Utilizing Morse Code to Evade Signature Based Detection Systems
Por um escritor misterioso
Last updated 22 dezembro 2024


The average loading time for news sites using CovertCast over .

BlueNoroff Hackers Utilize ObjCShellz Malware to Create Backdoors on Macs
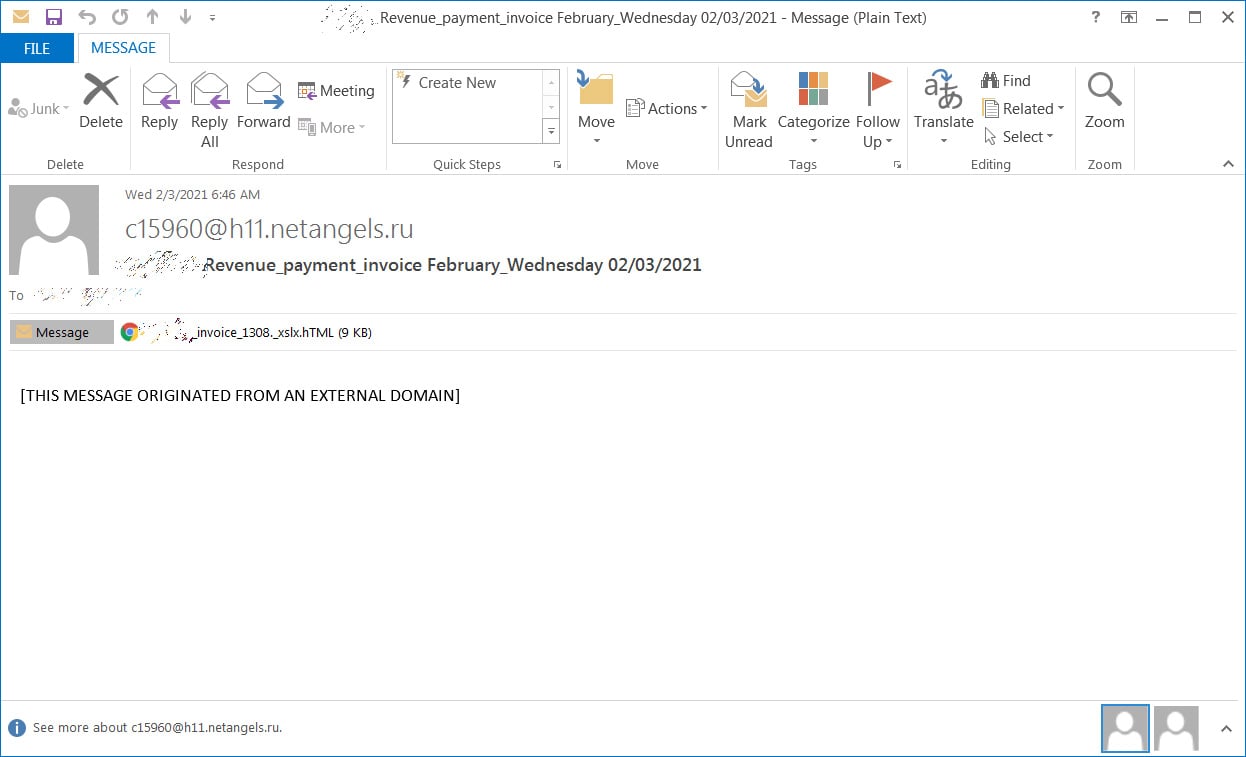
New phishing attack uses Morse code to hide malicious URLs
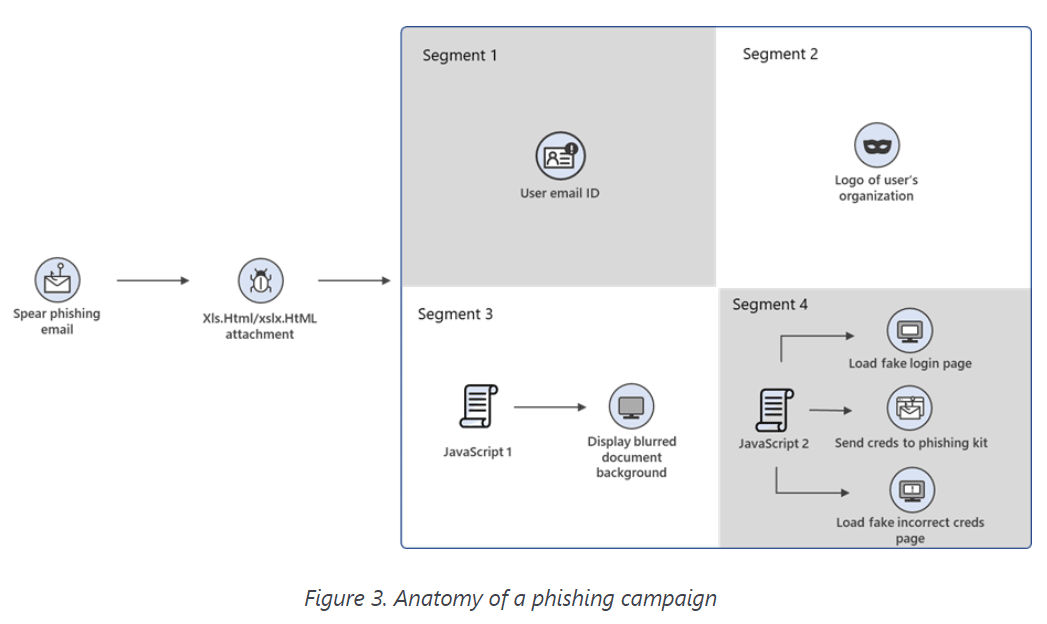
Phishing Campaign Used Morse Code to Evade Detection: Microsoft

