Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools
Por um escritor misterioso
Last updated 22 dezembro 2024

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.

Red Team tactics – breaching the lines of defense – Comsec Global

Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's

TTPs Within Cyber Threat Intelligence

Purple Team - Work it out: Organizing Effective Adversary
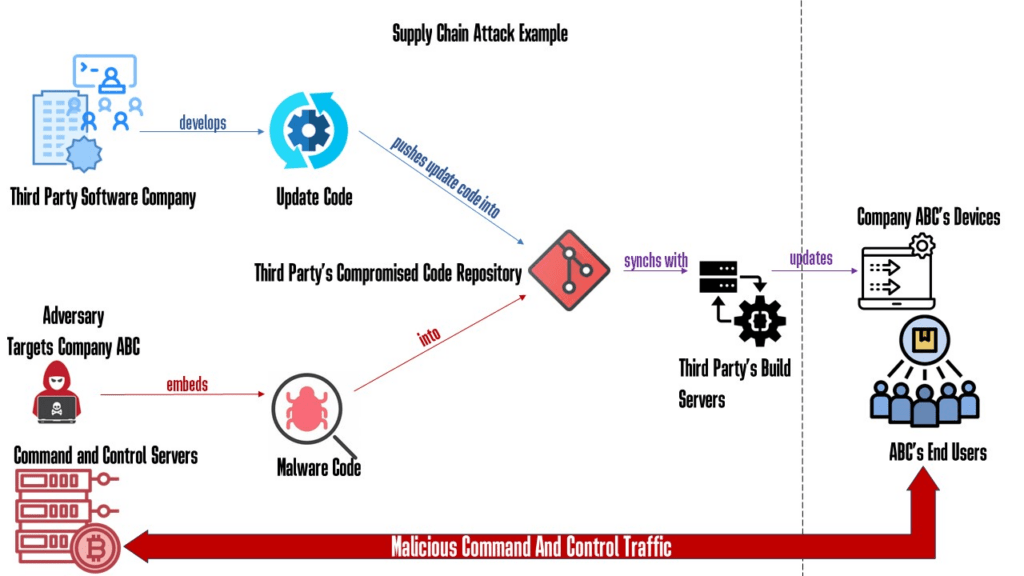
Why Red Teaming Should Be In A Supply Chain Defense Strategy
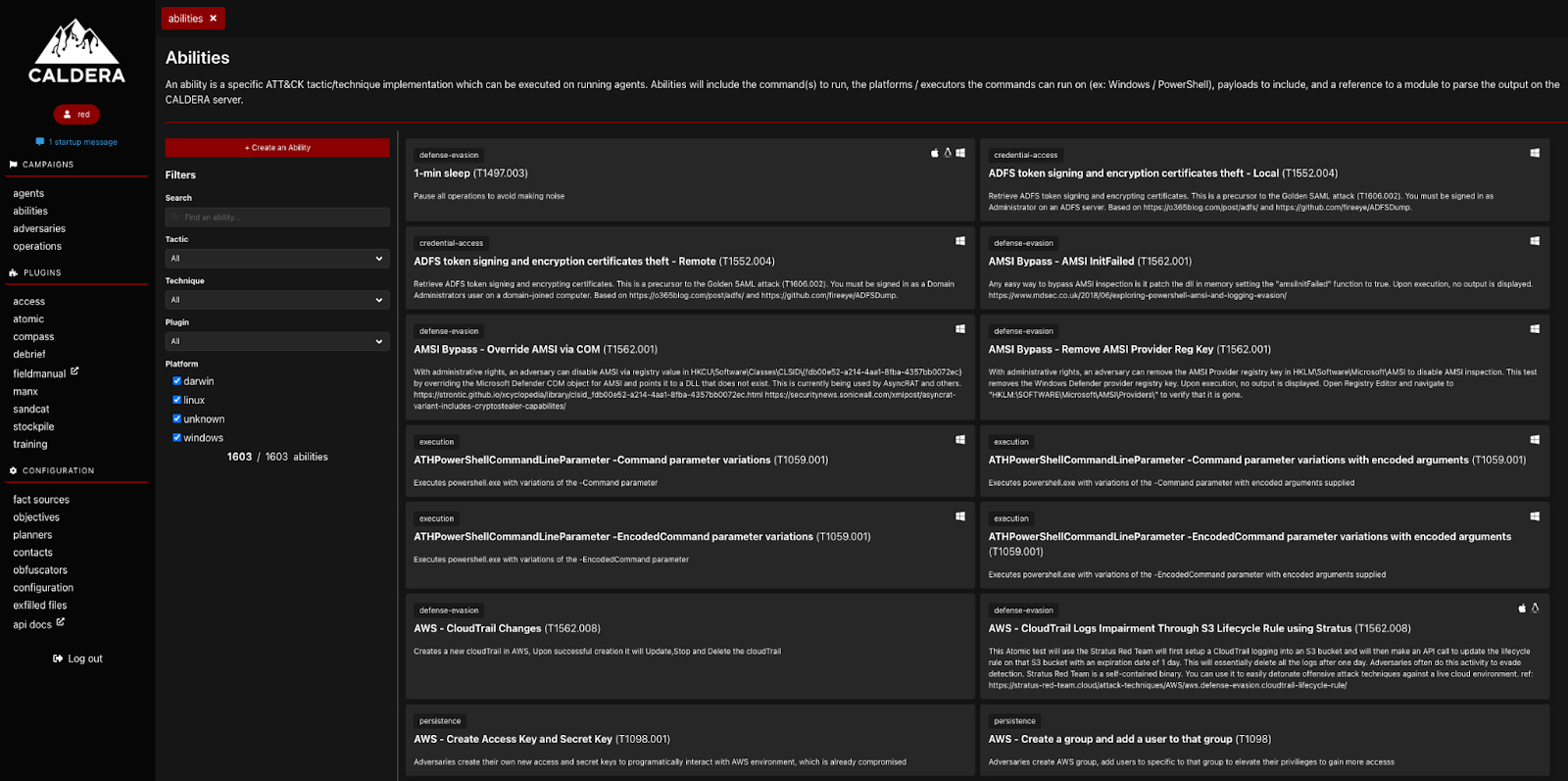
