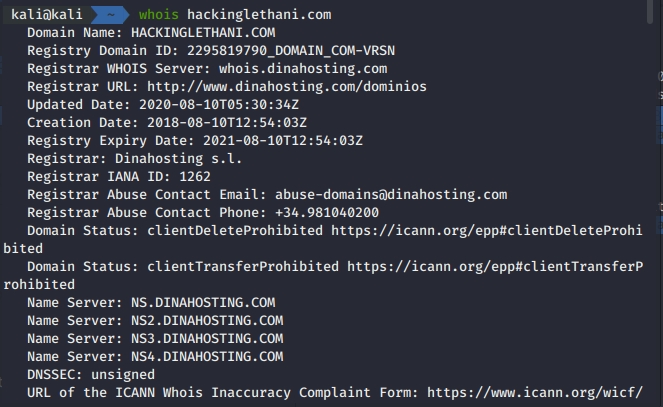
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 23 dezembro 2024
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Should you use Let's Encrypt for internal hostnames? – Terence Eden's Blog

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
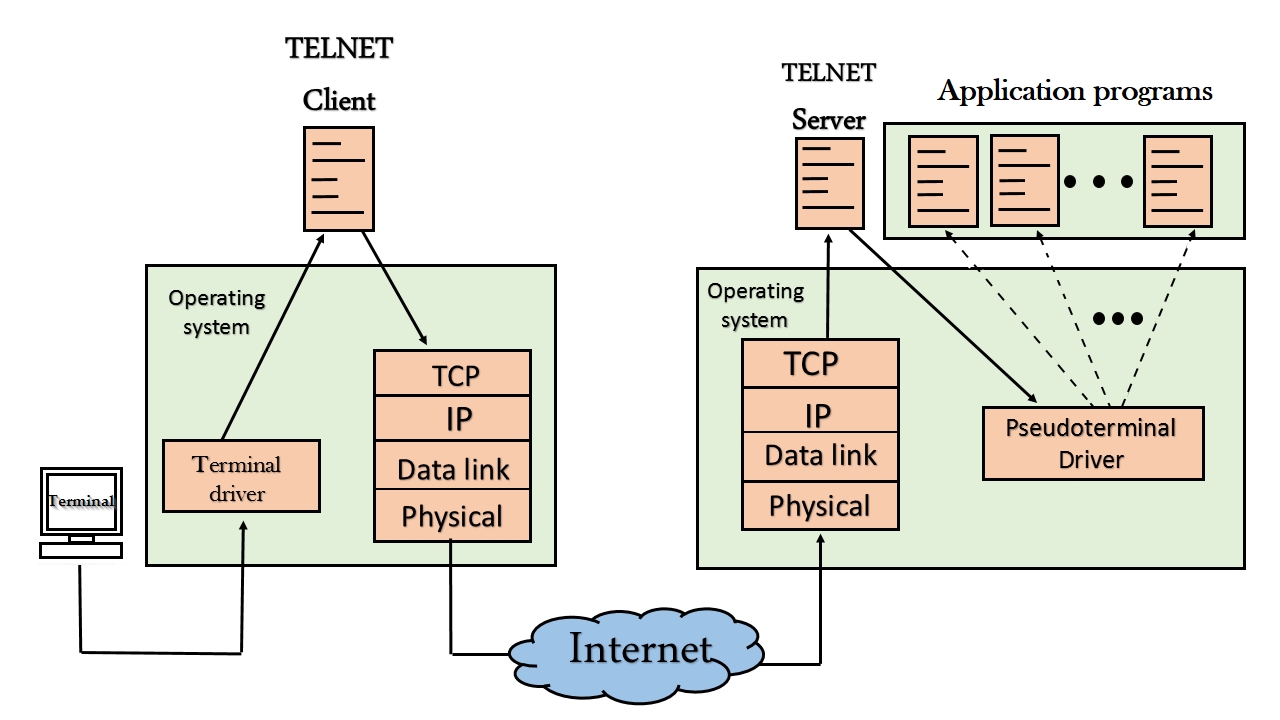
Infrastructure Hacking: Telnet Protocol » Hacking Lethani
How to Build an Active Directory Hacking Lab - The Cyber Mentor channel : r/homelab

Explained: The Tinyman Hack (January 2022)

Ethical Hacking Learning Path — A Complete Roadmap, by crawsecurity

Infrastructure Hacking: Telnet Protocol » Hacking Lethani
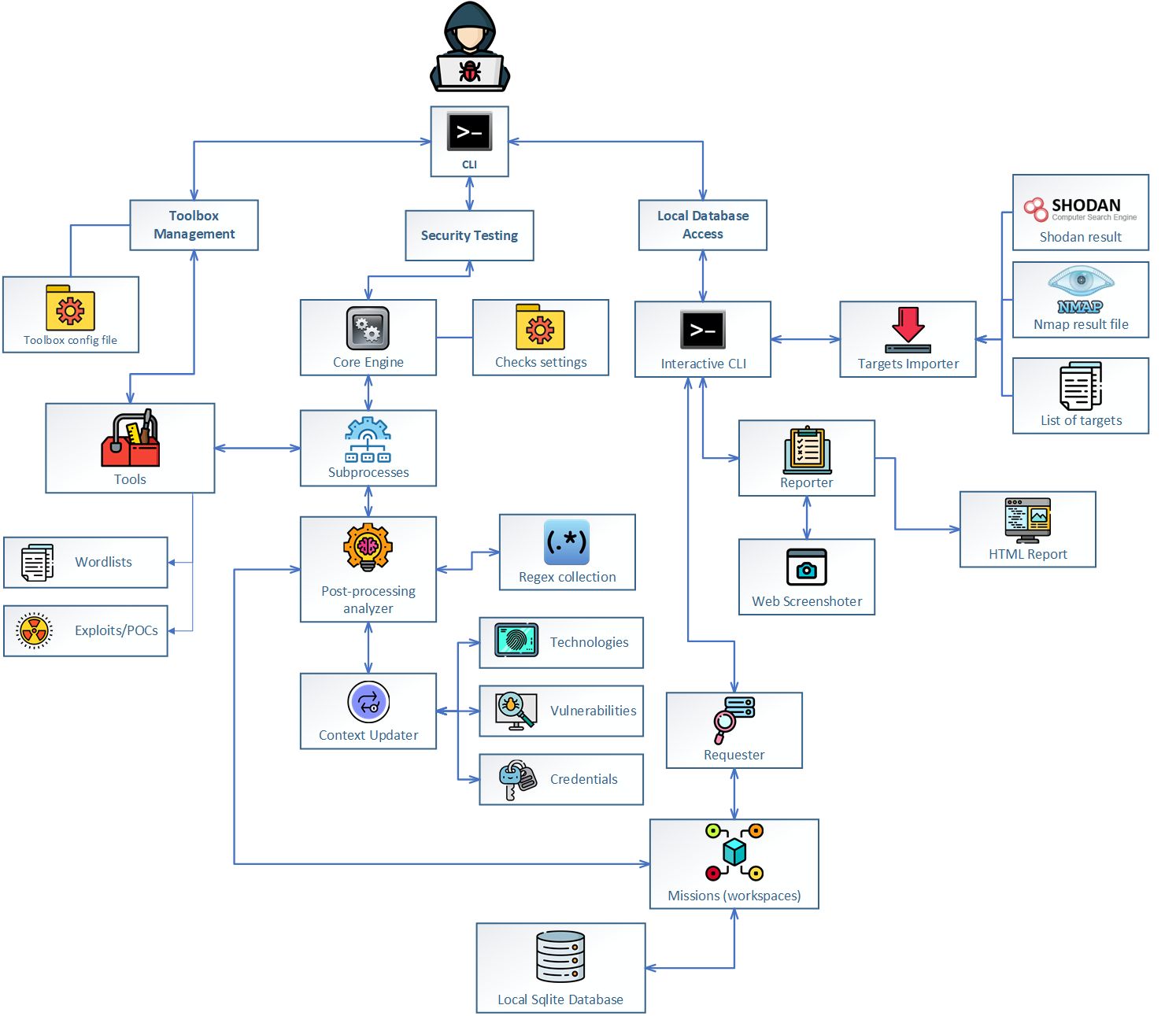
Jok3r v3 BETA 2 - Network and Web Pentest Automation Framework

DNC Hacks: How Spear Phishing Emails Were Used
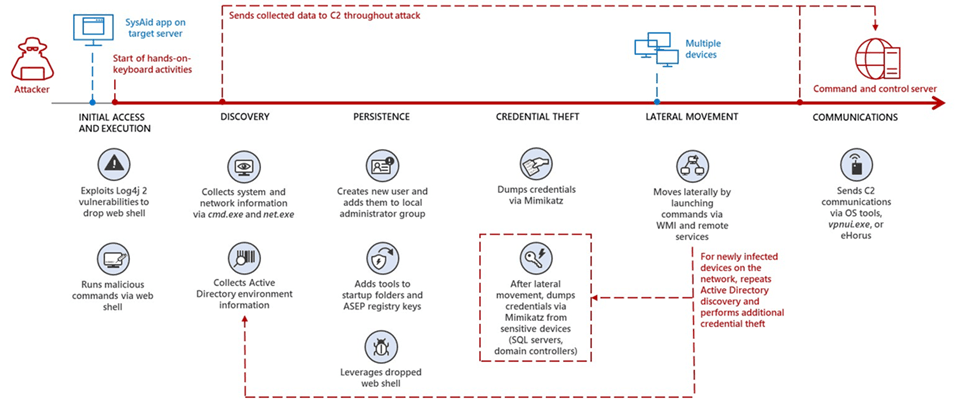
Microsoft: Nation-state Iranian hackers exploit Log4Shell against Israel
