SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Last updated 22 dezembro 2024

As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.
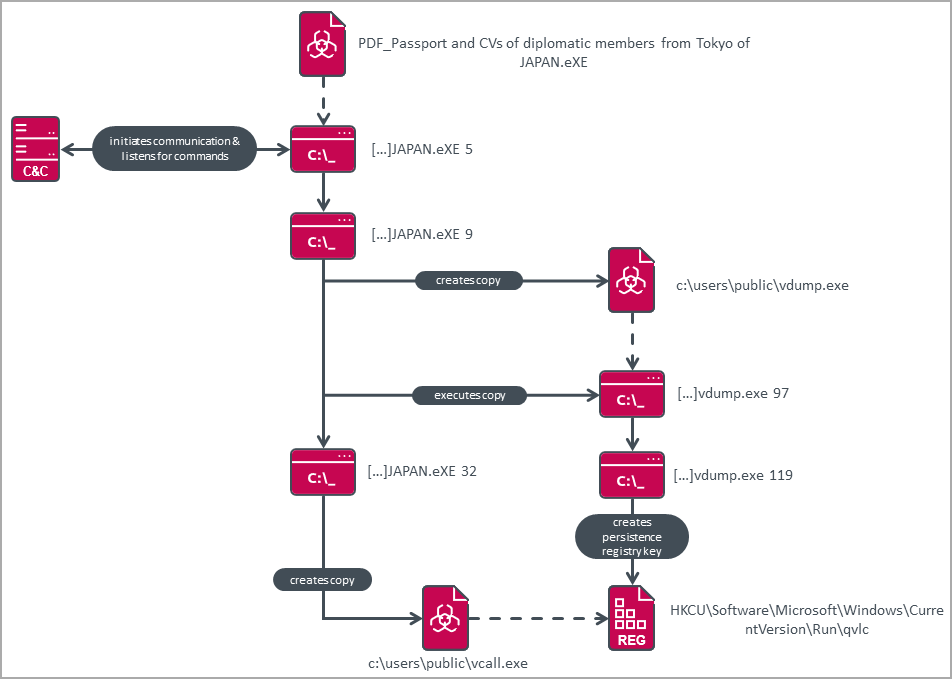
Chinese hackers use new custom backdoor to evade detection

Chinese State-Sponsored Hackers Evade Common Cybersecurity Tools
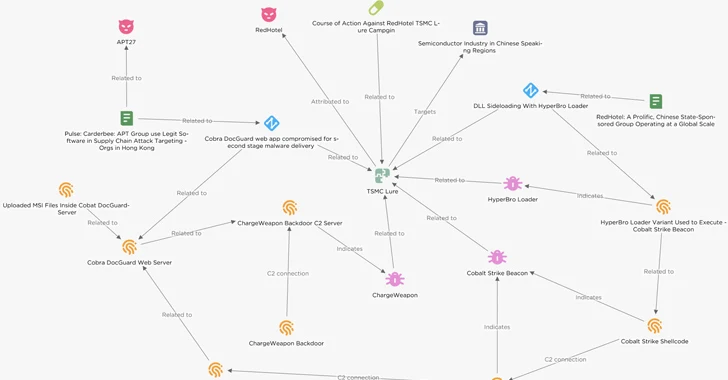
Cobalt Strike, Breaking Cybersecurity News

