To Be (Enumerated) Or Not To Be
Por um escritor misterioso
Last updated 21 setembro 2024
Are user enumeration vulnerabilities a real security concern? User enumeration is when an application reveals whether a user exists to other users.

PLANS FOR THE 1980 CENSUS Counting the People in 1980: AN

Enumerated Powers Song

What Is Enumeration in Ethical Hacking? [Updated 2023]

Add an Enumeration to a Stereotype

The 1880 U.S. Census: A Closer Look at the Even Better Census
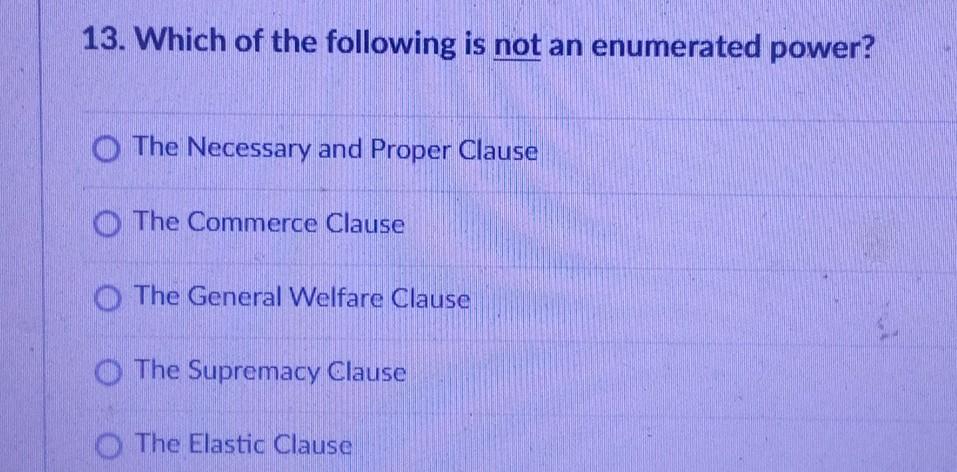
Solved 13. Which of the following is not an enumerated
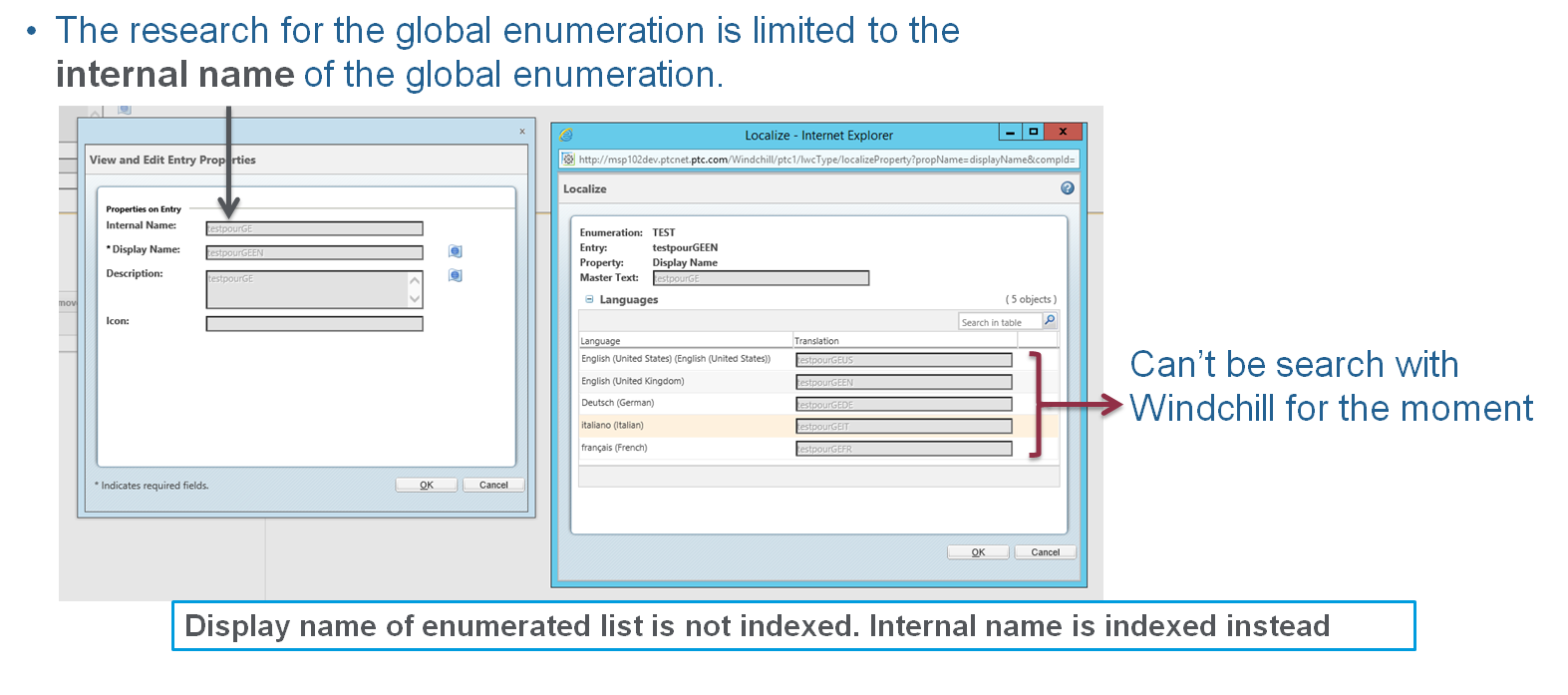
Extend SolR capabilities to Global Enumeration Dis - PTC Community
PPT - Enumerated Types PowerPoint Presentation, free download - ID