Adversary Simulation: Tools and Techniques

Red Team Assessment, Dubai

BOLO - Be On The Lookout: FireEye Red Team Tools Stolen in Nation

Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
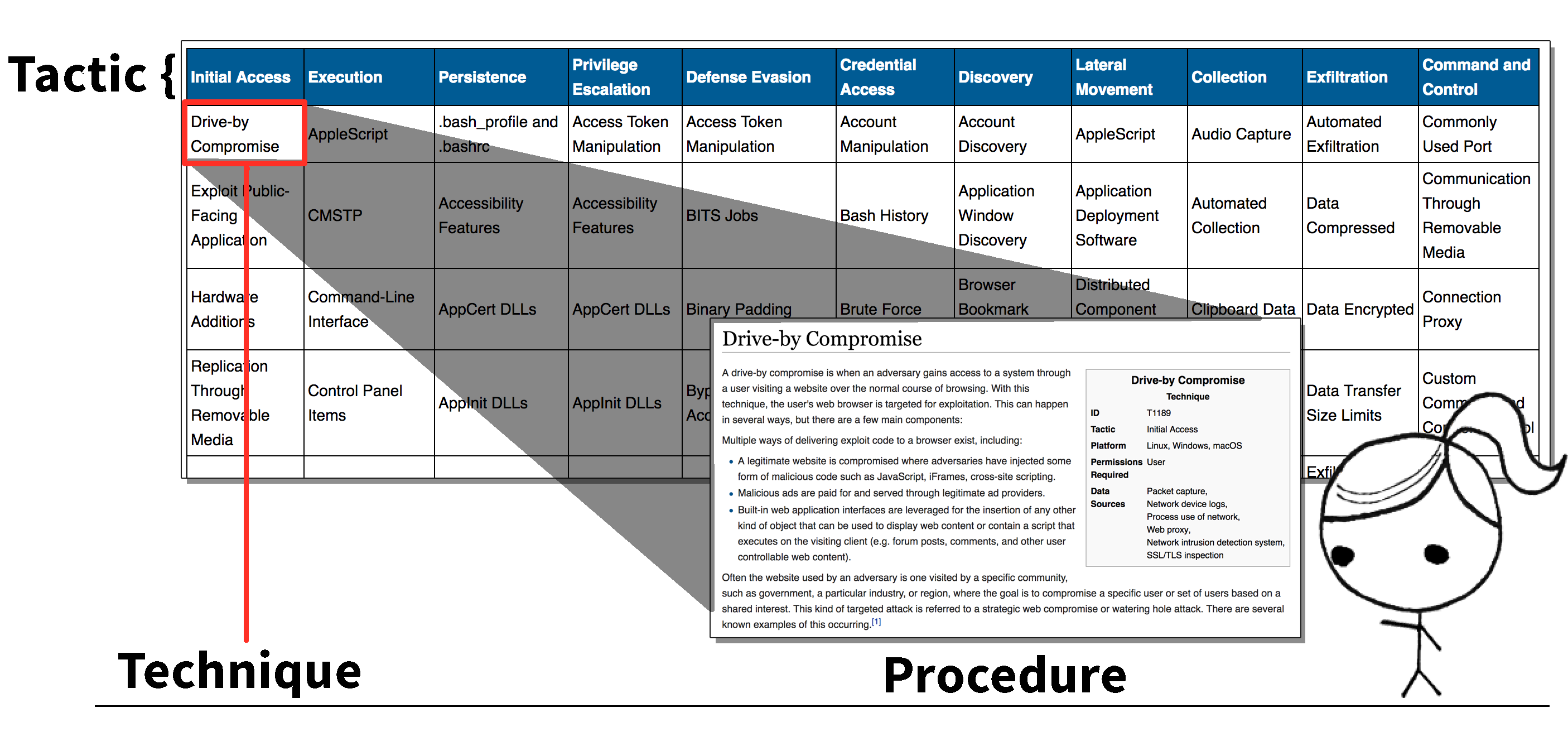
Red Teaming and MITRE ATT&CK Red Team Development and Operations
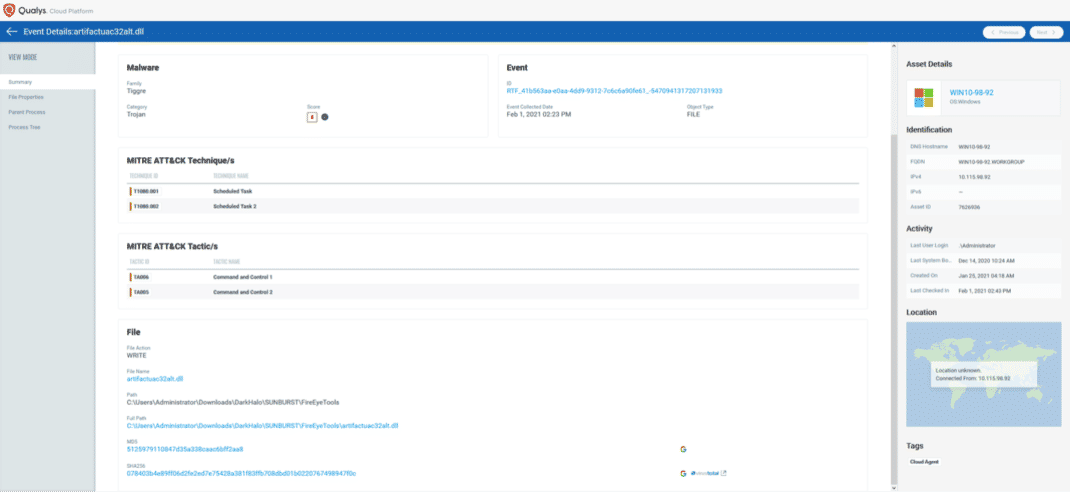
Unpacking the CVEs in the FireEye Breach - Start Here First
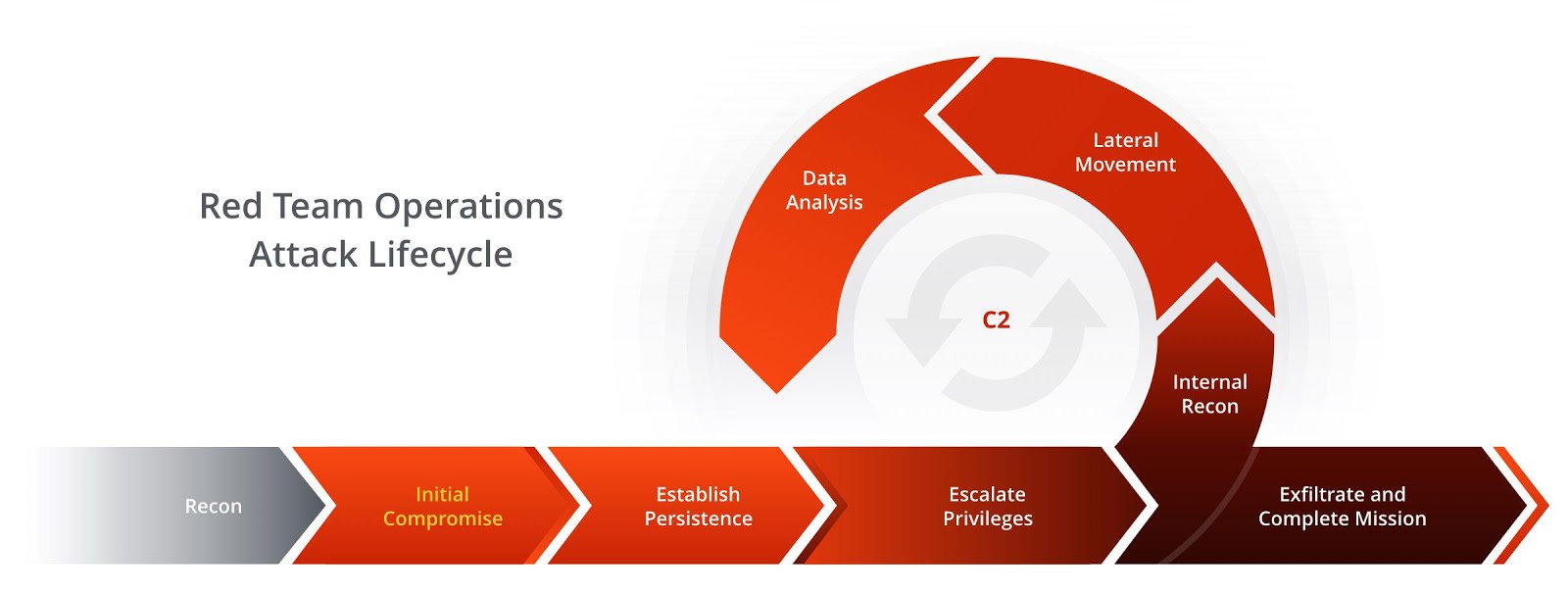
Redteam-Hardware-Toolkit - Red Team Hardware Toolkit

Red Team Tools Detection and Alerting