Hack Like a Pro: How to Evade AV Detection with Veil-Evasion « Null Byte :: WonderHowTo
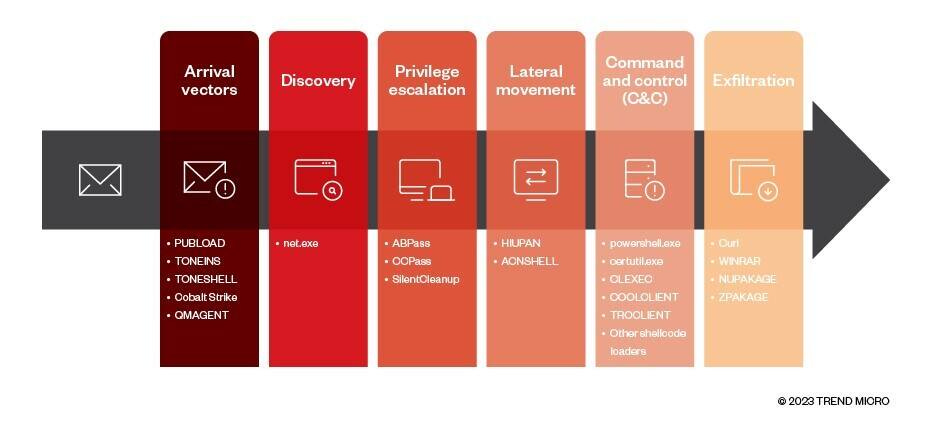
Bluepurple Pulse: week ending March 26th - by Ollie

Spixnet - Instagram fined €405m over children's data privacy

Simjacker
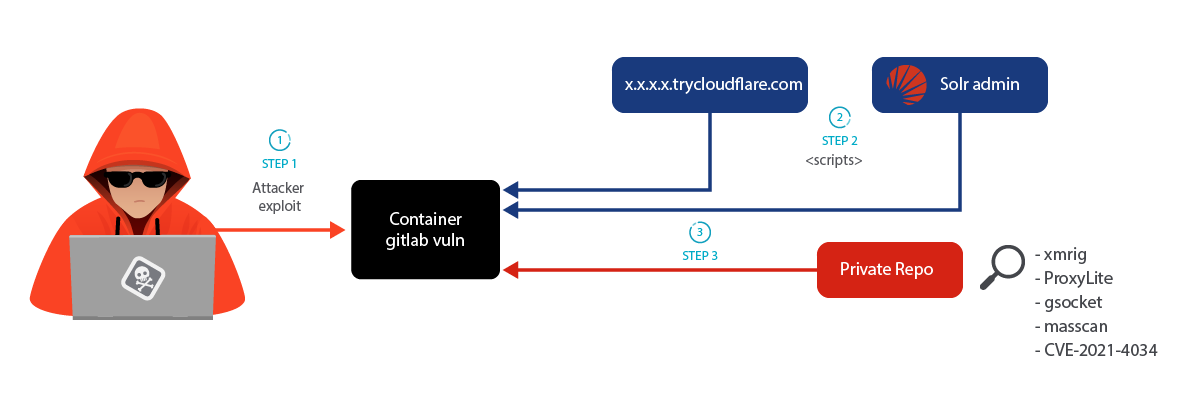
LABRAT: Stealthy Cryptojacking and Proxyjacking Campaign Targeting GitLab – Sysdig

Chinese Silkloader cyber attack tool falls into Russian hands

Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection

Cl0p hits Hitachi Energy. TikTok surveillance investigated. BreachForums arrest. Hacktivists, torrents in the hybrid war.

Post #11303 — Xpykerz (@Xpykerz)