User Enumeration Explained: Techniques and Prevention Tips

Enumeration of Bacteria Definition, Types & Methods - Video

Python Enumerate Explained (With Examples) - Afternerd

Thomas Jefferson Quote: “Congress has not unlimited powers to
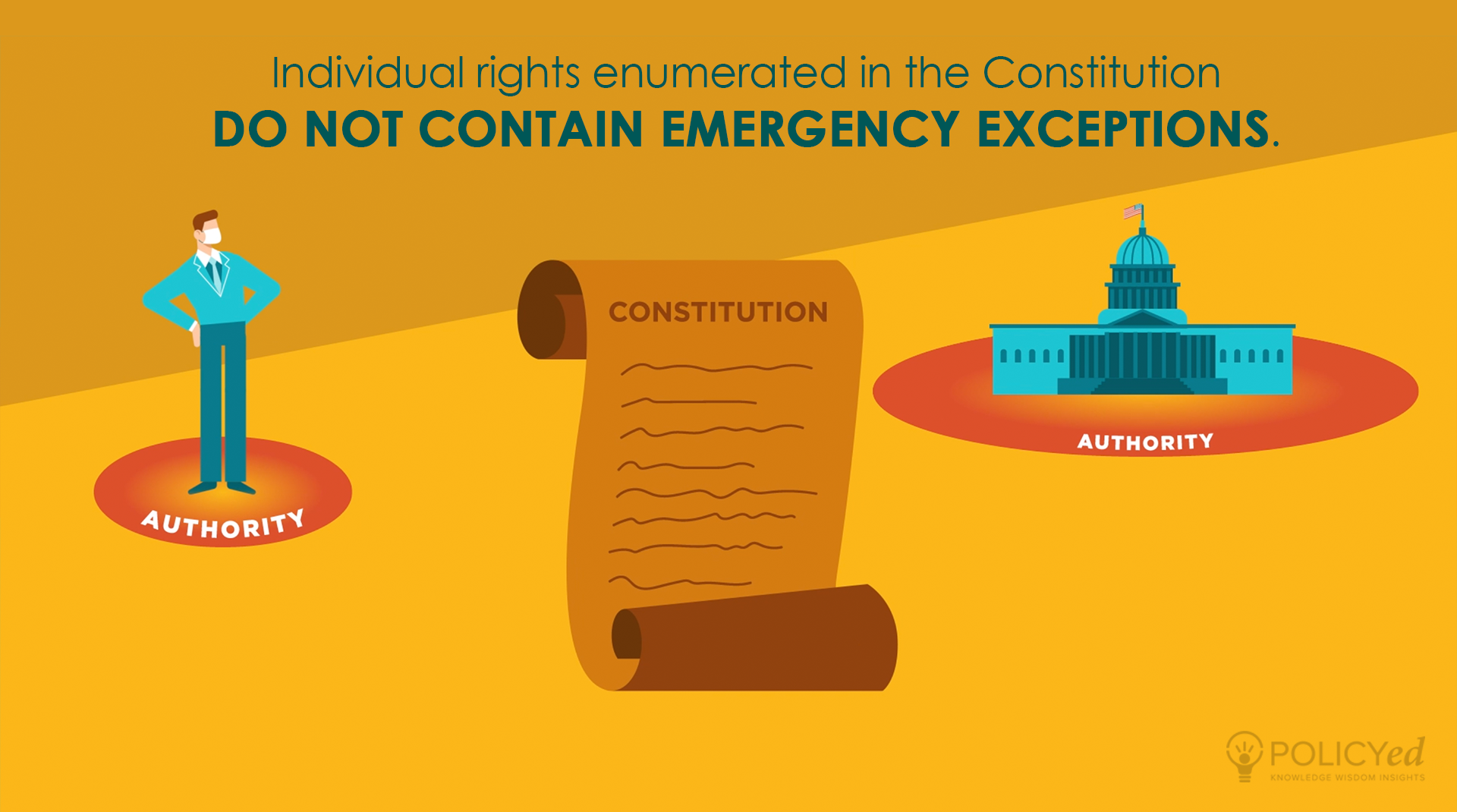
Key Facts
What Is Enumeration In Hacking? - Cyber Security Blog

Ninth Amendment: Non-Enumerated rights of the citizens
Recomendado para você
-
 Facebook: Locked Out of Your Facebook Account?21 setembro 2024
Facebook: Locked Out of Your Facebook Account?21 setembro 2024 -
 Dial +1-888-918-1764 for Facebook.Com/Login/Identify to Verify My21 setembro 2024
Dial +1-888-918-1764 for Facebook.Com/Login/Identify to Verify My21 setembro 2024 -