Ethical Hacking - Quick Guide

Russian APT hacked Iranian APT's infrastructure back in 2017
Recomendado para você
-
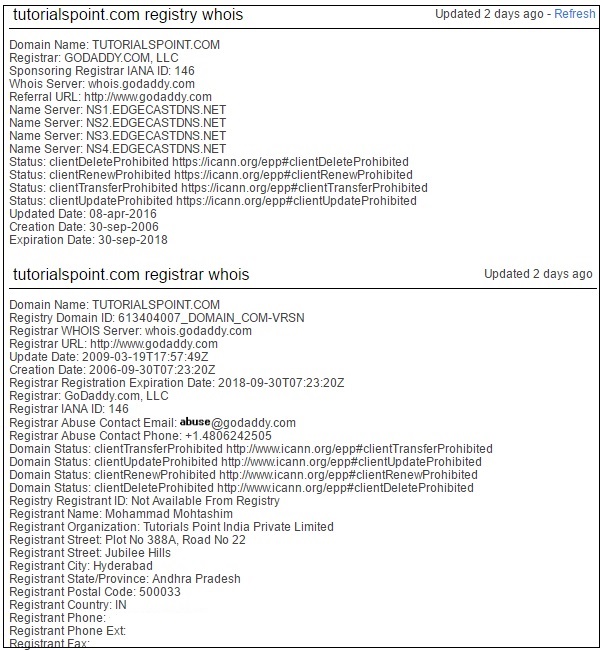
 How To Find Whois Domain Information from Command Line23 dezembro 2024
How To Find Whois Domain Information from Command Line23 dezembro 2024 -
 What is WHOIS and How Is It Used?23 dezembro 2024
What is WHOIS and How Is It Used?23 dezembro 2024 -
 WhoIs Domain Lookup - Tools - Joydeep Deb23 dezembro 2024
WhoIs Domain Lookup - Tools - Joydeep Deb23 dezembro 2024 -
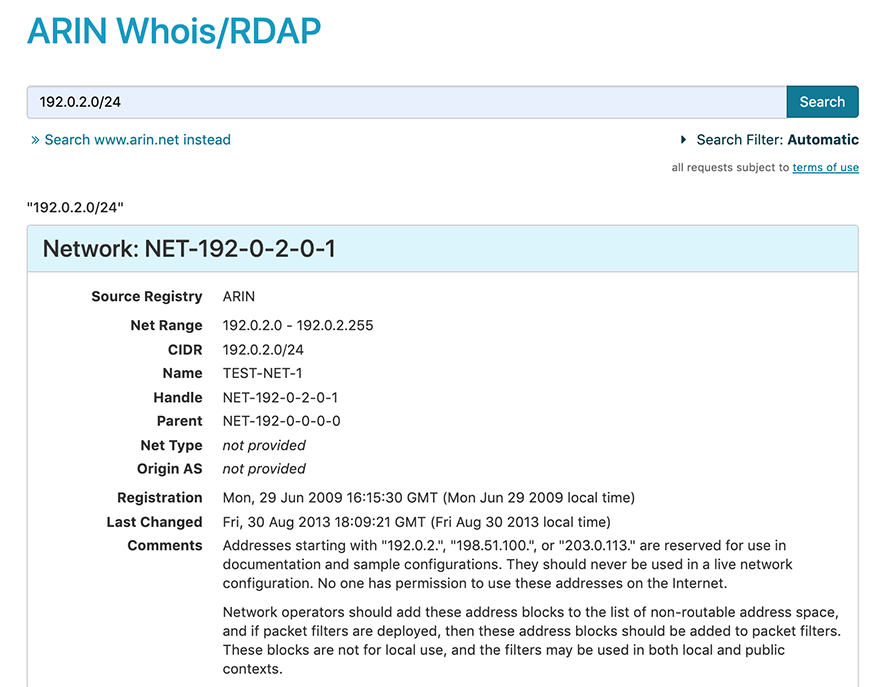 Using Whois - American Registry for Internet Numbers23 dezembro 2024
Using Whois - American Registry for Internet Numbers23 dezembro 2024 -
 WHOis Domain Name Search23 dezembro 2024
WHOis Domain Name Search23 dezembro 2024 -
 Whois.com Review 2023. whois.com good host in Singapore?23 dezembro 2024
Whois.com Review 2023. whois.com good host in Singapore?23 dezembro 2024 -