Provenance-based Intrusion Detection Systems: A Survey

Hackers are Using Morse Code to Avoid Detection - IDStrong
Gels, Free Full-Text

Attackers use Morse code, other encryption methods in evasive phishing campaign

Phishing Campaign Used Morse Code to Evade Detection: Microsoft

– . . . Security Focus . . .
How is it possible to communicate in Morse Code by knocking or tapping, when each tap sounds identical? - Quora
Symmetry, Free Full-Text

Public Secret Message - TV Tropes

Flax Typhoon Hackers Employ Advanced Tactics, Leveraging LOLBins for Stealthy Operations, Microsoft Reports

The Art & Science of Threat Hunting - A Guide to Preventing Cyber Attacks
Recomendado para você
-
 Roblox Murder Mystery 2 Codes for July 2023: Free knives22 dezembro 2024
Roblox Murder Mystery 2 Codes for July 2023: Free knives22 dezembro 2024 -
 Evolution Evade Codes - Try Hard Guides22 dezembro 2024
Evolution Evade Codes - Try Hard Guides22 dezembro 2024 -
 Create a Roblox Evade map list 2023 Tier List - TierMaker22 dezembro 2024
Create a Roblox Evade map list 2023 Tier List - TierMaker22 dezembro 2024 -
 All Evade Codes For November 2023 - GameRiv22 dezembro 2024
All Evade Codes For November 2023 - GameRiv22 dezembro 2024 -
 NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES22 dezembro 2024
NEW* ALL WORKING CODES FOR EVADE IN MARCH 2023! ROBLOX EVADE CODES22 dezembro 2024 -
 DragonSpark Attacks Evade Detection with SparkRAT and Golang22 dezembro 2024
DragonSpark Attacks Evade Detection with SparkRAT and Golang22 dezembro 2024 -
 Attackers use dynamic code loading to bypass Google Play store's22 dezembro 2024
Attackers use dynamic code loading to bypass Google Play store's22 dezembro 2024 -
 Codes d'évasion (novembre 2022) – Guides de jeu professionnels22 dezembro 2024
Codes d'évasion (novembre 2022) – Guides de jeu professionnels22 dezembro 2024 -
Data Encoder Crypter22 dezembro 2024
-
 College Presidents Under Fire After Dodging Questions About22 dezembro 2024
College Presidents Under Fire After Dodging Questions About22 dezembro 2024
você pode gostar
-
The Most Famous Football Player From Every State22 dezembro 2024
-
 Error Glitch - Sad Anime Girl Art Board Print for Sale by LEVANKOV Items22 dezembro 2024
Error Glitch - Sad Anime Girl Art Board Print for Sale by LEVANKOV Items22 dezembro 2024 -
WrestleBR on X: 🚨 WWE acredita que o NXT consistemente superará o AEW Dynamite em 2024 Clique na imagem para ler 👇🏾 / X22 dezembro 2024
-
 7 Jogos de Celular Extremamente Viciantes para Crianças22 dezembro 2024
7 Jogos de Celular Extremamente Viciantes para Crianças22 dezembro 2024 -
 The Last Of Us Part 2 - Biggest Story Spoilers22 dezembro 2024
The Last Of Us Part 2 - Biggest Story Spoilers22 dezembro 2024 -
 Download Code Geass C.C. Anime Wallpaper Wallpaper22 dezembro 2024
Download Code Geass C.C. Anime Wallpaper Wallpaper22 dezembro 2024 -
 Mario Kart 8 Deluxe (Nintendo Switch) (European22 dezembro 2024
Mario Kart 8 Deluxe (Nintendo Switch) (European22 dezembro 2024 -
 Arsenal Paranormal ✨ em 202322 dezembro 2024
Arsenal Paranormal ✨ em 202322 dezembro 2024 -
Measure Your Ring Size - Silvery22 dezembro 2024
-
 How do i revert back to the old draggers - Building Support - Developer Forum22 dezembro 2024
How do i revert back to the old draggers - Building Support - Developer Forum22 dezembro 2024