 Facebook 2FA is stuck in a loop and I have tried everything I can21 setembro 2024
Facebook 2FA is stuck in a loop and I have tried everything I can21 setembro 2024 -
 Facebook Warning For Koobface Virus - How to Restore your Facebook21 setembro 2024
Facebook Warning For Koobface Virus - How to Restore your Facebook21 setembro 2024 -
 Protecting young people's privacy as Facebook claims it can21 setembro 2024
Protecting young people's privacy as Facebook claims it can21 setembro 2024 -
 Find the Email Address for Your Facebook Account: Mobile App21 setembro 2024
Find the Email Address for Your Facebook Account: Mobile App21 setembro 2024 -
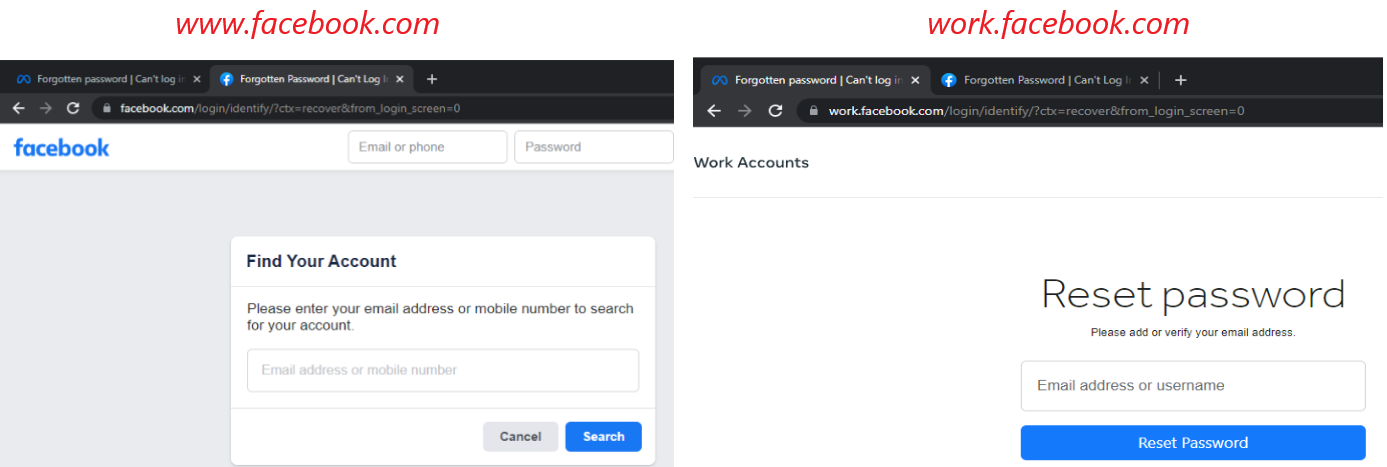 Contact Point Deanonymization Vulnerability in Meta21 setembro 2024
