Malware analysis Malicious activity
Por um escritor misterioso
Last updated 10 novembro 2024

TryHackMe Hacktivities

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Protecting Your Network from Cyber Attacks
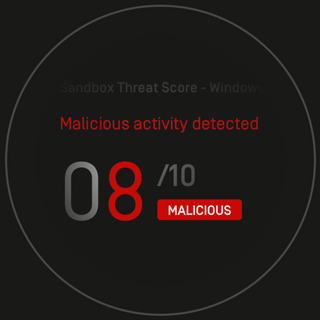
MetaDefender Cloud Advanced threat prevention and detection

Malware Analysis: Steps & Examples - CrowdStrike
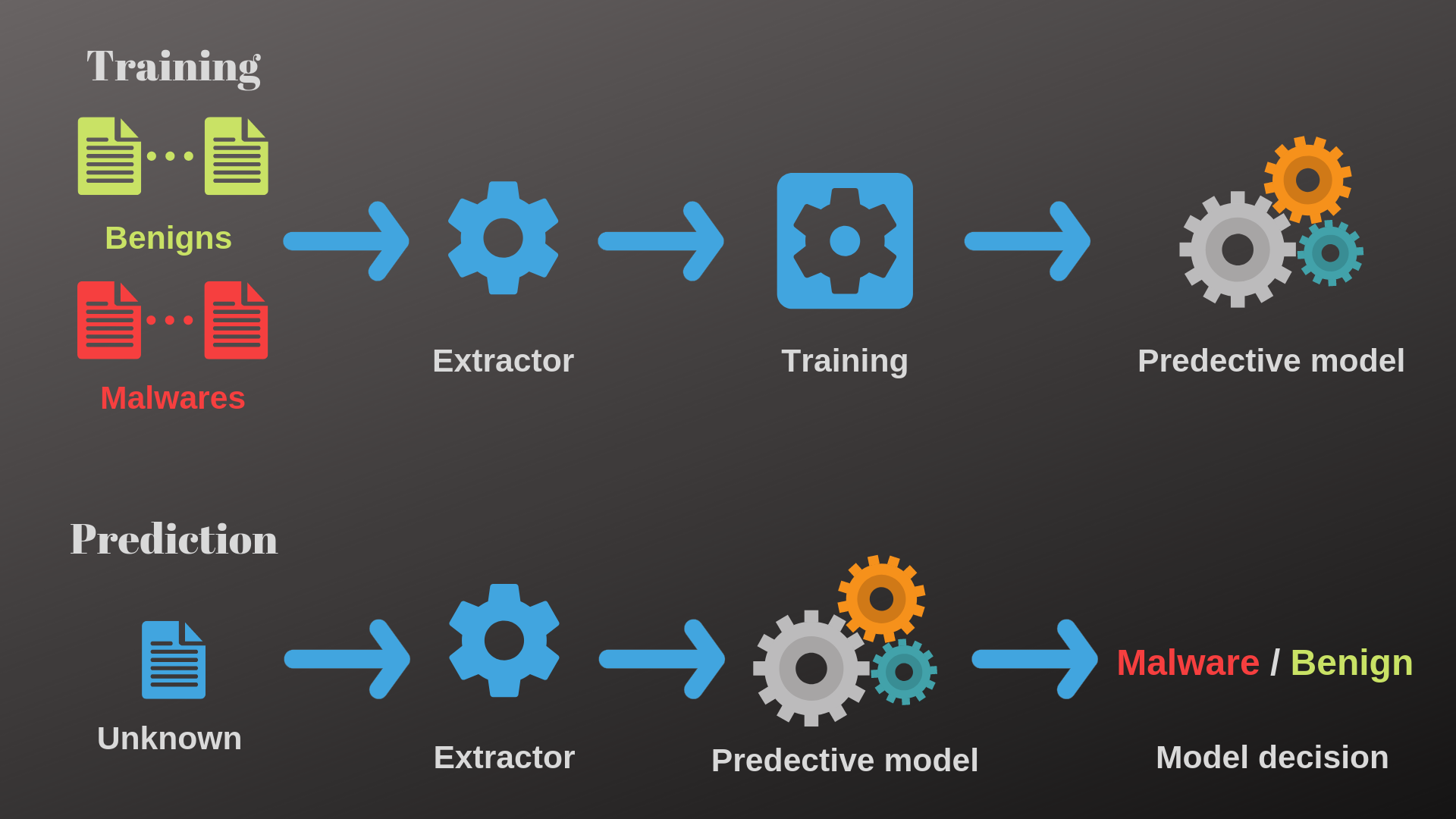
Feature Extraction and Detection of Malwares Using Machine Learning

