a1), {(b1)-(c1)}, (d1), (e1), and {(f1)-(g1)} shows copy-move forged
Por um escritor misterioso
Last updated 22 dezembro 2024

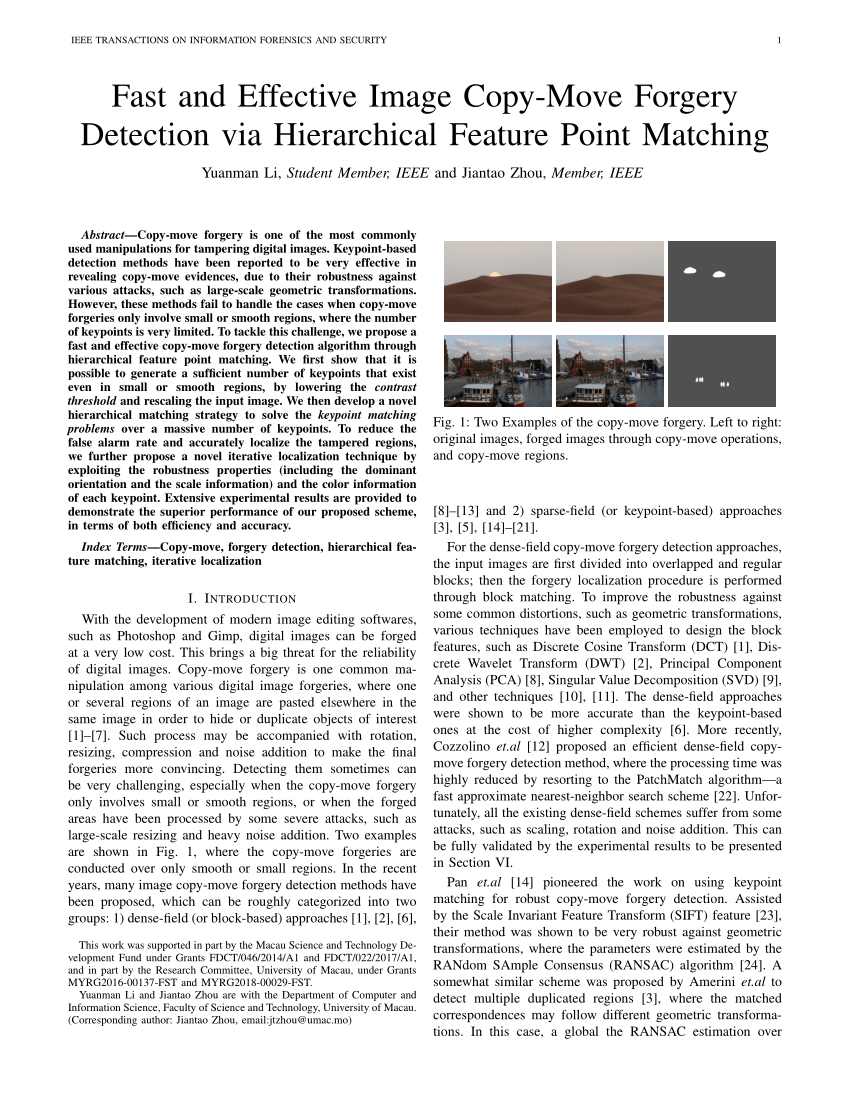
PDF) Fast and Effective Image Copy-Move Forgery Detection via Hierarchical Feature Point Matching

PDF] Copy-Move Forgery Detection Utilizing Local Binary Patterns

Accuracy (in the left side) and loss (in the right side) of the
Copy-move image forgery detection based on evolving circular domains coverage
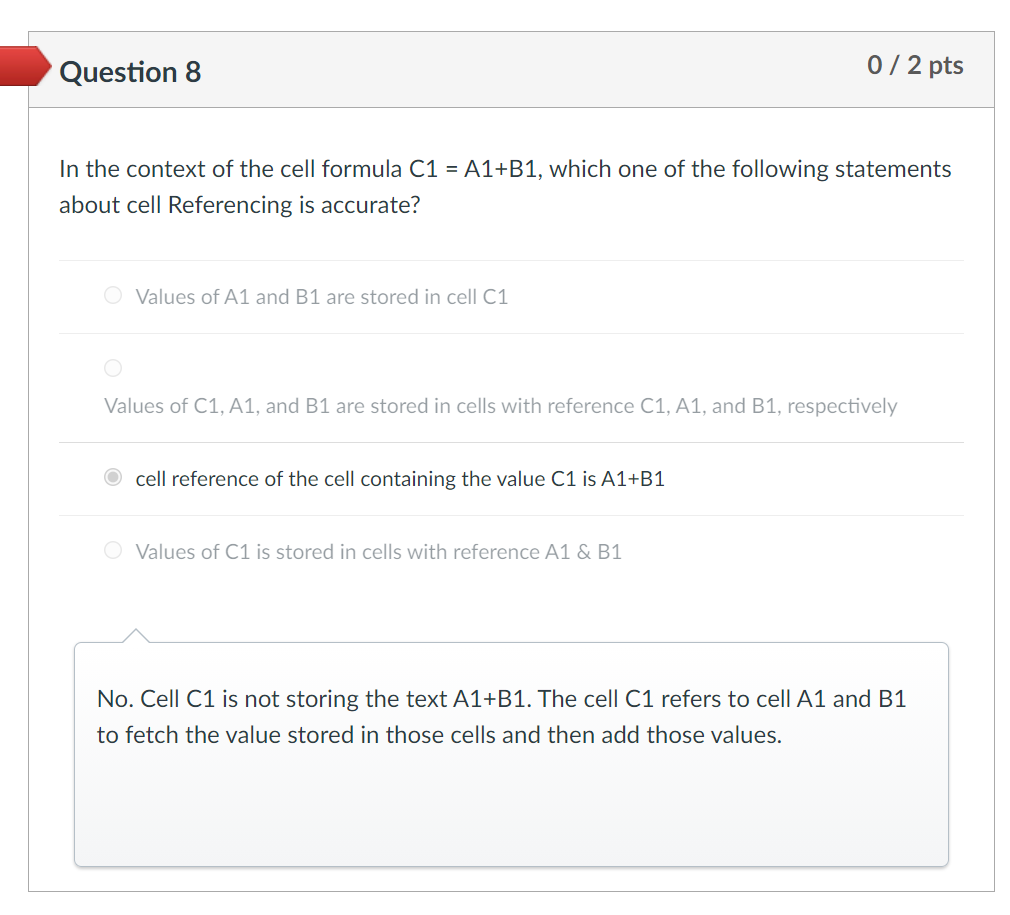
Solved Which one of the following formulas will work if
The first five examples for Copy-Move forgery detection: original

Copy-move forgery detection using binary discriminant features - ScienceDirect
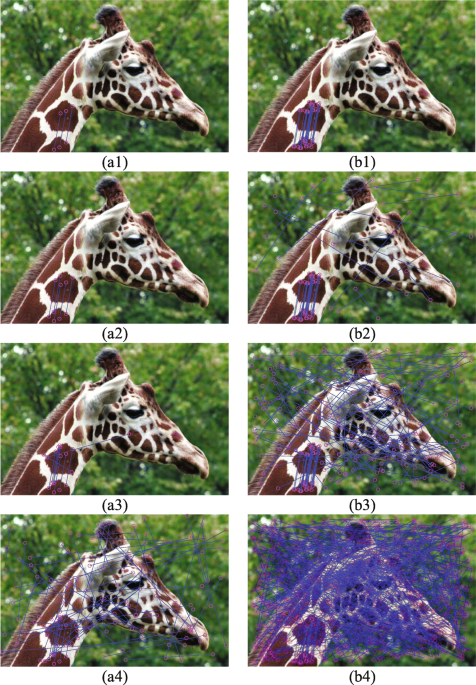
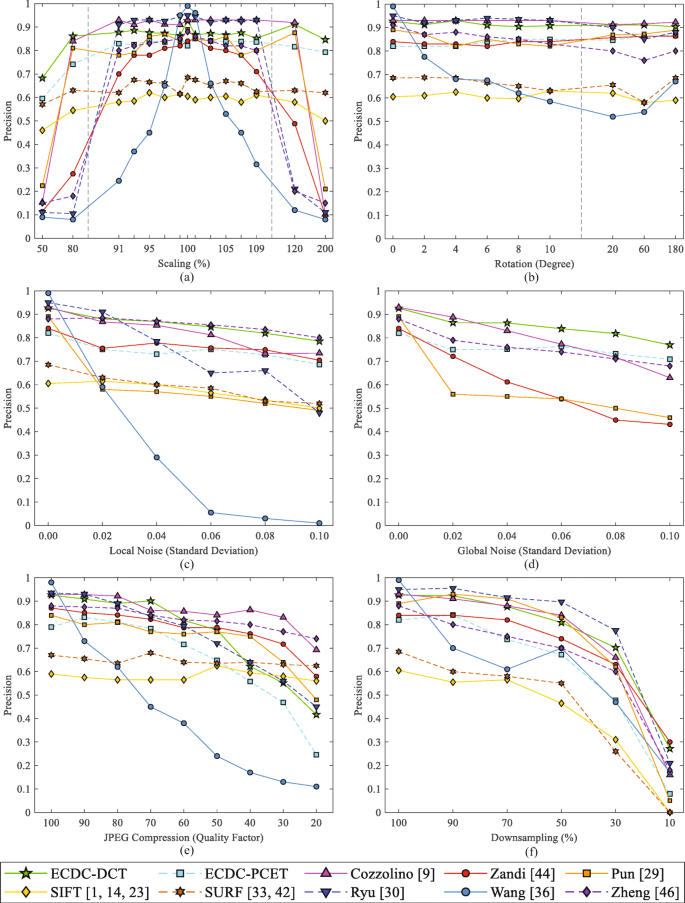
Copy-move image forgery detection based on evolving circular domains coverage
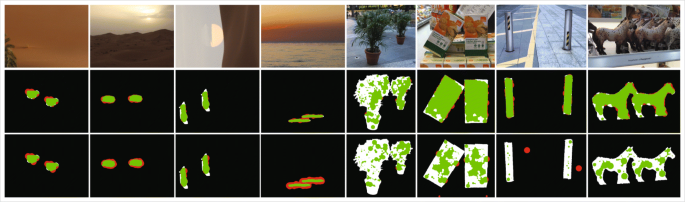
Copy-move image forgery detection based on evolving circular domains coverage
Recomendado para você
-
 Transformers G1: Powerdasher F1 Dasher and Decoy #12 Skids22 dezembro 2024