Contact Point Deanonymization Vulnerability in Meta21 setembro 2024 -
 Teens: Facebook is just, like, too much drama - CNET21 setembro 2024
Teens: Facebook is just, like, too much drama - CNET21 setembro 2024 -
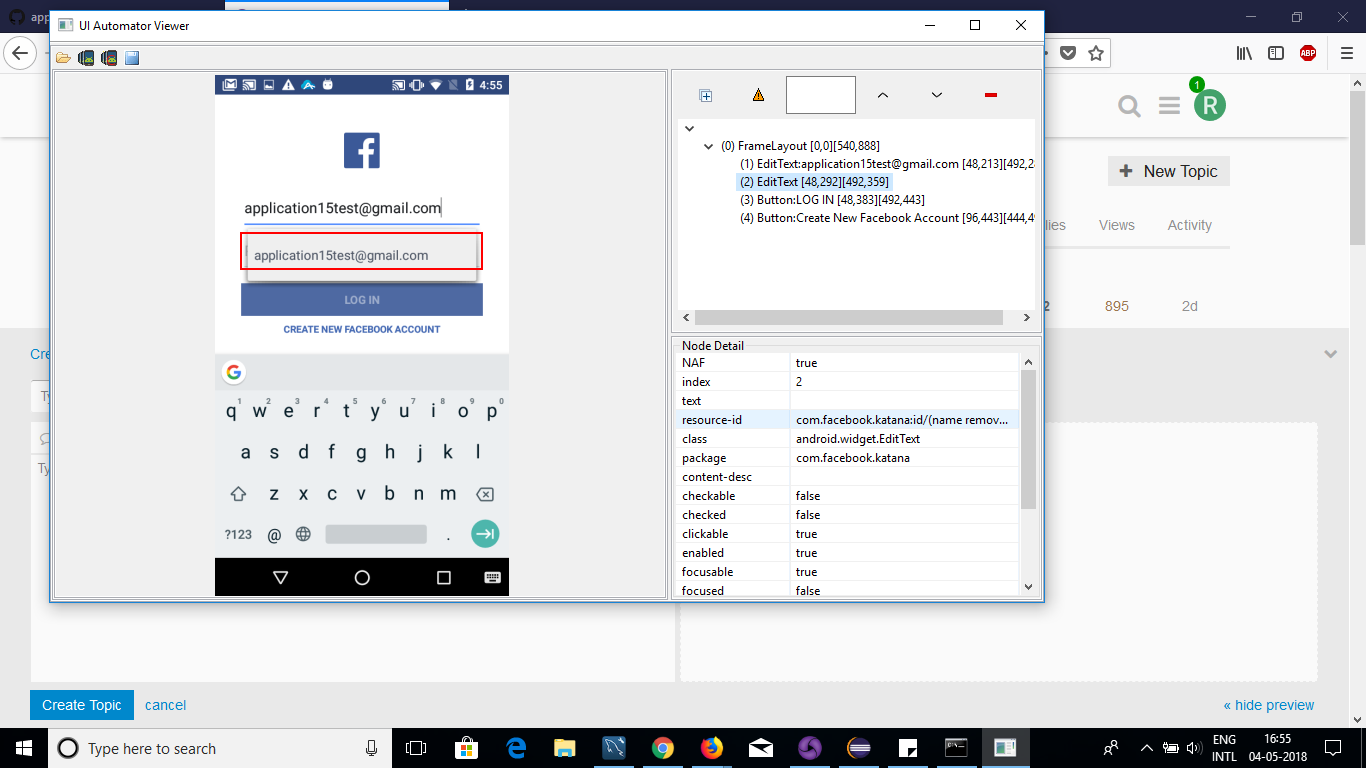 Facebook app Login not able to identify elements - Issues/Bugs21 setembro 2024
Facebook app Login not able to identify elements - Issues/Bugs21 setembro 2024 -
 Forgot my Facebook password, how to reset it?21 setembro 2024
Forgot my Facebook password, how to reset it?21 setembro 2024
você pode gostar
-
 Tati Gabrielle's Best Hairstyle Moments: Pixie Cuts, Braids, & More21 setembro 2024
