Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Last updated 22 dezembro 2024

HackMag – Page 2 – Security, malware, coding, devops
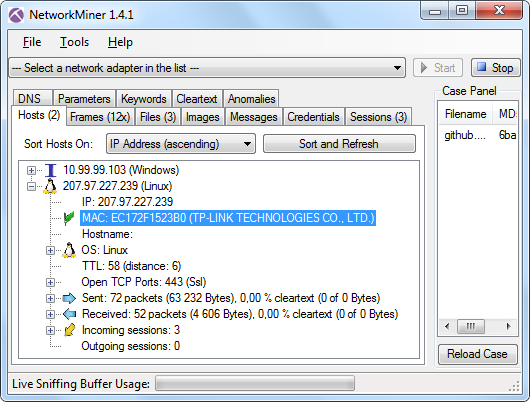
Forensics of Chinese MITM on GitHub

Xiangyu Qi - CatalyzeX
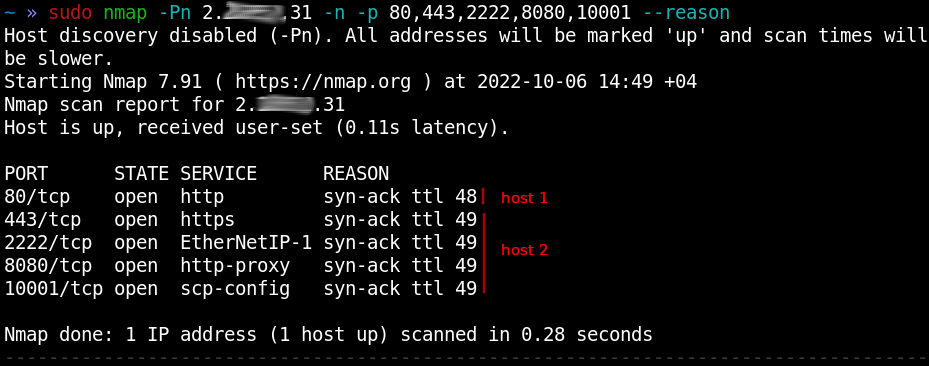
Kung fu enumeration. Data collection in attacked systems – HackMag
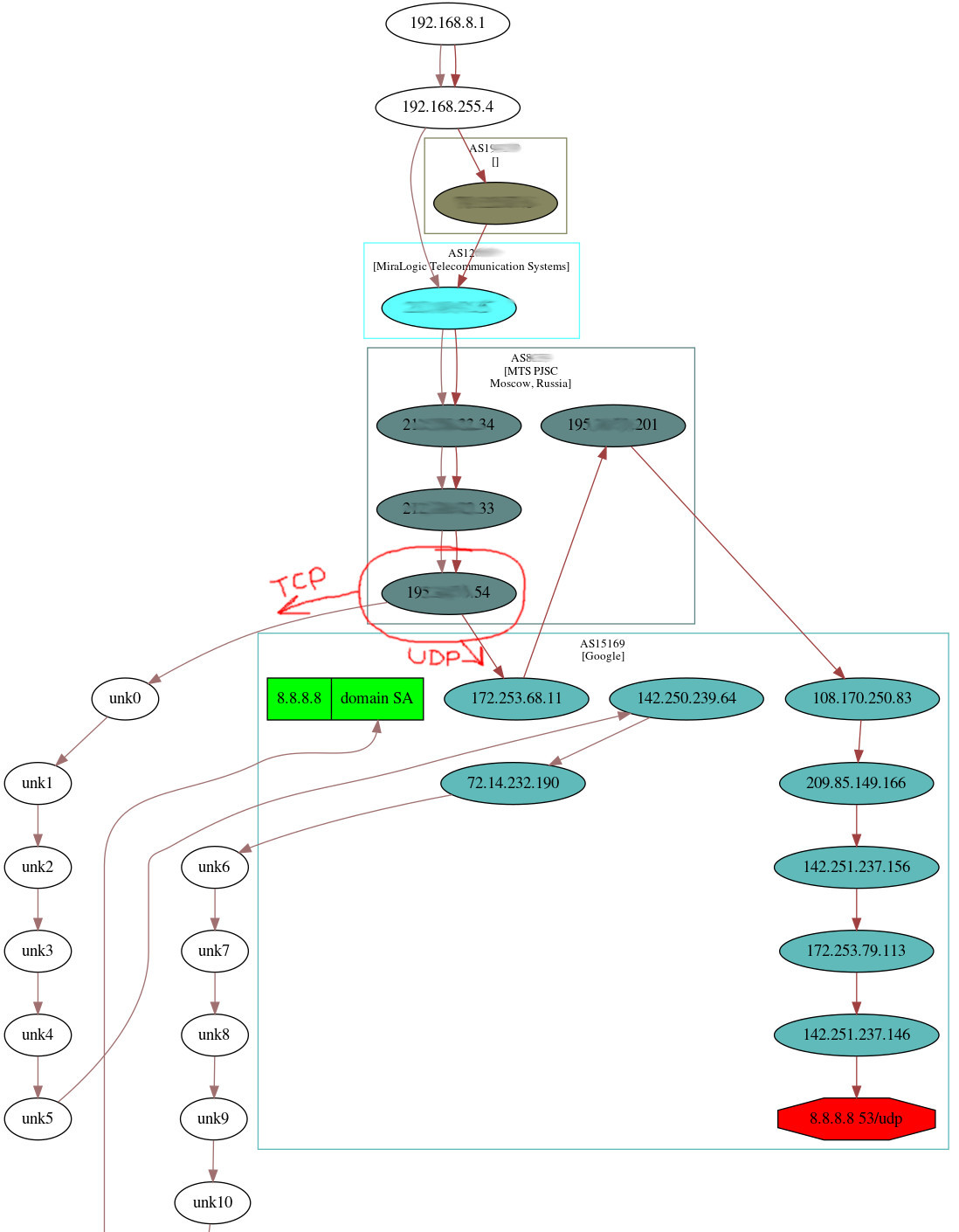
Kung fu enumeration. Data collection in attacked systems – HackMag