Interactive Online Malware Sandbox

Malware analysis Program_Install_and_Uninstall Malicious activity

A detailed analysis of the Menorah malware used by APT34
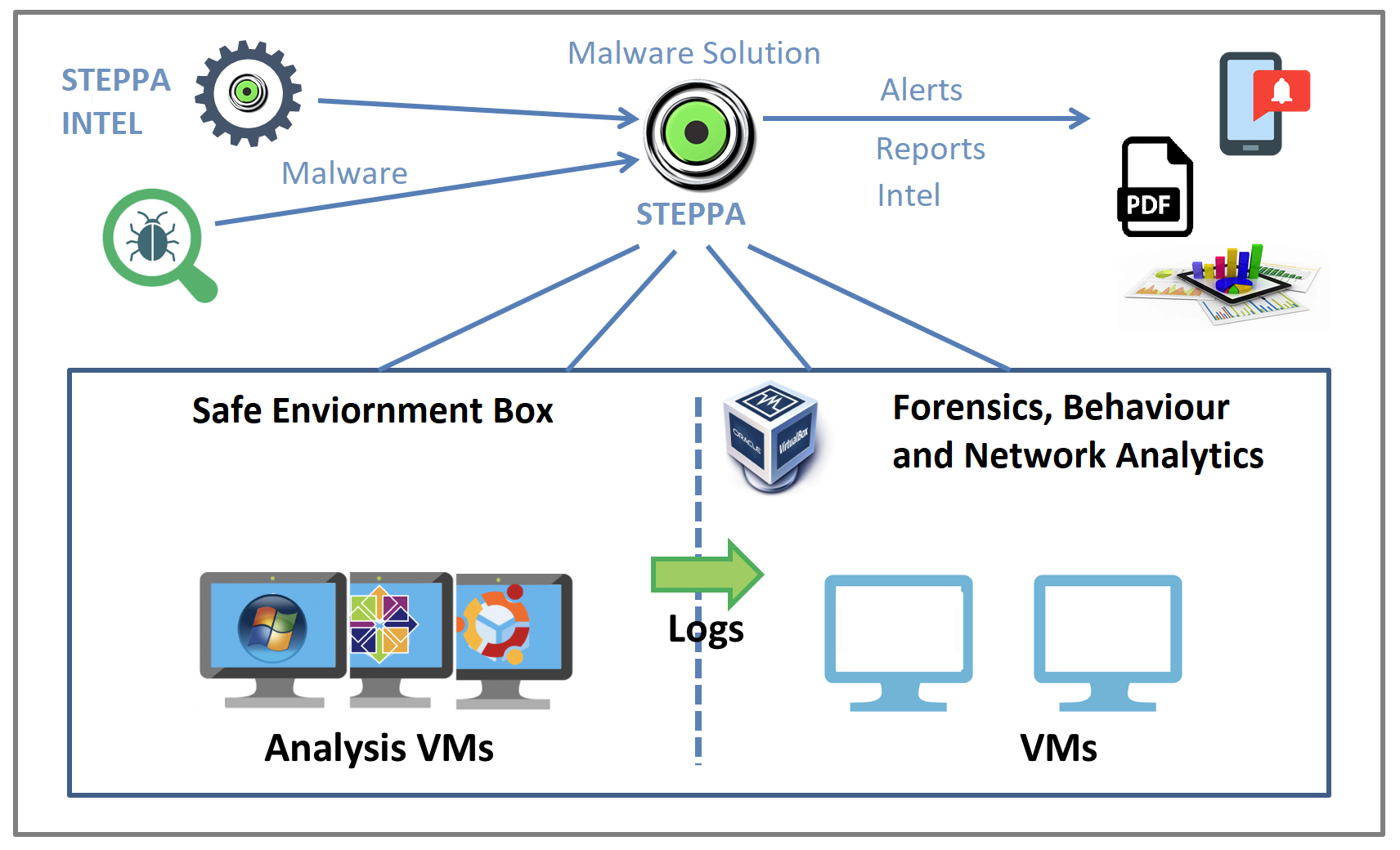
Malware Analysis Solution: Analyze, Detect, and Protect

