 2024 -
 CapCut_i can save us evade roblox23 dezembro 2024
CapCut_i can save us evade roblox23 dezembro 2024 -
 my son(7) was able to evade the ROBLOX chat block : r/RobloxParents23 dezembro 2024
my son(7) was able to evade the ROBLOX chat block : r/RobloxParents23 dezembro 2024 -
![EVADE] Rebel Fixed - Download Free 3D model by Blender Editer](https://media.sketchfab.com/models/5bb7b5c65c0347d69368edef44c9b9c4/fallbacks/7ae9344ee87a40ebaf2a1d5cd518d1ea/a6bed5c4343b4ed2b8a43ca2b6962f2b.jpeg) EVADE] Rebel Fixed - Download Free 3D model by Blender Editer23 dezembro 2024
EVADE] Rebel Fixed - Download Free 3D model by Blender Editer23 dezembro 2024 -
 EVADE ROBLOX PRO GUIDE PART 2 (TIPS AND TRICKS, GLITCHES, ANGRY23 dezembro 2024
EVADE ROBLOX PRO GUIDE PART 2 (TIPS AND TRICKS, GLITCHES, ANGRY23 dezembro 2024
você pode gostar
-
 Sakamoto desu ga? Stylish Collection: Sakamoto ver. B - My Anime Shelf23 dezembro 2024
Sakamoto desu ga? Stylish Collection: Sakamoto ver. B - My Anime Shelf23 dezembro 2024 -
 Ver Attack on Titan The Final Season (Online) HD by HiGuys920 on DeviantArt23 dezembro 2024
Ver Attack on Titan The Final Season (Online) HD by HiGuys920 on DeviantArt23 dezembro 2024 -
 webSeminovos Volkswagen Saveiro Cross CD 1.6 16V Branco 2021/202223 dezembro 2024
webSeminovos Volkswagen Saveiro Cross CD 1.6 16V Branco 2021/202223 dezembro 2024 -
 Pluto - Rotten Tomatoes23 dezembro 2024
Pluto - Rotten Tomatoes23 dezembro 2024 -
 Dragões Celestiais - Tudo sobre estes personagens de One Piece23 dezembro 2024
Dragões Celestiais - Tudo sobre estes personagens de One Piece23 dezembro 2024 -
/media/movies/covers/2014/07/fairy-tail-arco-5-etherion_t63839.jpg) Fairy Tail (Arco 5: Etherion) - 17 de Maio de 201023 dezembro 2024
Fairy Tail (Arco 5: Etherion) - 17 de Maio de 201023 dezembro 2024 -
 Mario - Games - Coleções23 dezembro 2024
Mario - Games - Coleções23 dezembro 2024 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2023/j/Y/YBtoWyROK4CU4mhJOeag/usa-basketball.png) Lembra de Hay Day? Tudo sobre o jogo estilo 'fazendinha' para celular23 dezembro 2024
Lembra de Hay Day? Tudo sobre o jogo estilo 'fazendinha' para celular23 dezembro 2024 -
 Pizza Tower Mods : MrUnownD3G : Free Download, Borrow, and Streaming : Internet Archive23 dezembro 2024
Pizza Tower Mods : MrUnownD3G : Free Download, Borrow, and Streaming : Internet Archive23 dezembro 2024 -
 Philly Cheese House - Portland, OR Restaurant, Menu + Delivery23 dezembro 2024
Philly Cheese House - Portland, OR Restaurant, Menu + Delivery23 dezembro 2024