Tati Gabrielle's Best Hairstyle Moments: Pixie Cuts, Braids, & More21 setembro 2024 -
 TRADUÇÃO PARA O PORTUGUÊS BR DO POKEMON LEGENDS ARCEUS NO RYUJINX21 setembro 2024
TRADUÇÃO PARA O PORTUGUÊS BR DO POKEMON LEGENDS ARCEUS NO RYUJINX21 setembro 2024 -
 DVD Anime LOG Horizon Complete Series Season 1-3 (1-62) ENGLISH DUBBED + Special21 setembro 2024
DVD Anime LOG Horizon Complete Series Season 1-3 (1-62) ENGLISH DUBBED + Special21 setembro 2024 -
 Como Colocar Letras Coloridas FF e Dicas de Nick, Chat e Bio (PT)21 setembro 2024
Como Colocar Letras Coloridas FF e Dicas de Nick, Chat e Bio (PT)21 setembro 2024 -
 Hyperkin Scout Premium BT Controller for Super NES21 setembro 2024
Hyperkin Scout Premium BT Controller for Super NES21 setembro 2024 -
 Flags With Hearts Quiz - By Darzlat21 setembro 2024
Flags With Hearts Quiz - By Darzlat21 setembro 2024 -
 Sunday Snippet: Sum 41 (Pieces) » Beyond the Rhetoric21 setembro 2024
Sunday Snippet: Sum 41 (Pieces) » Beyond the Rhetoric21 setembro 2024 -
 Volume 11, Komi-san wa Komyushou Desu Wiki21 setembro 2024
Volume 11, Komi-san wa Komyushou Desu Wiki21 setembro 2024 -
 Jiafei Products, Floptok Wiki21 setembro 2024
Jiafei Products, Floptok Wiki21 setembro 2024 -
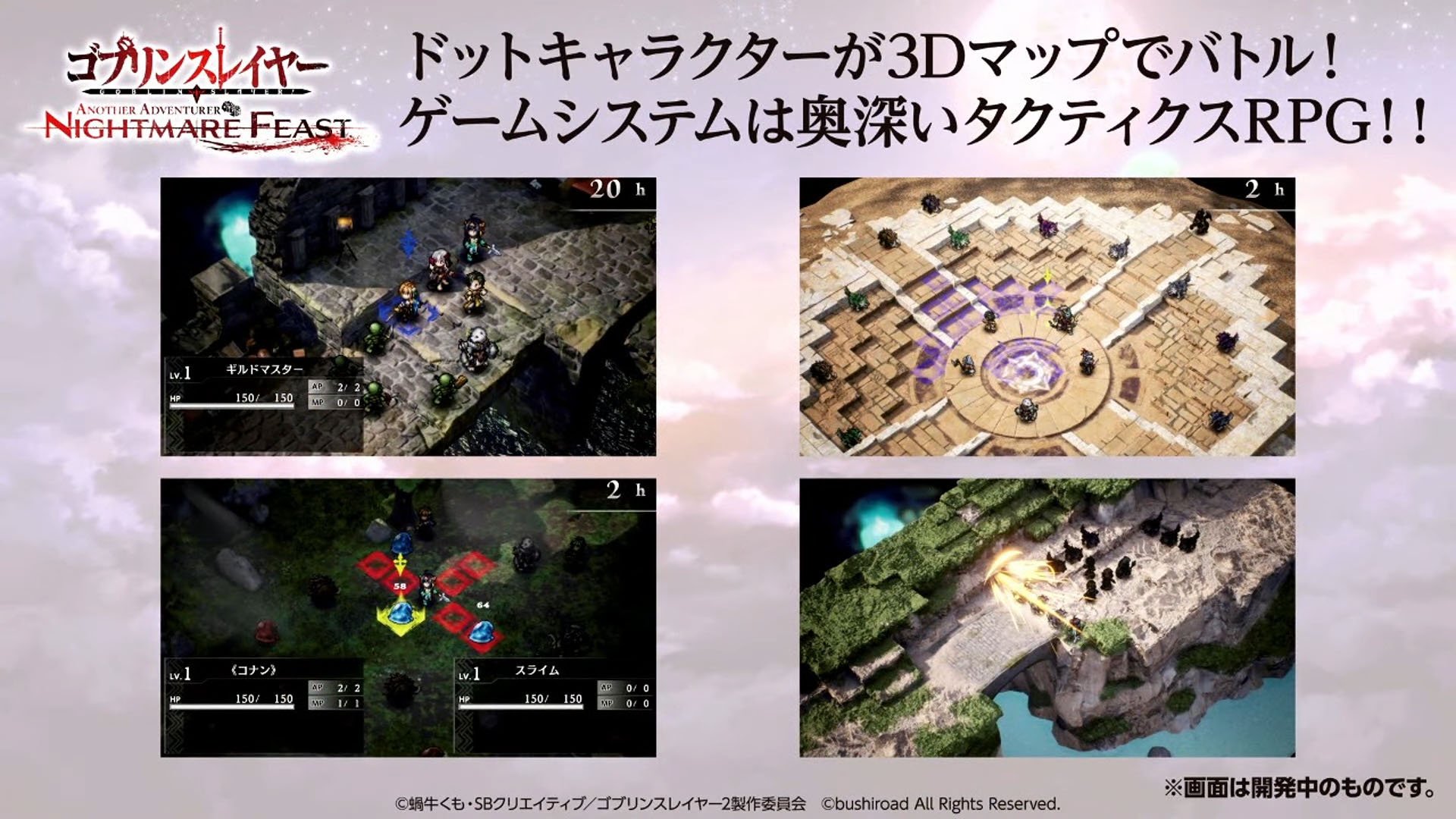 Goblin Slayer Another Adventurer: Nightmare Feast ganha data de lançamento para Nintendo Switch21 setembro 2024
Goblin Slayer Another Adventurer: Nightmare Feast ganha data de lançamento para Nintendo Switch21 setembro 2024