ReversingLabs Malware Lab: Detect, classify, analyze, and respond to malicious files - Help Net Security
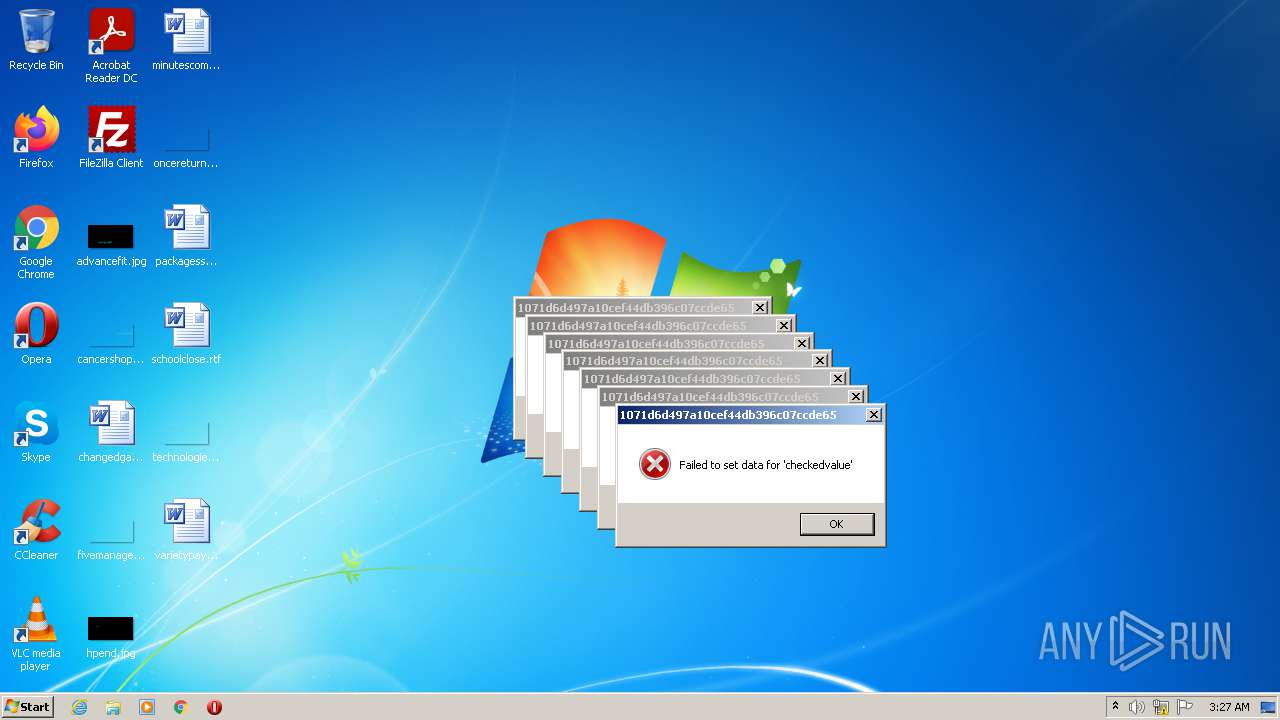
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity
Krebs on Security – In-depth security news and investigation
Recomendado para você
-
 List of (Blox.Land) blox land promo codes (December 2023)10 novembro 2024
List of (Blox.Land) blox land promo codes (December 2023)10 novembro 2024 -
 Is Blox.land a scam or a legit Robux generator? - Quora10 novembro 2024
Is Blox.land a scam or a legit Robux generator? - Quora10 novembro 2024 -
 Blox.land Login10 novembro 2024
Blox.land Login10 novembro 2024 -
Earn R$!10 novembro 2024
-
how to win the giveaway in bloxland|TikTok Search10 novembro 2024
-
 Blox.land (@Bloxland4) / X10 novembro 2024
Blox.land (@Bloxland4) / X10 novembro 2024 -
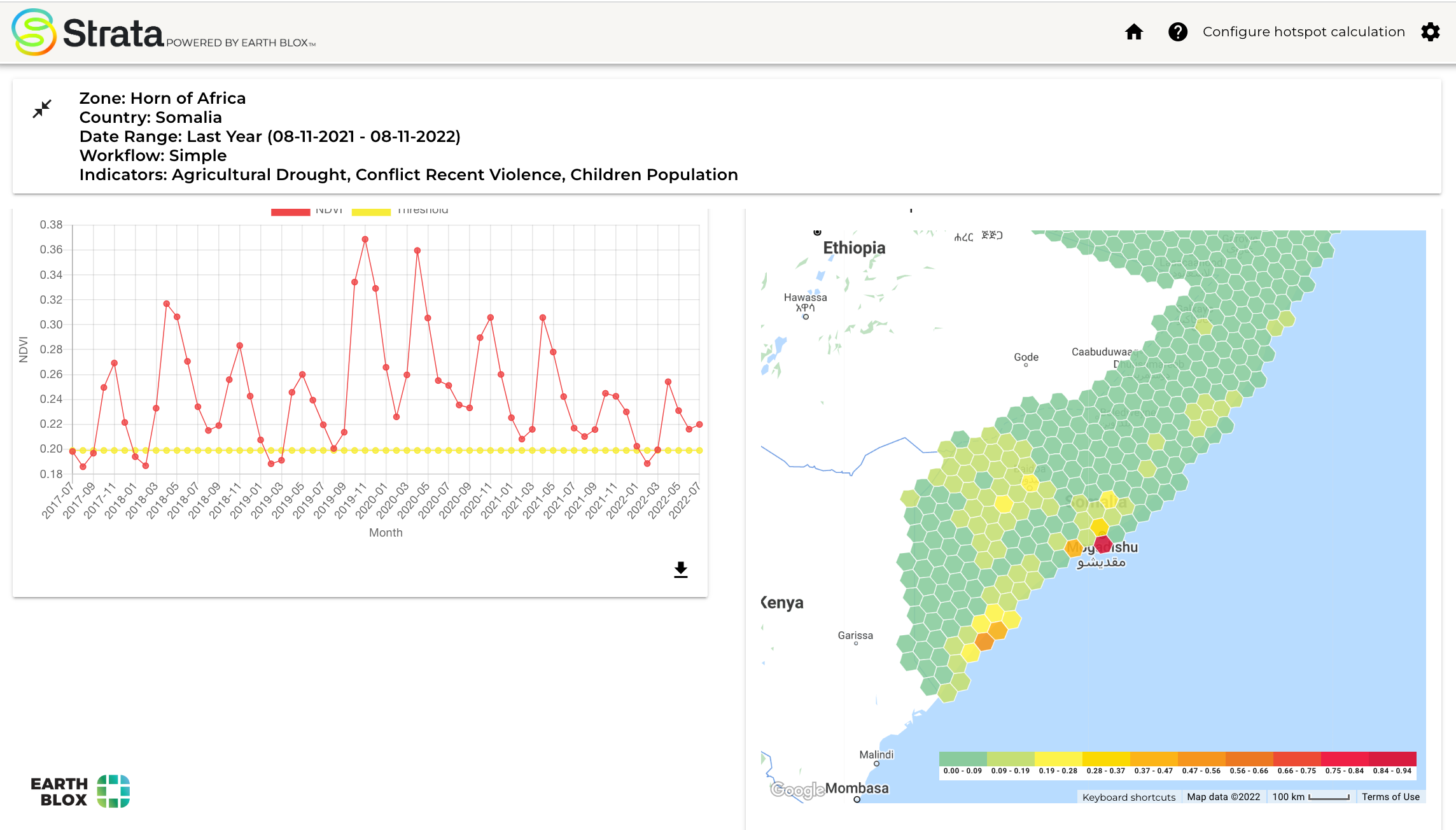 Strata: UNEP's Earth Stress Monitor, Blog10 novembro 2024
Strata: UNEP's Earth Stress Monitor, Blog10 novembro 2024 -
 Proposed framework could change city's future land use map implementation10 novembro 2024
Proposed framework could change city's future land use map implementation10 novembro 2024 -
Bloxland Promo Codes 202410 novembro 2024
-
 Florissant seeks park land swap with housing developer10 novembro 2024
Florissant seeks park land swap with housing developer10 novembro 2024
você pode gostar
-
 Camisa Naruto - Símbolo AKATSUKI10 novembro 2024