Transformers G1: Powerdasher F1 Dasher and Decoy #12 Skids22 dezembro 2024 -
 BenQ G1 digital camera boasts F1.8 lens, swivel-screen and modest price tag22 dezembro 2024
BenQ G1 digital camera boasts F1.8 lens, swivel-screen and modest price tag22 dezembro 2024 -
 Pre-Owned Vizio OEM Remote Control for VIZIO Smart TV D50x-G9 D65x-G4 D55x-G1 D40f-G9 D43f-F1 D70-F3 V505-G9 D32h-F1 P75-F1 D55x-G1 V405-G9 E75-F222 dezembro 2024
Pre-Owned Vizio OEM Remote Control for VIZIO Smart TV D50x-G9 D65x-G4 D55x-G1 D40f-G9 D43f-F1 D70-F3 V505-G9 D32h-F1 P75-F1 D55x-G1 V405-G9 E75-F222 dezembro 2024 -
 XRT136 Replace Remote Control fit for VIZIO Smart TV D50x-G9 D65x-G4 D55x-G1 D40f-G9 D43f-F1 D70-F3 V505-G9 D32h-F1 D24h-G9 E70-F3 D43-F1 V705-G322 dezembro 2024
XRT136 Replace Remote Control fit for VIZIO Smart TV D50x-G9 D65x-G4 D55x-G1 D40f-G9 D43f-F1 D70-F3 V505-G9 D32h-F1 D24h-G9 E70-F3 D43-F1 V705-G322 dezembro 2024 -
 Griip G1 Carbon fiber 1000 cart powered by the Aprilia RSV4 superbikes V4 engine.22 dezembro 2024
Griip G1 Carbon fiber 1000 cart powered by the Aprilia RSV4 superbikes V4 engine.22 dezembro 2024 -
