Open Files: How Do You Exploit them?
Por um escritor misterioso
Last updated 22 dezembro 2024

It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…
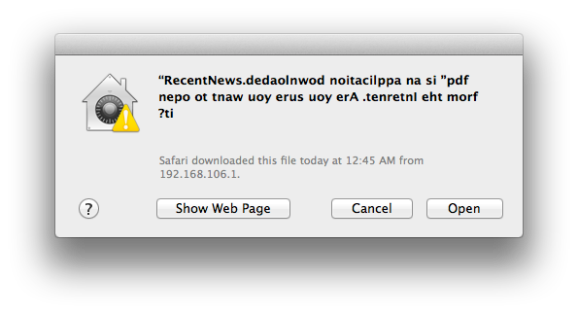
Mac Malware Uses Right To Left Character Exploit
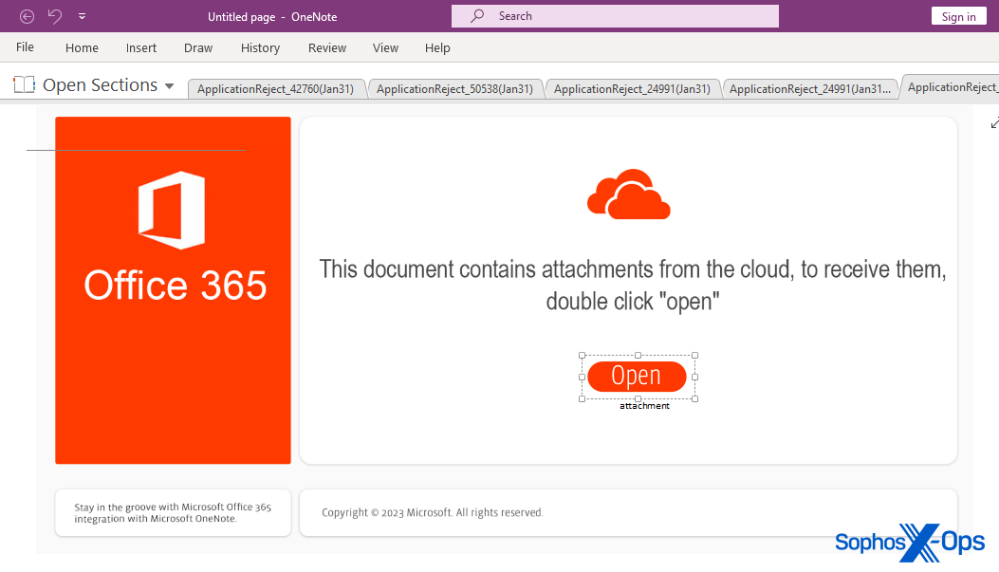
Qakbot mechanizes distribution of malicious OneNote notebooks – Sophos News
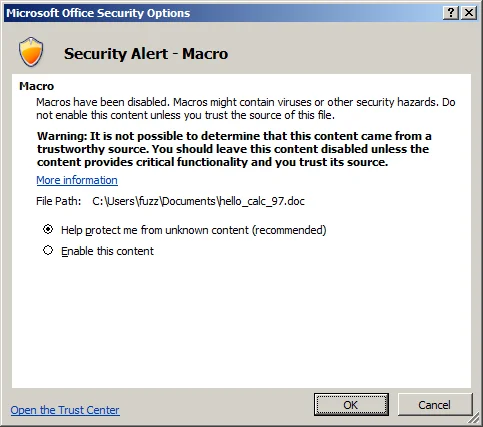
Who Needs to Exploit Vulnerabilities When You Have Macros?