Indiana systems falling prey to increasing hacks into medical records
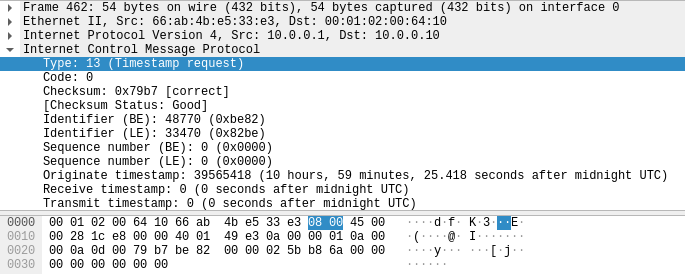
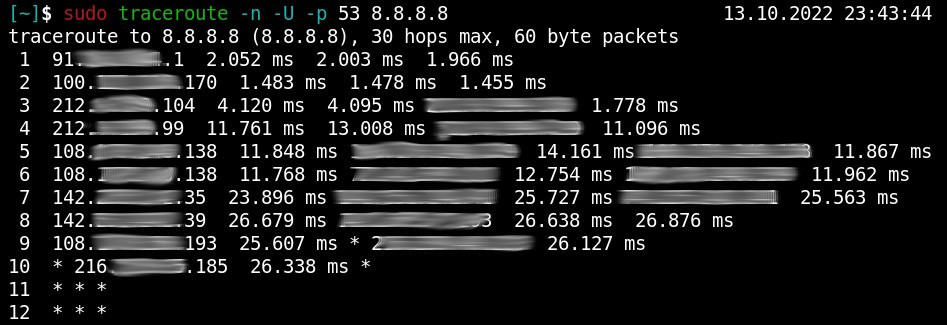
Kung fu enumeration. Data collection in attacked systems – HackMag

X BLOCK effective ADVANCED TECHNIQUE - Kung Fu Report
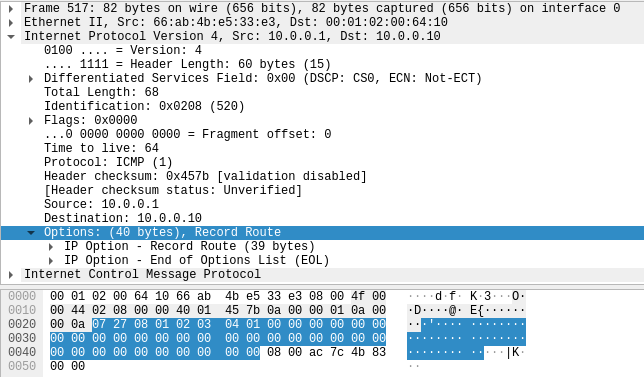
Kung fu enumeration. Data collection in attacked systems – HackMag