 IIVVERR 20mm F1/2 G1/2 Thread 1.5M Long Shower Hose Pipe for Hand Held Showerhead (20mm F1 / 2' 'G1 / 2' 'Tubo de manguera de ducha larga de 1.5M22 dezembro 2024
IIVVERR 20mm F1/2 G1/2 Thread 1.5M Long Shower Hose Pipe for Hand Held Showerhead (20mm F1 / 2' 'G1 / 2' 'Tubo de manguera de ducha larga de 1.5M22 dezembro 2024 -
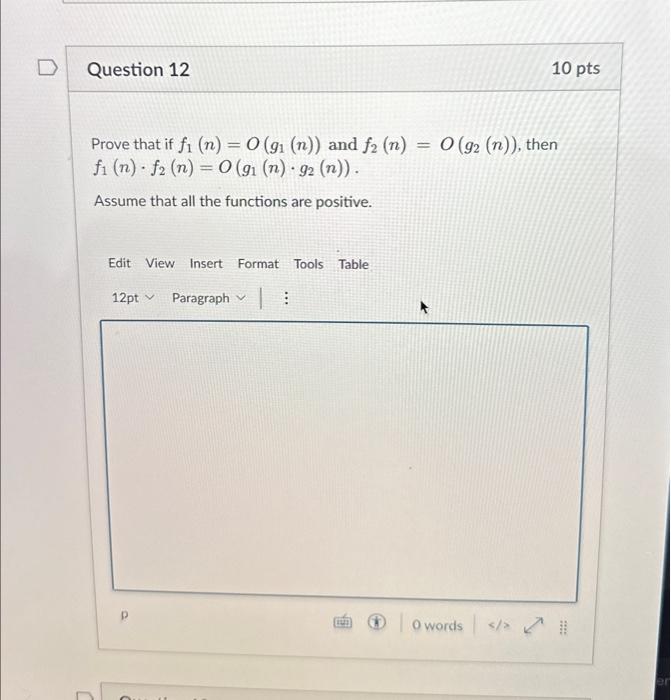
Solved Prove that if f1(n)=O(g1(n)) and f2(n)=O(g2(n)), then22 dezembro 2024
-
 Lot of 5 JVC G1-90 F1-90 Sealed Blank Cassettes Type 1 Japan22 dezembro 2024
Lot of 5 JVC G1-90 F1-90 Sealed Blank Cassettes Type 1 Japan22 dezembro 2024 -
 F1: Lewis Hamilton Wins United States Grand Prix (PHOTOS) - Racing News22 dezembro 2024
F1: Lewis Hamilton Wins United States Grand Prix (PHOTOS) - Racing News22 dezembro 2024 -
 20mm F1/2 G1/2 Thread 1.5M Length PVC Handheld Shower Hose Pipe White - Bed Bath & Beyond - 1846368522 dezembro 2024
20mm F1/2 G1/2 Thread 1.5M Length PVC Handheld Shower Hose Pipe White - Bed Bath & Beyond - 1846368522 dezembro 2024
você pode gostar
-
 Fairy tail, anime, erza, fairy tail, gray, happy, lucy, natsu, HD phone wallpaper22 dezembro 2024
