PDF] Analysing web-based malware behaviour through client honeypots
Por um escritor misterioso
Last updated 22 dezembro 2024
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/122-Figure7-8-1.png)
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/114-Figure7-2-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://ars.els-cdn.com/content/image/1-s2.0-S1574013723000679-gr2.jpg)
Flow based containerized honeypot approach for network traffic analysis: An empirical study - ScienceDirect
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/15-Table1-1-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.researchgate.net/profile/Sanjeev-Kumar-356/publication/271503033/figure/fig1/AS:11431281089703250@1665664744295/Flow-Diagram-of-Integrated-Framework_Q320.jpg)
PDF) Hybrid honeypot framework for malware collection and analysis
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/30-Figure2-2-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/135-Figure7-16-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://image.slidesharecdn.com/basicsurveyonmalwareanalysistoolsandtechniques-140312015530-phpapp01/85/basic-survey-on-malware-analysis-tools-and-techniques-1-320.jpg?cb=1670364094)
Basic survey on malware analysis, tools and techniques
![PDF] Analysing web-based malware behaviour through client honeypots](https://cdn.ttgtmedia.com/rms/onlineimages/security-honeypot_place_in_network-f_mobile.png)
What is a honeypot? How it protects against cyber attacks
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.ntt-review.jp/archive_html/201210/images/fa2_fig05.jpg)