Subterfuge (Man-in-the-Middle Attack Framework) - Hacking Articles
Recomendado para você
-
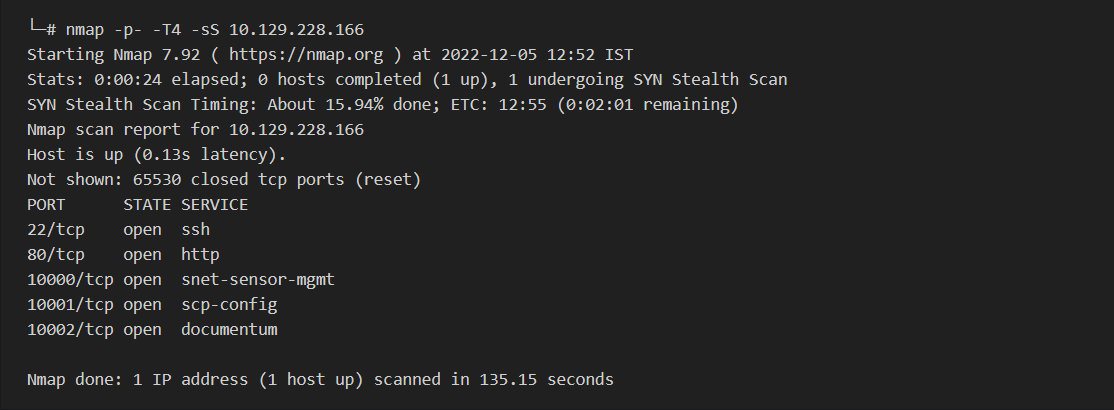 HTB University CTF 2022 — Cloud — Enchanted, by Akshay Shinde22 dezembro 2024
HTB University CTF 2022 — Cloud — Enchanted, by Akshay Shinde22 dezembro 2024 -
 Snarferman22 dezembro 2024
Snarferman22 dezembro 2024 -
 인류의 조상일지도 모르는 존재, 빅풋 SCP - 100022 dezembro 2024
인류의 조상일지도 모르는 존재, 빅풋 SCP - 100022 dezembro 2024 -
 10001% correct view of the AFSPECWAR career fields : r/Pararescue22 dezembro 2024
10001% correct view of the AFSPECWAR career fields : r/Pararescue22 dezembro 2024 -
 27/3 Seaguy Week! Captain Lotharius - Xanaduum22 dezembro 2024
27/3 Seaguy Week! Captain Lotharius - Xanaduum22 dezembro 2024 -
SCP - 10001 (@JKweesley32757) / X22 dezembro 2024
-
![The Mads [MST3K Fan Art]](https://i2.wp.com/www.rowsdowr.com/wp-content/uploads/2011/07/media_httpfc09deviant_nbumh1.jpg.scaled10001.jpg?resize=841%2C393) The Mads [MST3K Fan Art]22 dezembro 2024
The Mads [MST3K Fan Art]22 dezembro 2024 -
DesktopDinosaur🦖 on Instagram: Just wanted to show my own spin of the murder trio! They're not that different from their original designs but I just like the extra little flare it gives.22 dezembro 2024
-
 Muerte by Arfaxad, dark Paintings for sale, direct from the artist22 dezembro 2024
Muerte by Arfaxad, dark Paintings for sale, direct from the artist22 dezembro 2024 -
posts this then dissapears for another month* #fnaf #digital #dontyi22 dezembro 2024
você pode gostar
-
 Sega Genesis Collection - Wikipedia22 dezembro 2024
Sega Genesis Collection - Wikipedia22 dezembro 2024 -
 Defesa Siciliana: qual variante escolher para começar a jogar?22 dezembro 2024
Defesa Siciliana: qual variante escolher para começar a jogar?22 dezembro 2024 -
Papa Pizza, Pizza place22 dezembro 2024
-
classroom, Classroom of the Elite, Arisu Sakayanagi / Arisu Sakayanagi - pixiv22 dezembro 2024
-
God Of War 2 Original Ps2 Novo Lacrado Versão 2 Disco22 dezembro 2024
-
 Slither.io Mod Menu Version:54.0 Mega Mod Menu Made By ModsMinecraftgaming Invisible Body And Speed22 dezembro 2024
Slither.io Mod Menu Version:54.0 Mega Mod Menu Made By ModsMinecraftgaming Invisible Body And Speed22 dezembro 2024 -
 Imagens Fino PNG e Vetor, com Fundo Transparente Para Download Grátis22 dezembro 2024
Imagens Fino PNG e Vetor, com Fundo Transparente Para Download Grátis22 dezembro 2024 -
 Here is my map at 119 shrines. Can you spot the one I am missing? : r/botw22 dezembro 2024
Here is my map at 119 shrines. Can you spot the one I am missing? : r/botw22 dezembro 2024 -
 Inuyasha-Kanketsu-hen-inuyasha-the-final-act-21057636-1280…22 dezembro 2024
Inuyasha-Kanketsu-hen-inuyasha-the-final-act-21057636-1280…22 dezembro 2024 -
Sailor Moon Crystal - Portugal22 dezembro 2024