Camisa Naruto - Símbolo AKATSUKI10 novembro 2024 -
 Download Bubble Puzzle 97 (Windows) - My Abandonware10 novembro 2024
Download Bubble Puzzle 97 (Windows) - My Abandonware10 novembro 2024 -
![Toy Defense Codes Wiki Roblox [December 2023] - MrGuider](https://www.mrguider.org/wp-content/uploads/2023/05/Toy-Defense-Codes-Wiki-Roblox.jpg) Toy Defense Codes Wiki Roblox [December 2023] - MrGuider10 novembro 2024
Toy Defense Codes Wiki Roblox [December 2023] - MrGuider10 novembro 2024 -
Anime Stickers for WhatsApp - Izinhlelo zokusebenza ku-Google Play10 novembro 2024
-
 Warframe: Updates - PlayStation Sisters of Parvos: Update 30.510 novembro 2024
Warframe: Updates - PlayStation Sisters of Parvos: Update 30.510 novembro 2024 -
 Nova saga: Dragões: Defensores de Berk, Dragões10 novembro 2024
Nova saga: Dragões: Defensores de Berk, Dragões10 novembro 2024 -
 Assistir Kaguya-sama wa Kokurasetai Dublado Episodio 8 Online10 novembro 2024
Assistir Kaguya-sama wa Kokurasetai Dublado Episodio 8 Online10 novembro 2024 -
 Diplo, Jessie Murph, Polo G - Heartbroken (Official Video)10 novembro 2024
Diplo, Jessie Murph, Polo G - Heartbroken (Official Video)10 novembro 2024 -
 CLICANDO E COMPRANDO Jogo Cartas Truco Maluco 54 Cartas Baralho Truuco Marcador10 novembro 2024
CLICANDO E COMPRANDO Jogo Cartas Truco Maluco 54 Cartas Baralho Truuco Marcador10 novembro 2024 -
GM Authority10 novembro 2024