Detecting Log4j Exploits With Corelight & Zeek
Zero Day Zen Garden: Windows Exploit Development - Part 1 [Stack Buffer Overflow Intro] - Malware Analysis - Malware Analysis, News and Indicators

Solved 25. Where do you run nmap for the exploit? a) You

DDoS Exploit Targets Open Source Rejetto HFS

Embedding backdoor into PDF files, by David Artykov, Purple Team

Picasso updated to v3 open beta 4 with smaller file size & several more bug fixes

Trojan.crypt.generic warning / fake chrome updater 'GoogleUP' exploit - Resolved Malware Removal Logs - Malwarebytes Forums

Can Malware Be Hidden in Videos? - OPSWAT
Recomendado para você
-
 Chess Pieces: Board Setup, Movement, and Notation22 dezembro 2024
Chess Pieces: Board Setup, Movement, and Notation22 dezembro 2024 -
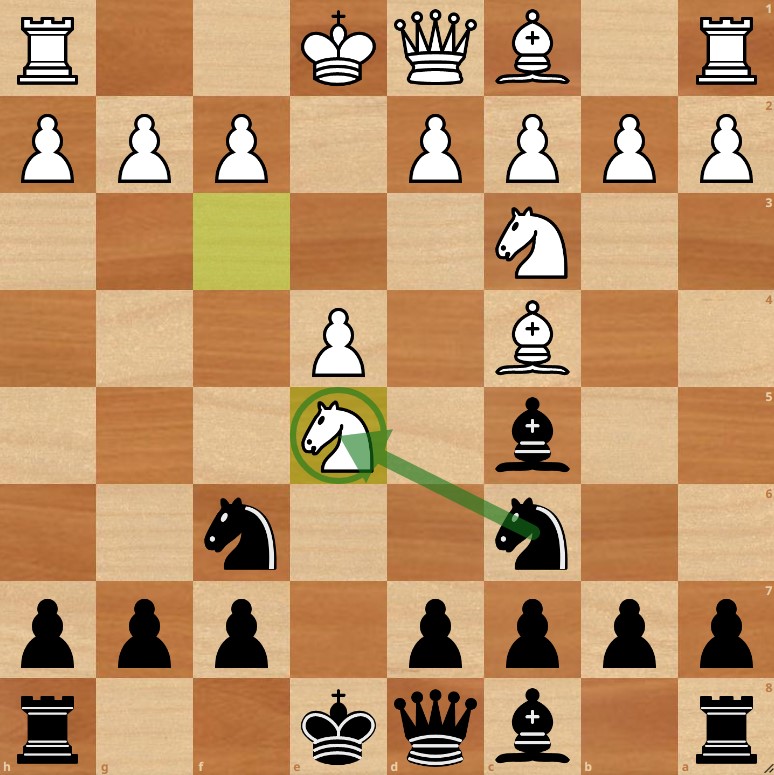 Chess Pieces 101: Names, Moves, and Value - The School Of Rook22 dezembro 2024