Chinese Hackers Use New Cryptojacking Tactics to Evade Detection

Black Arrow Cyber Consulting — Black Arrow Cyber Threat Briefing 17 March 2023
Recomendado para você
-
 Evade Roblox Hack: Money Farm, AFK Farm, ESP & More22 dezembro 2024
Evade Roblox Hack: Money Farm, AFK Farm, ESP & More22 dezembro 2024 -
![Evade [AutoRespawn, Esp] Scripts](https://rbxscript.com/images/-KAgv5dirUs-image.jpg) Evade [AutoRespawn, Esp] Scripts22 dezembro 2024
Evade [AutoRespawn, Esp] Scripts22 dezembro 2024 -
evade script|TikTok Search22 dezembro 2024
-
![🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)](https://i.ytimg.com/vi/m_qS5tSnnts/maxresdefault.jpg) 🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)22 dezembro 2024
🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)22 dezembro 2024 -
 New ESXiArgs ransomware variant can evade CISA's recovery script22 dezembro 2024
New ESXiArgs ransomware variant can evade CISA's recovery script22 dezembro 2024 -
 Roblox Evade Script: Exp & Money Farm » Download Free Cheats22 dezembro 2024
Roblox Evade Script: Exp & Money Farm » Download Free Cheats22 dezembro 2024 -
 OP) ROBLOX Evade Script - 2022, Auto Jump / ESP22 dezembro 2024
OP) ROBLOX Evade Script - 2022, Auto Jump / ESP22 dezembro 2024 -
 Enums. Using enums are a really useful way to…22 dezembro 2024
Enums. Using enums are a really useful way to…22 dezembro 2024 -
 NEW* EVADE 🍀 HACK GUI 🔥 BEST MONEY FARM, GODMODE, FAST REVIVE22 dezembro 2024
NEW* EVADE 🍀 HACK GUI 🔥 BEST MONEY FARM, GODMODE, FAST REVIVE22 dezembro 2024 -
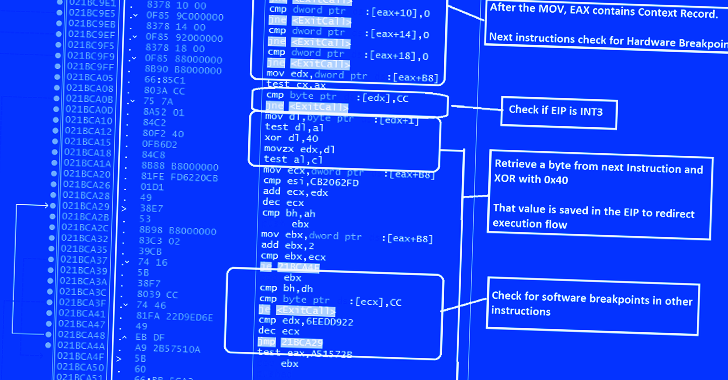 GuLoader Malware Utilizing New Techniques to Evade Security Software22 dezembro 2024
GuLoader Malware Utilizing New Techniques to Evade Security Software22 dezembro 2024
você pode gostar
-
Domestic na Kanojo Episode 8 Discussion (100 - ) - Forums22 dezembro 2024
-
 Doll House Design & Decoration 2: Girls House Game Game for Android - Download22 dezembro 2024
Doll House Design & Decoration 2: Girls House Game Game for Android - Download22 dezembro 2024 -
 VAMOS ASSISTIR - JACKIE CHAN NA SUA MELHOR LUTA.22 dezembro 2024
VAMOS ASSISTIR - JACKIE CHAN NA SUA MELHOR LUTA.22 dezembro 2024 -
 Ateliers Do It Yourself : pourquoi ont-ils autant de succès ?22 dezembro 2024
Ateliers Do It Yourself : pourquoi ont-ils autant de succès ?22 dezembro 2024 -
 Desapego Games - Roblox > Conta antiga do roblox com mais de 4000 robux gastos e histórico em vários jogos22 dezembro 2024
Desapego Games - Roblox > Conta antiga do roblox com mais de 4000 robux gastos e histórico em vários jogos22 dezembro 2024 -
 Arminha de gel Bolinha Orbeez Eletrica Automatica Brinquedo na22 dezembro 2024
Arminha de gel Bolinha Orbeez Eletrica Automatica Brinquedo na22 dezembro 2024 -
 Horizon games official site22 dezembro 2024
Horizon games official site22 dezembro 2024 -
 Getsuyoubi no Tawawa - IntoxiAnime22 dezembro 2024
Getsuyoubi no Tawawa - IntoxiAnime22 dezembro 2024 -
 LOS ANGELES, JUL 29 - Toby Regbo, Torrance Coombs arrives at the 2013 CBS TCA Summer Party at the private location on July 29, 2013 in Beverly Hills, CA 14122245 Stock Photo at Vecteezy22 dezembro 2024
LOS ANGELES, JUL 29 - Toby Regbo, Torrance Coombs arrives at the 2013 CBS TCA Summer Party at the private location on July 29, 2013 in Beverly Hills, CA 14122245 Stock Photo at Vecteezy22 dezembro 2024 -
Ravelry: Green (Rainbow Friends) pattern by Karol Torres Handmade22 dezembro 2024