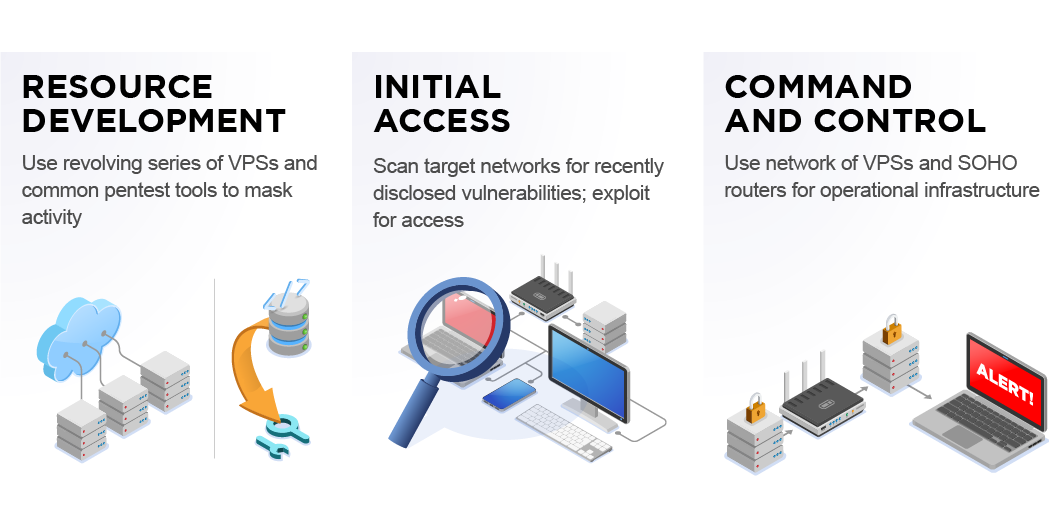
Chinese State-Sponsored Cyber Operations: Observed TTPs

Purple Team - Work it out: Organizing Effective Adversary
Recomendado para você
-
 HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!22 dezembro 2024
HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!22 dezembro 2024 -
GitHub - SonsoFsERpent/redEngine-Spoofer: With the redENGINE22 dezembro 2024
-
 Risk Intelligence & Device Fingerprinting Solution22 dezembro 2024
Risk Intelligence & Device Fingerprinting Solution22 dezembro 2024 -