Detection, Analysis, and Countermeasure Technologies for Cyber Attacks from Evolving Malware
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.ntt-review.jp/archive_html/201007/images/sf3_fig01.gif)
Anti-Malware Technologies
![PDF] Analysing web-based malware behaviour through client honeypots](https://media.springernature.com/lw685/springer-static/image/chp%3A10.1007%2F978-3-030-98002-3_23/MediaObjects/529440_1_En_23_Fig1_HTML.png)
Faking Smart Industry: A Honeypot-Driven Approach for Exploring Cyber Security Threat Landscape
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.researchgate.net/publication/344735922/figure/fig1/AS:956682159013890@1605102209709/Client-honeypot-design_Q320.jpg)
PDF) A Detection of Malware Embedded into Web Pages Using Client Honeypot
![PDF] Analysing web-based malware behaviour through client honeypots](https://imgv2-2-f.scribdassets.com/img/document/248385507/149x198/a692ca61e9/1423748517?v=1)
Integrated Honeypot Based Malware Collection and Analysis, PDF, Computer Virus
![PDF] Analysing web-based malware behaviour through client honeypots](https://ars.els-cdn.com/content/image/1-s2.0-S1574013723000679-gr3.jpg)
Flow based containerized honeypot approach for network traffic analysis: An empirical study - ScienceDirect
Recomendado para você
-
IKARUS mobile.security - Apps on Google Play22 dezembro 2024
-
 command line IKARUS antivirus engine - The Portable Freeware Collection Forums22 dezembro 2024
command line IKARUS antivirus engine - The Portable Freeware Collection Forums22 dezembro 2024 -
 shakti-trojan-what-it-is-and-what-you-can-do-about-it22 dezembro 2024
shakti-trojan-what-it-is-and-what-you-can-do-about-it22 dezembro 2024 -