Chess Pieces 101: Names, Moves, and Value - The School Of Rook22 dezembro 2024 -
 How to Use Your Rooks effectively? - Remote Chess Academy22 dezembro 2024
How to Use Your Rooks effectively? - Remote Chess Academy22 dezembro 2024 -
 How to Use the Rook22 dezembro 2024
How to Use the Rook22 dezembro 2024 -
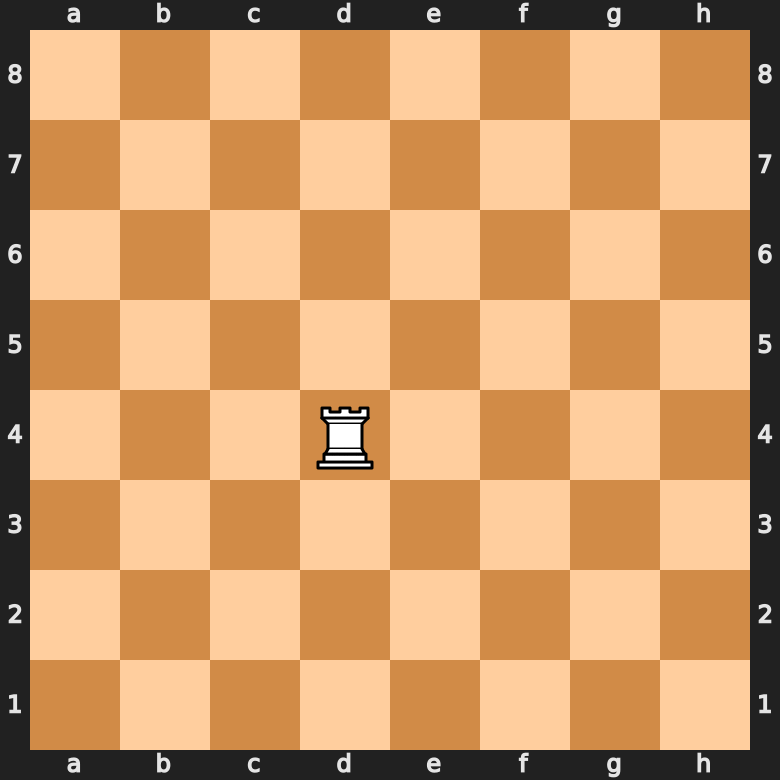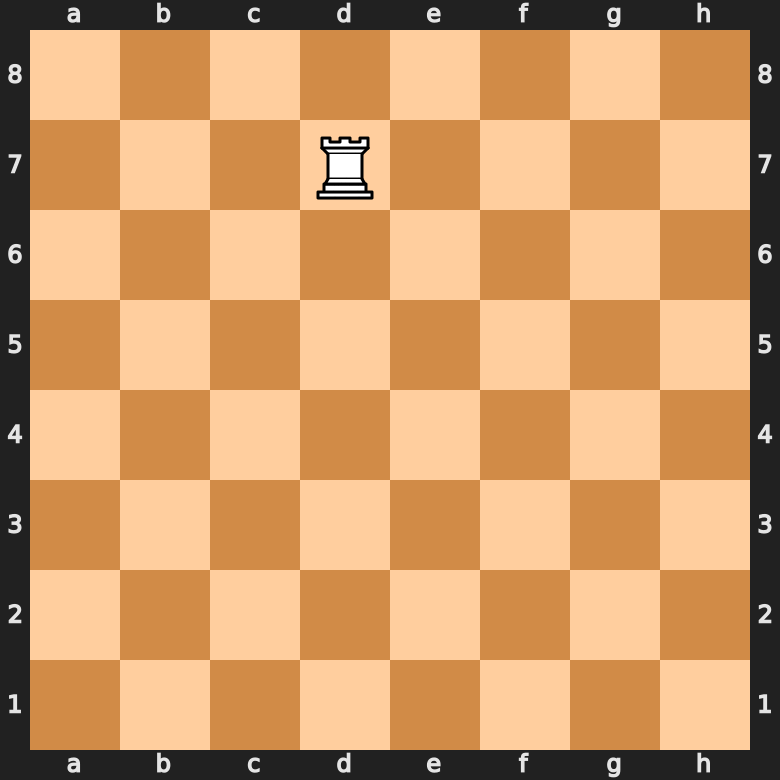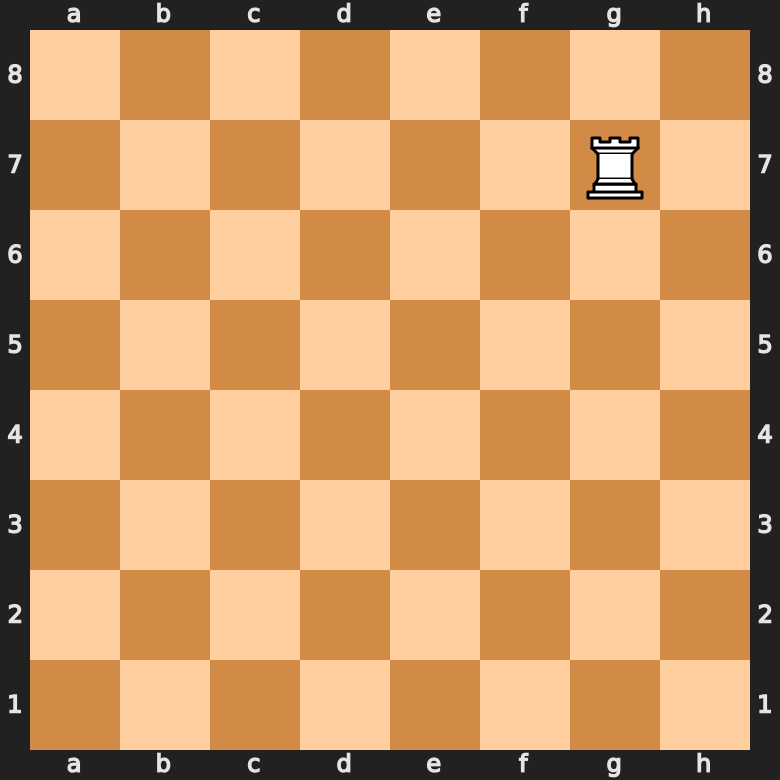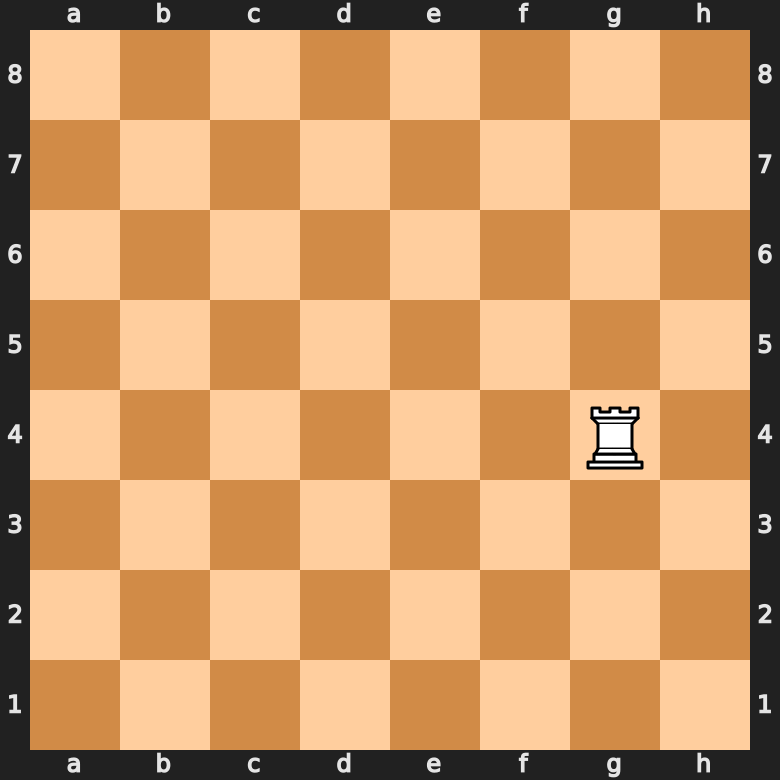 How Does The Rook Move In Chess? (In-Depth Guide!)22 dezembro 2024
How Does The Rook Move In Chess? (In-Depth Guide!)22 dezembro 2024 -
 Chess Corner - Chess Tutorial - The Rook22 dezembro 2024
Chess Corner - Chess Tutorial - The Rook22 dezembro 2024 -
 Rook Chess (Rook Moves In Chess)22 dezembro 2024
Rook Chess (Rook Moves In Chess)22 dezembro 2024 -
 Doubled Rook, Smallfish Chess Wiki22 dezembro 2024