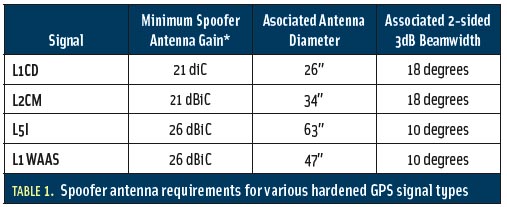 Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation22 dezembro 2024
Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation22 dezembro 2024 -
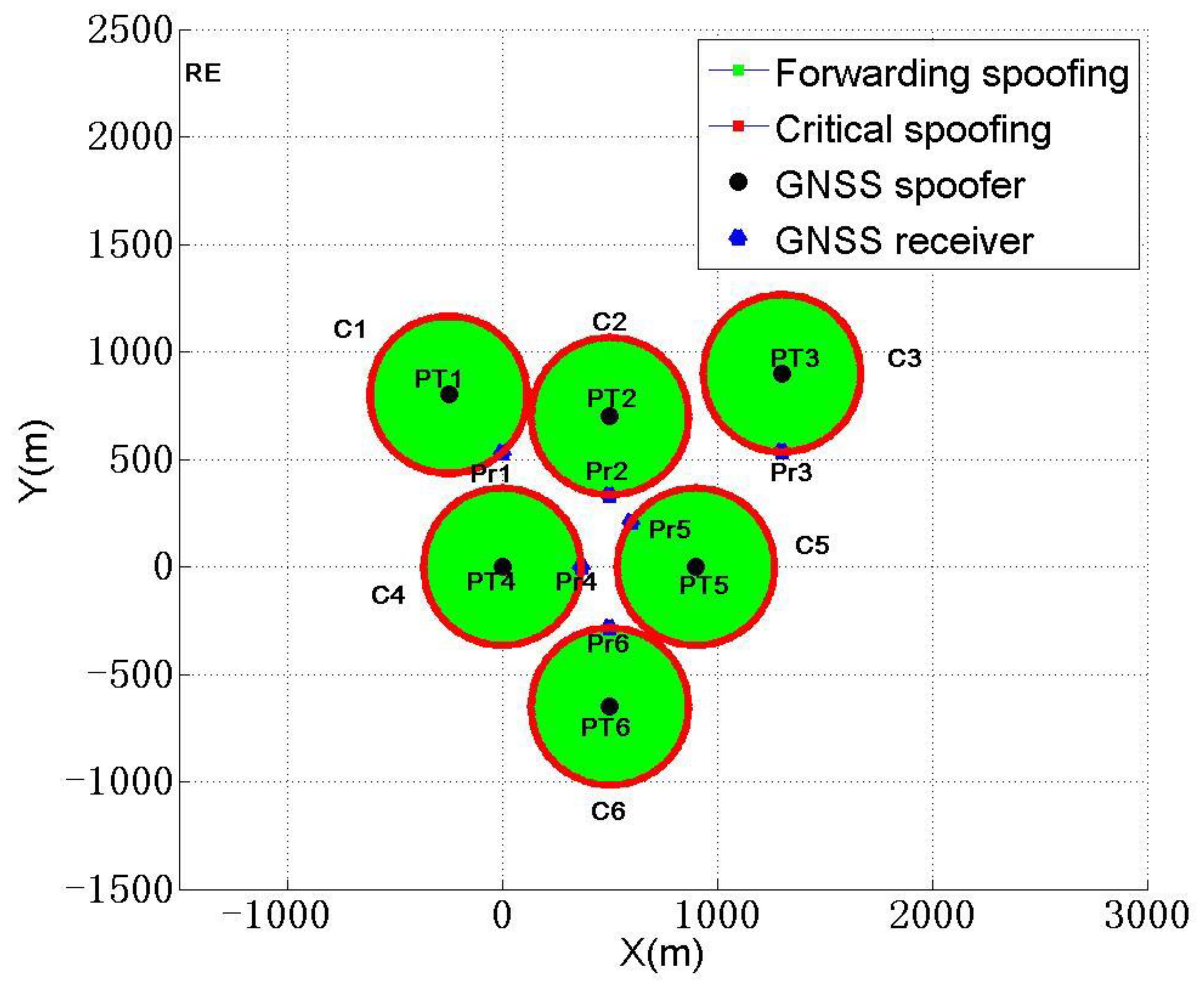 Sensors, Free Full-Text22 dezembro 2024
Sensors, Free Full-Text22 dezembro 2024 -
hwid-spoofer · GitHub Topics · GitHub22 dezembro 2024
-
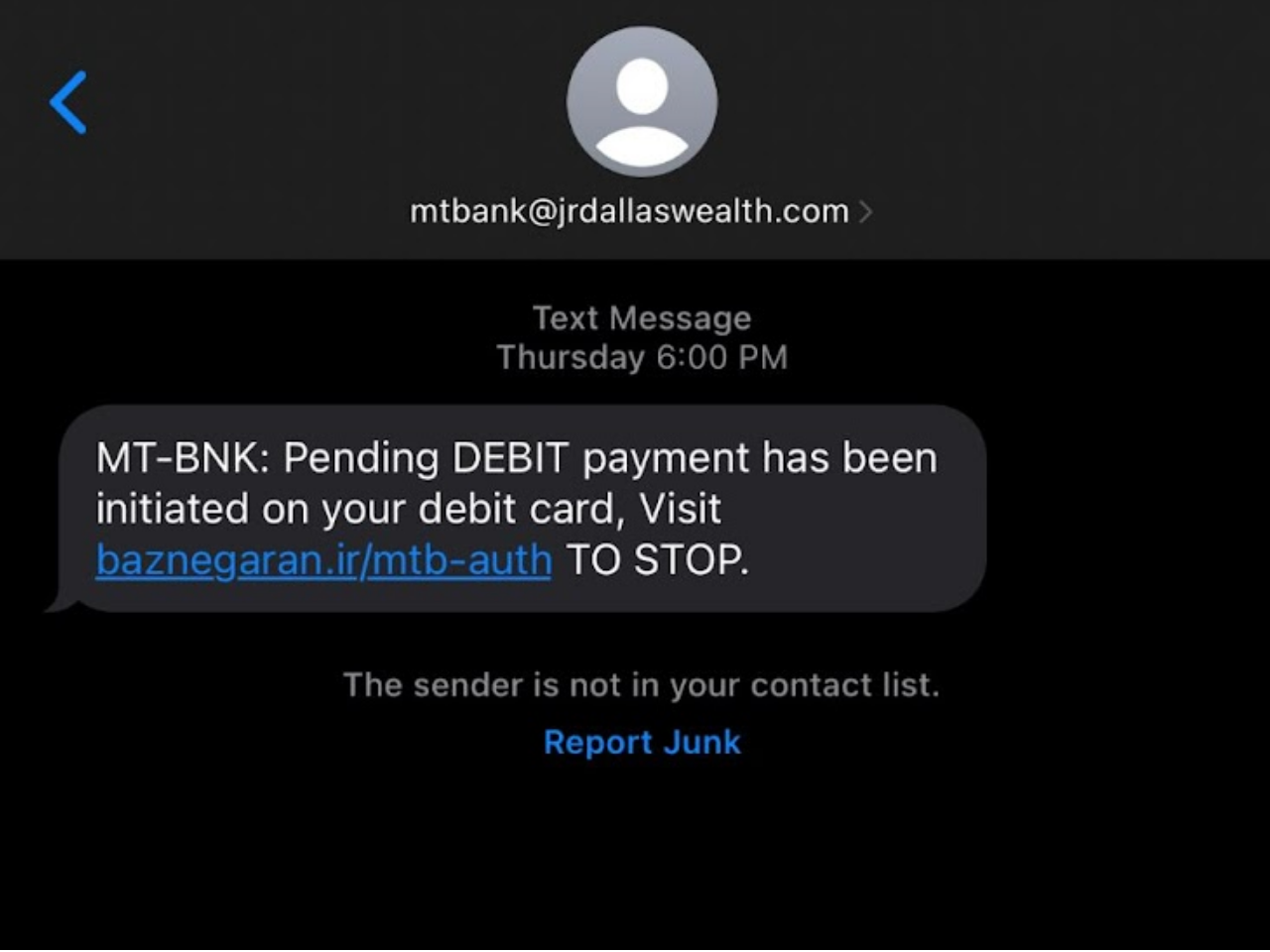 What Is Spoofing In Cybersecurity?22 dezembro 2024
What Is Spoofing In Cybersecurity?22 dezembro 2024 -