 malware - Why is my debugger detected as a Trojan by anti-virus software? - Information Security Stack Exchange22 dezembro 2024
malware - Why is my debugger detected as a Trojan by anti-virus software? - Information Security Stack Exchange22 dezembro 2024 -
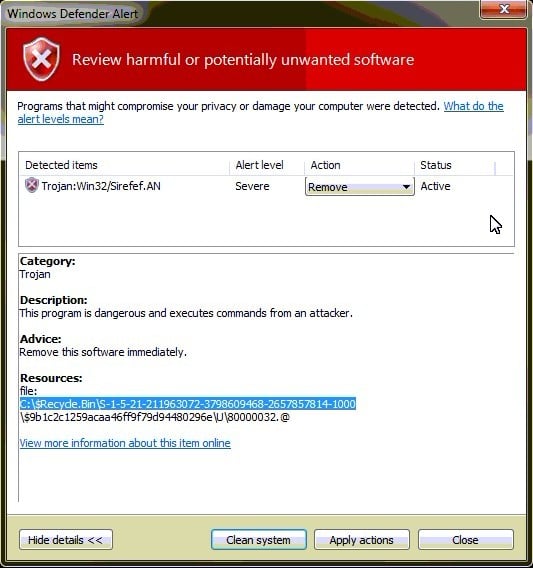 How To Completely Remove Sirefef Trojan (Virus Removal Guide)22 dezembro 2024
How To Completely Remove Sirefef Trojan (Virus Removal Guide)22 dezembro 2024 -
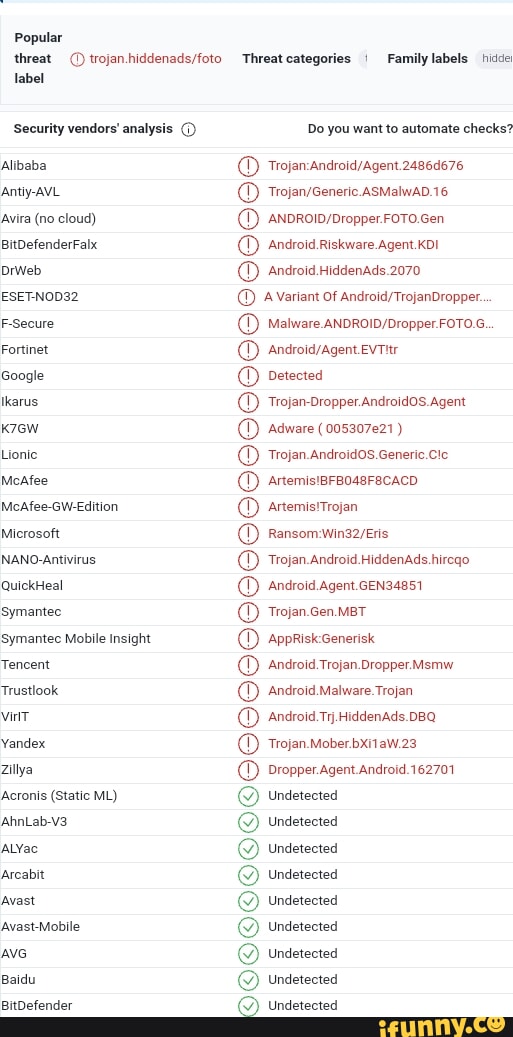 Ikarus memes. Best Collection of funny Ikarus pictures on iFunny Brazil22 dezembro 2024
Ikarus memes. Best Collection of funny Ikarus pictures on iFunny Brazil22 dezembro 2024 -
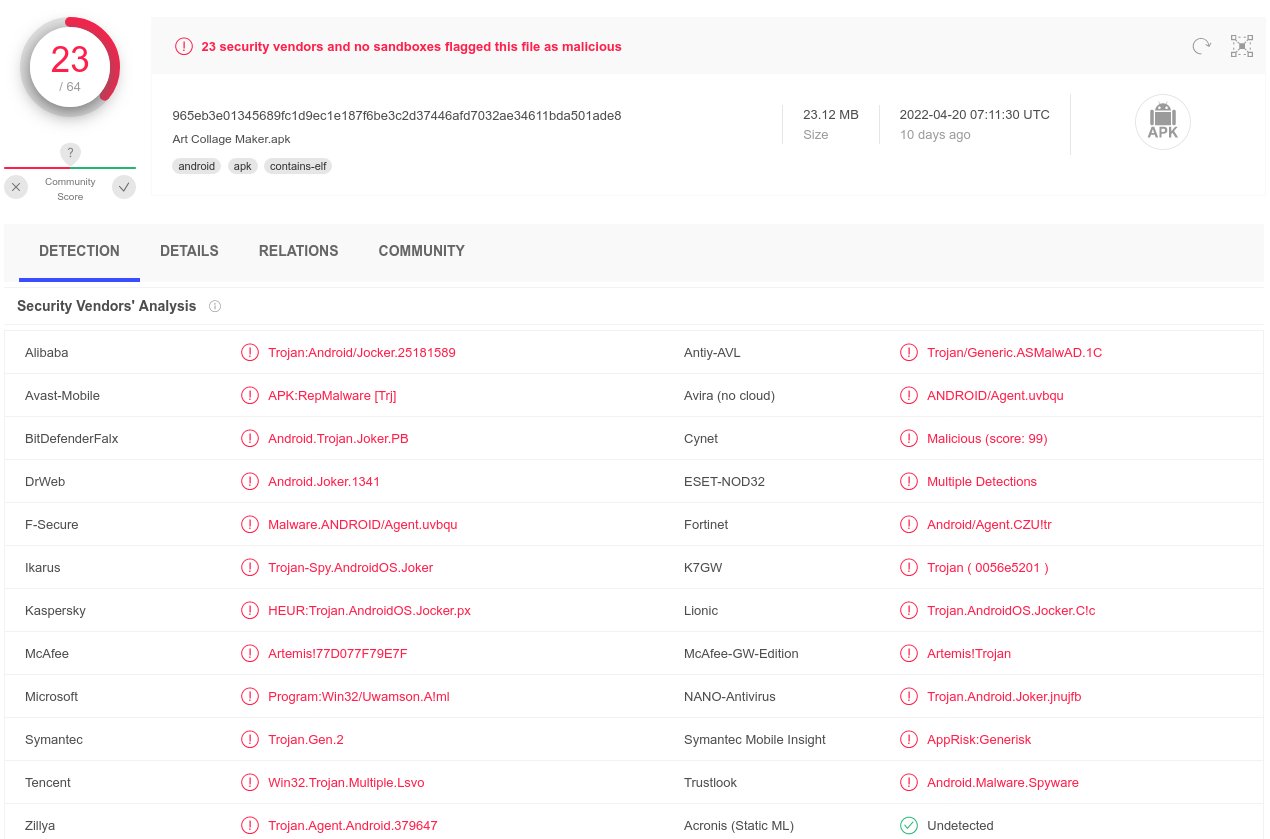 MalwareHunterTeam on X: While we recently tweeted mostly about those usury & spyware 2-in-1 apps in Play, it's still full of different normal malware/junk/etc too. Good example: ~a month after @ReBensk tweeted22 dezembro 2024
MalwareHunterTeam on X: While we recently tweeted mostly about those usury & spyware 2-in-1 apps in Play, it's still full of different normal malware/junk/etc too. Good example: ~a month after @ReBensk tweeted22 dezembro 2024 -
 How To Remove Trojan Vundo (Trojan:Win32/Vundo And TR/Drop.Vundo)22 dezembro 2024
How To Remove Trojan Vundo (Trojan:Win32/Vundo And TR/Drop.Vundo)22 dezembro 2024 -
 City of Troy Greek Mythology Travel Print Trojan Horse - Norway22 dezembro 2024
City of Troy Greek Mythology Travel Print Trojan Horse - Norway22 dezembro 2024 -
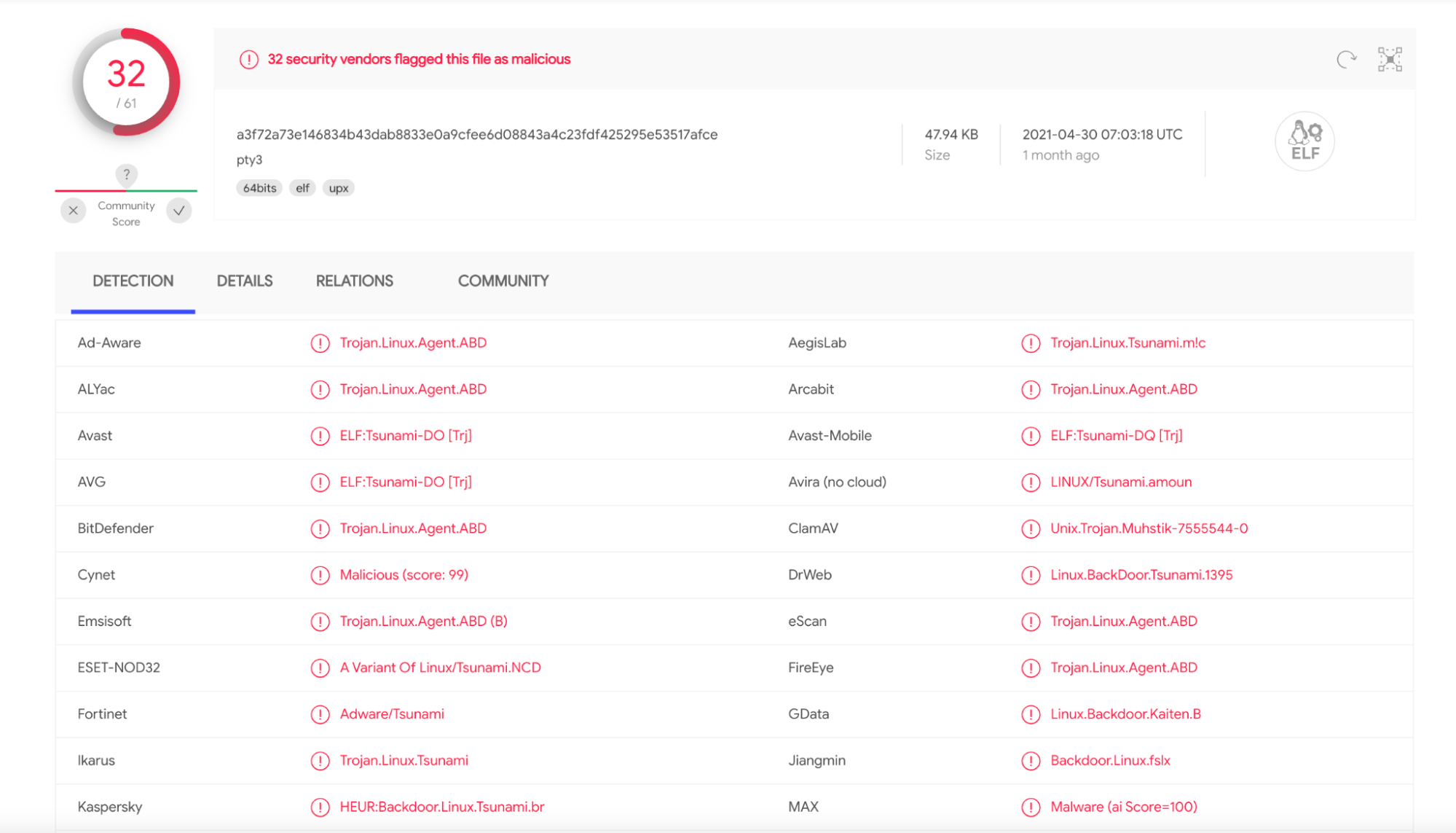 Hands-On Muhstik Botnet: crypto-mining attacks targeting Kubernetes – Sysdig22 dezembro 2024