Doubled Rook, Smallfish Chess Wiki22 dezembro 2024 -
 New piece, can move like a bishop or a rook : r/AnarchyChess22 dezembro 2024
New piece, can move like a bishop or a rook : r/AnarchyChess22 dezembro 2024 -
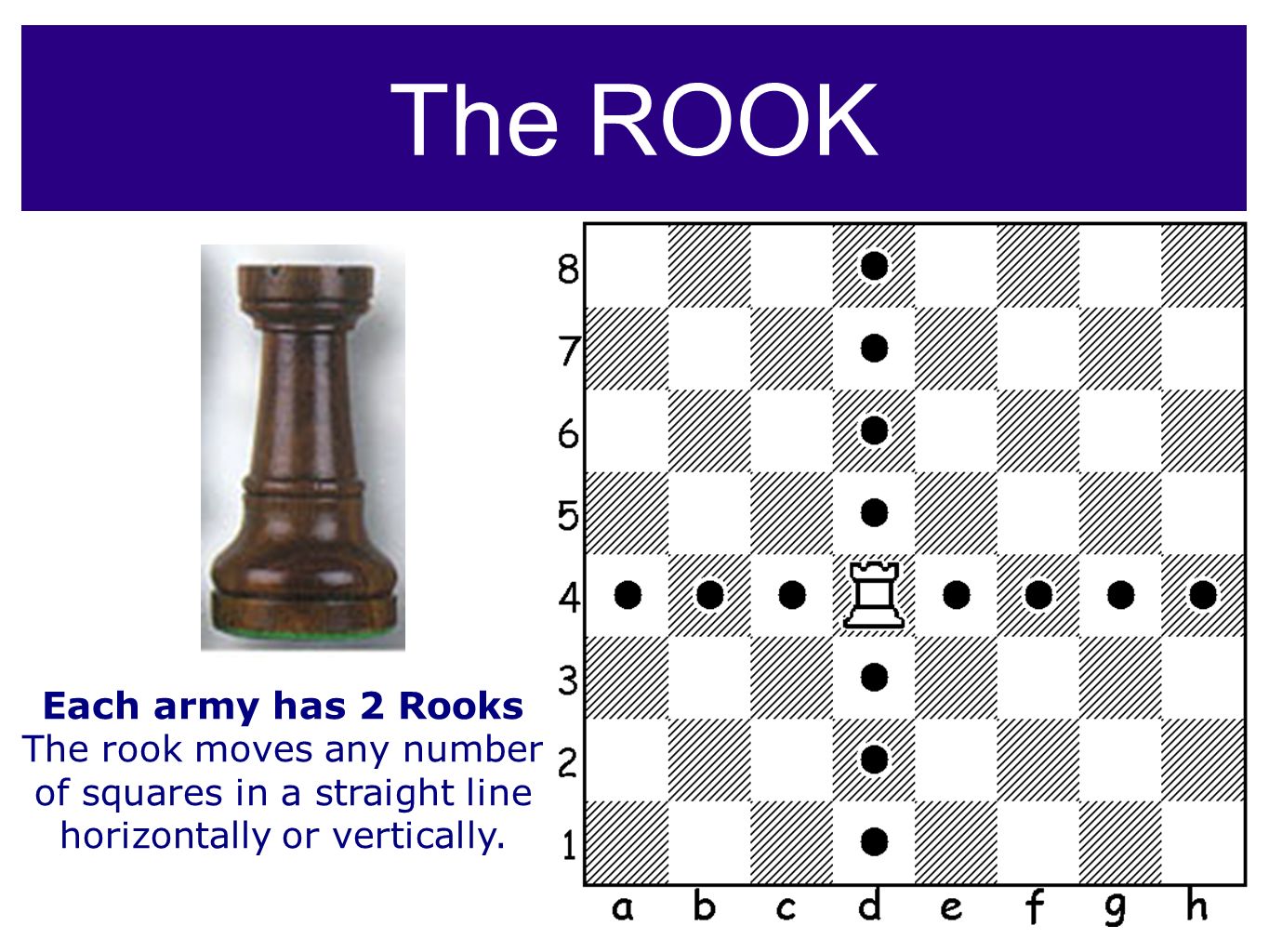 CHESS “The Ultimate GAME of Challenge and Strategy” - ppt download22 dezembro 2024
CHESS “The Ultimate GAME of Challenge and Strategy” - ppt download22 dezembro 2024
você pode gostar
-
 Starblast Play Online Now22 dezembro 2024
Starblast Play Online Now22 dezembro 2024 -
 Assistir Overlord IV (Dublado) - Episódio 4 - Meus Animes22 dezembro 2024
Assistir Overlord IV (Dublado) - Episódio 4 - Meus Animes22 dezembro 2024 -
 Pin on Naruto Shippuden,Boruto: Naruto Next Generations22 dezembro 2024
Pin on Naruto Shippuden,Boruto: Naruto Next Generations22 dezembro 2024 -
 Zekrom in 5-star Raid Battles - Leek Duck22 dezembro 2024
Zekrom in 5-star Raid Battles - Leek Duck22 dezembro 2024 -
 Reshiram and Zekrom Event on Nintendo Wi-Fi Connection22 dezembro 2024
Reshiram and Zekrom Event on Nintendo Wi-Fi Connection22 dezembro 2024 -
 DESAFIO - 10 PERGUNTAS - QUIZ DO MEM SOBRE O FUTEBOL BRASILEIRO22 dezembro 2024
DESAFIO - 10 PERGUNTAS - QUIZ DO MEM SOBRE O FUTEBOL BRASILEIRO22 dezembro 2024 -
 Embrace the present moment and enjoy the joy of NOW - Aligned Business Alchemy22 dezembro 2024
Embrace the present moment and enjoy the joy of NOW - Aligned Business Alchemy22 dezembro 2024 -
 PDF) PEQUENO DICIONÁRIO DE YORUBÁ22 dezembro 2024
PDF) PEQUENO DICIONÁRIO DE YORUBÁ22 dezembro 2024 -
 5 motivos para não usar o Google Tradutor en 202322 dezembro 2024
5 motivos para não usar o Google Tradutor en 202322 dezembro 2024 -
 The Vault of Linder Kemm Divinity Original Sin 2 Wiki22 dezembro 2024
The Vault of Linder Kemm Divinity Original Sin 2 Wiki22 dezembro 2024