 Location Spoofing, Detect Fake GPS Location22 dezembro 2024
Location Spoofing, Detect Fake GPS Location22 dezembro 2024 -
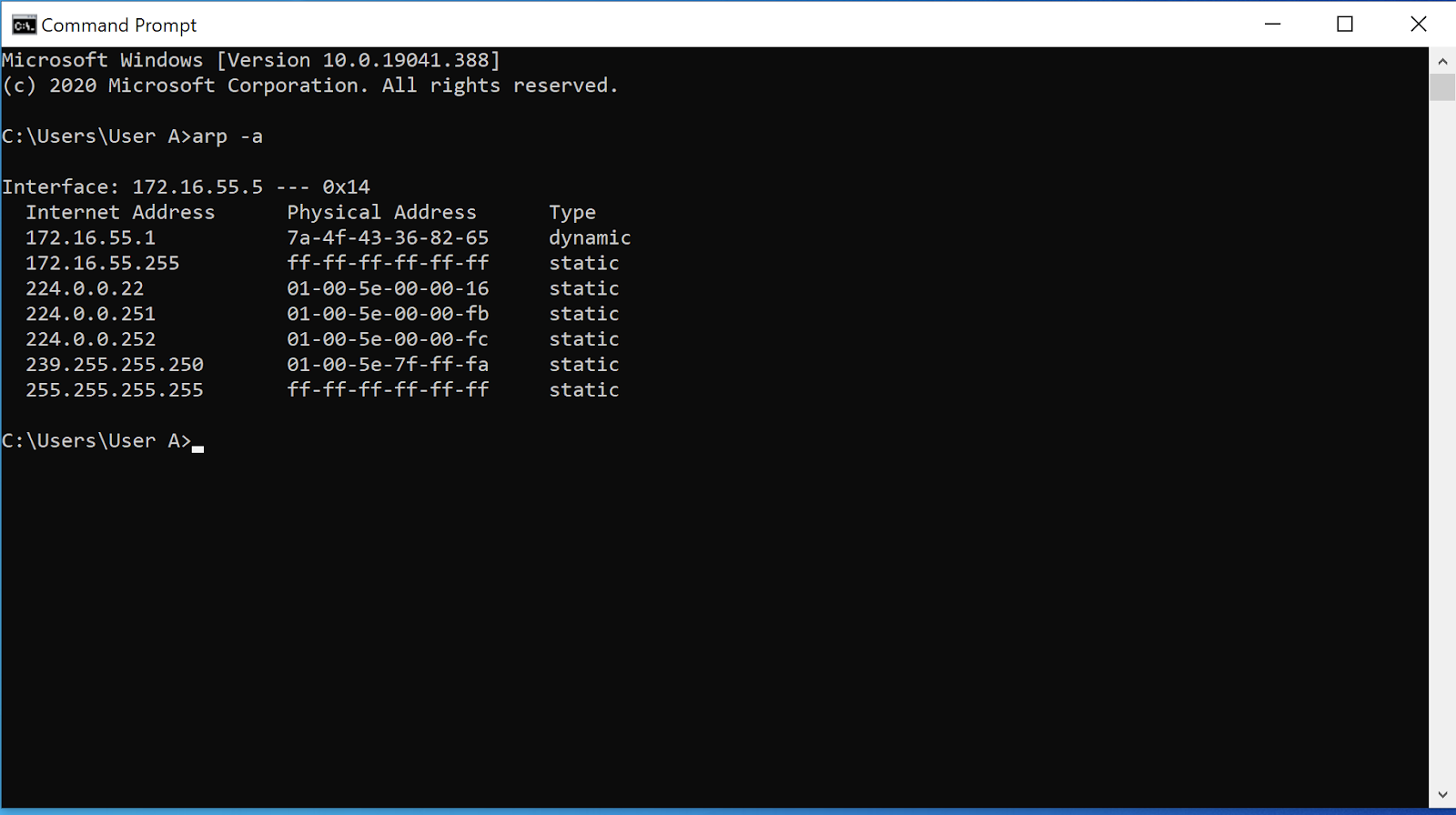 ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks22 dezembro 2024
ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks22 dezembro 2024 -
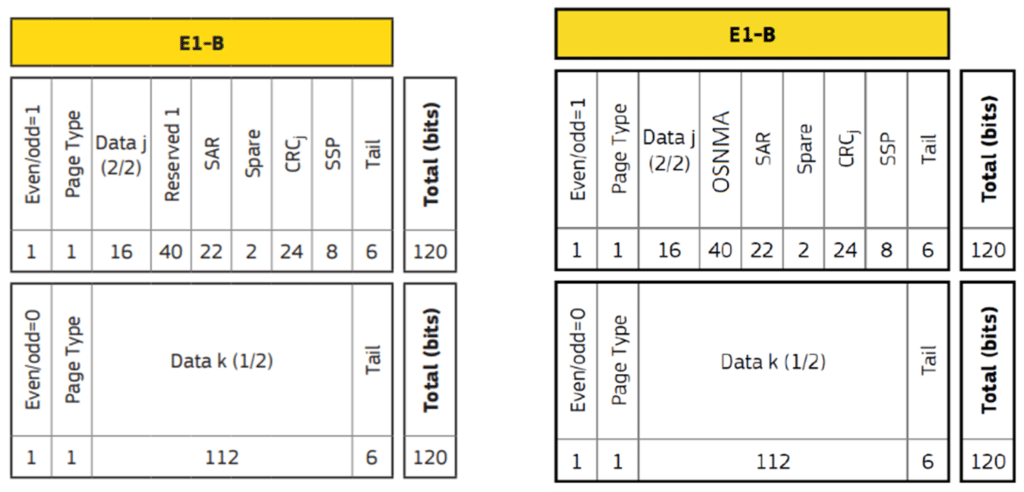 Testing a Receiver's Galileo OS-NMA Capability Using Skydel22 dezembro 2024
Testing a Receiver's Galileo OS-NMA Capability Using Skydel22 dezembro 2024
você pode gostar
-