Hands-On Muhstik Botnet: crypto-mining attacks targeting Kubernetes – Sysdig22 dezembro 2024
você pode gostar
-
 Nova Skin Gifts & Merchandise for Sale22 dezembro 2024
Nova Skin Gifts & Merchandise for Sale22 dezembro 2024 -
 Benriya Saitou-san Fanart by ijunk30 on Newgrounds22 dezembro 2024
Benriya Saitou-san Fanart by ijunk30 on Newgrounds22 dezembro 2024 -
 House of the Dragon Episode 5 Trailer Sets Up Another Bloody Game of Thrones Wedding22 dezembro 2024
House of the Dragon Episode 5 Trailer Sets Up Another Bloody Game of Thrones Wedding22 dezembro 2024 -
 X 上的Manga Mogura RE:「Kaiko sareta Ankoku Heishi (30-dai) no22 dezembro 2024
X 上的Manga Mogura RE:「Kaiko sareta Ankoku Heishi (30-dai) no22 dezembro 2024 -
 Personalized Your Name Soundtrack Kimi no Na wa from Studio Ghibli 30-Note Wind-Up Music Box Gift (Wooden)22 dezembro 2024
Personalized Your Name Soundtrack Kimi no Na wa from Studio Ghibli 30-Note Wind-Up Music Box Gift (Wooden)22 dezembro 2024 -
 Chess online - Play chess96022 dezembro 2024
Chess online - Play chess96022 dezembro 2024 -
 Wandinha Addams se apaixonaria discretamente por você?22 dezembro 2024
Wandinha Addams se apaixonaria discretamente por você?22 dezembro 2024 -
 como blindar um carro no gta san andreas22 dezembro 2024
como blindar um carro no gta san andreas22 dezembro 2024 -
 Hajime no Ippo - Recomendación anime - Hanami Dango22 dezembro 2024
Hajime no Ippo - Recomendación anime - Hanami Dango22 dezembro 2024 -
 Besiktas jk hi-res stock photography and images - Alamy22 dezembro 2024
Besiktas jk hi-res stock photography and images - Alamy22 dezembro 2024