Malware analysis Malicious activity
Por um escritor misterioso
Last updated 08 novembro 2024

Dynamic Malware Analysis in the Modern Era—A State of the Art Survey

Brute Force Attacks: Password Protection
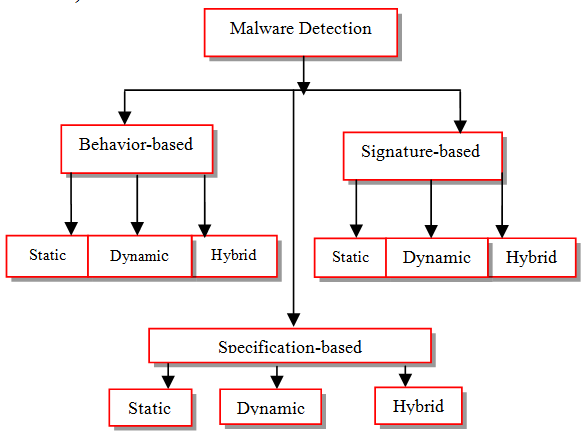
Organization of malware detection techniques (Elhadi et al., 2015

The Guide to Ransomware Solutions in 2023 - Security Boulevard
TryHackMe Hacktivities

TryHackMe Cyber Security Exercises and Labs

Playbook of the Week: Malware Investigation and Response - Palo

Routers Roasting on an Open Firewall: the KV-botnet Investigation

Endpoint Detection and Response, Free - What is EDR Security?

Malware Analysis: Steps & Examples - CrowdStrike
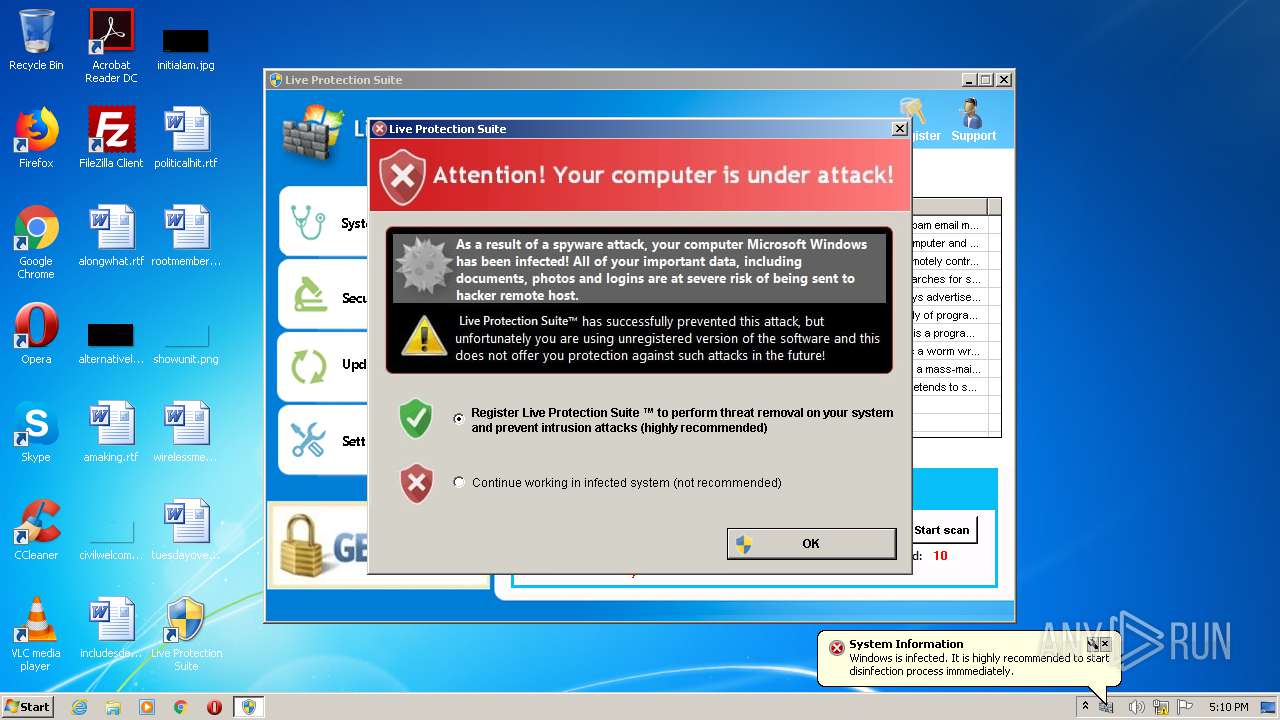
Malware analysis metasploit.bat Malicious activity