 Daiko O Saiyajin on X: Rascunho do capítulo 93 do mangá de Dragon Ball Super! Parece que teremos a continuação da luta entre Broly e Goku, algo que não foi mostrado no22 dezembro 2024
Daiko O Saiyajin on X: Rascunho do capítulo 93 do mangá de Dragon Ball Super! Parece que teremos a continuação da luta entre Broly e Goku, algo que não foi mostrado no22 dezembro 2024 -
 5 curiosidades sobre All Of Us Are Dead22 dezembro 2024
5 curiosidades sobre All Of Us Are Dead22 dezembro 2024 -
 FINNEGANS WAKE: A Tentative Crossing in Portuguese, by Dirce Waltrick do Amarante22 dezembro 2024
FINNEGANS WAKE: A Tentative Crossing in Portuguese, by Dirce Waltrick do Amarante22 dezembro 2024 -
 TOP 5 RAP DO ANIME NARUTO PARTE 122 dezembro 2024
TOP 5 RAP DO ANIME NARUTO PARTE 122 dezembro 2024 -
 Hill Climb Racing 2 Play It Now At !22 dezembro 2024
Hill Climb Racing 2 Play It Now At !22 dezembro 2024 -
 Tuttosport: Milan battling Inter for 24-year-old Torino defender who could replace Romagnoli22 dezembro 2024
Tuttosport: Milan battling Inter for 24-year-old Torino defender who could replace Romagnoli22 dezembro 2024 -
 Camp Half-Blood ID by SLONE13 on DeviantArt22 dezembro 2024
Camp Half-Blood ID by SLONE13 on DeviantArt22 dezembro 2024 -
 Mis dibujos Kawaii, tiernos y adorables22 dezembro 2024
Mis dibujos Kawaii, tiernos y adorables22 dezembro 2024 -
 Let's Dig In - E's Construction Birthday Party - My Suburban Kitchen22 dezembro 2024
Let's Dig In - E's Construction Birthday Party - My Suburban Kitchen22 dezembro 2024 -
Big Brother Reindeer Games' Cast: Meet the Former Players Competing22 dezembro 2024