 Enriching threat feeds with WHOIS information23 dezembro 2024
Enriching threat feeds with WHOIS information23 dezembro 2024 -
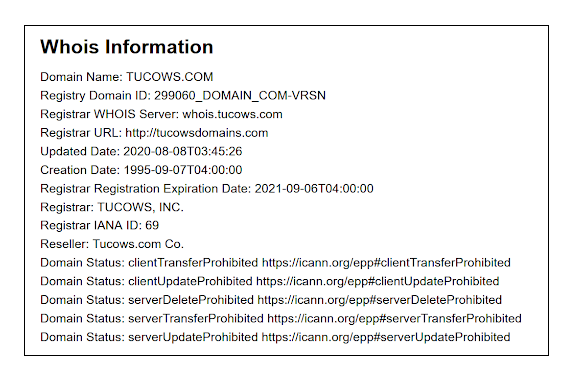 What do domain status codes mean?23 dezembro 2024
What do domain status codes mean?23 dezembro 2024 -
 Prefix WhoIs - Wikipedia23 dezembro 2024
Prefix WhoIs - Wikipedia23 dezembro 2024 -
 A Quick Guide to ARIN's Whois - ARIN's Vault23 dezembro 2024
A Quick Guide to ARIN's Whois - ARIN's Vault23 dezembro 2024
você pode gostar
-
 The 100th Regression of the Max-Level Player - Chapter 1 - مانجا ARESManga23 dezembro 2024
The 100th Regression of the Max-Level Player - Chapter 1 - مانجا ARESManga23 dezembro 2024 -
 ADJ F-Scent Fog Juice Scent - Vanilla23 dezembro 2024
ADJ F-Scent Fog Juice Scent - Vanilla23 dezembro 2024 -
 Xiaomi 11T apresenta limitações em testes da câmera frontal - Canaltech23 dezembro 2024
Xiaomi 11T apresenta limitações em testes da câmera frontal - Canaltech23 dezembro 2024 -
 Rainbow Friends PNG23 dezembro 2024
Rainbow Friends PNG23 dezembro 2024 -
 Kageki Shoujo!! - Anime terá 13 episódios - AnimeNew23 dezembro 2024
Kageki Shoujo!! - Anime terá 13 episódios - AnimeNew23 dezembro 2024 -
 Oficinas de Férias - Quiz - Sesc Paraná23 dezembro 2024
Oficinas de Férias - Quiz - Sesc Paraná23 dezembro 2024 -
 Dragon Ball Z Royalty-Free Images, Stock Photos & Pictures23 dezembro 2024
Dragon Ball Z Royalty-Free Images, Stock Photos & Pictures23 dezembro 2024 -
 Ludo Championship, Ludo Khelne Wala Game, Ludo Game Online23 dezembro 2024
Ludo Championship, Ludo Khelne Wala Game, Ludo Game Online23 dezembro 2024 -
 The most important PC games of all time23 dezembro 2024
The most important PC games of all time23 dezembro 2024 -
 New Mutants: Lethal Legion (2023-) Chapter 2 - Page 223 dezembro 2024
New Mutants: Lethal Legion (2023-) Chapter 2 - Page 223 dezembro 2024