PROUD-MAL: static analysis-based progressive framework for deep
Malware analysis 009E9015BDEF9F869B5F15A526D9A1B1 Malicious
Recomendado para você
-
 Roblox Is Bringing Generative AI to Its Gaming Universe08 novembro 2024
Roblox Is Bringing Generative AI to Its Gaming Universe08 novembro 2024 -
 Roblox Studio 0.523 - Download for PC Free08 novembro 2024
Roblox Studio 0.523 - Download for PC Free08 novembro 2024 -
 How to install Roblox Studio on a Chromebook08 novembro 2024
How to install Roblox Studio on a Chromebook08 novembro 2024 -
 Roblox Development08 novembro 2024
Roblox Development08 novembro 2024 -
RNA - #DeveloperNews, Roblox Studio announces Studio08 novembro 2024
-
 Malware analysis Malicious activity08 novembro 2024
Malware analysis Malicious activity08 novembro 2024 -
 Roblox 101: How to Make Your First Game08 novembro 2024
Roblox 101: How to Make Your First Game08 novembro 2024 -
 Roblox Studio Spider Man Web Zip Tool08 novembro 2024
Roblox Studio Spider Man Web Zip Tool08 novembro 2024 -
 How to Add Clothes to NPCs In Roblox STUDIO!08 novembro 2024
How to Add Clothes to NPCs In Roblox STUDIO!08 novembro 2024 -
 Creating your own Web Server for Roblox Integrations [JS08 novembro 2024
Creating your own Web Server for Roblox Integrations [JS08 novembro 2024
você pode gostar
-
 KTM abre as reservas das motocicletas off-road SX e EXC 202308 novembro 2024
KTM abre as reservas das motocicletas off-road SX e EXC 202308 novembro 2024 -
 Hi Blox Fruits folks! I just started on a new account. But I want to make this special The most upvoted comment should be what I do. So, give me good things08 novembro 2024
Hi Blox Fruits folks! I just started on a new account. But I want to make this special The most upvoted comment should be what I do. So, give me good things08 novembro 2024 -
 Sport - London Chessboxing Grandmaster Bash! - Scala. A girl08 novembro 2024
Sport - London Chessboxing Grandmaster Bash! - Scala. A girl08 novembro 2024 -
Hahahahaha ;D08 novembro 2024
-
 Super Kirby Clash, Kirby Wiki08 novembro 2024
Super Kirby Clash, Kirby Wiki08 novembro 2024 -
Blue Protocol Brasil08 novembro 2024
-
 Stranger Things Day' divulga novo trailer da quarta temporada08 novembro 2024
Stranger Things Day' divulga novo trailer da quarta temporada08 novembro 2024 -
 GABINETE GAMEMAX PRECISION COC PRETO • Executive08 novembro 2024
GABINETE GAMEMAX PRECISION COC PRETO • Executive08 novembro 2024 -
 Revenue and Usage Statistics (2023) - Business of Apps08 novembro 2024
Revenue and Usage Statistics (2023) - Business of Apps08 novembro 2024 -
 The Witcher - Geralt of Rivia (Henry Cavill) 1/4 Scale Statue08 novembro 2024
The Witcher - Geralt of Rivia (Henry Cavill) 1/4 Scale Statue08 novembro 2024