Fairy tail, anime, erza, fairy tail, gray, happy, lucy, natsu, HD phone wallpaper22 dezembro 2024 -
 An Orchestral Tribute to the Notorious B.I.G. · Lincoln Center22 dezembro 2024
An Orchestral Tribute to the Notorious B.I.G. · Lincoln Center22 dezembro 2024 -
 Alfabeto Ilustrado Turma da Mônica - Zé Vampir22 dezembro 2024
Alfabeto Ilustrado Turma da Mônica - Zé Vampir22 dezembro 2024 -
 100+ Social Media Acronyms and Slang You Must Know – PromoRepublic22 dezembro 2024
100+ Social Media Acronyms and Slang You Must Know – PromoRepublic22 dezembro 2024 -
Flork Memes Stickers for Android - Download22 dezembro 2024
-
 Crunchyroll to Stream That Time I Got Reincarnated as a Slime22 dezembro 2024
Crunchyroll to Stream That Time I Got Reincarnated as a Slime22 dezembro 2024 -
 🥇Forza Horizon 4: Ultimate +ALL DLC, +Steam friends✔️22 dezembro 2024
🥇Forza Horizon 4: Ultimate +ALL DLC, +Steam friends✔️22 dezembro 2024 -
 Goku Super Full Power Saiyan 4: Limit Breakthrough é a nova invenção de Dragon Ball Heroes22 dezembro 2024
Goku Super Full Power Saiyan 4: Limit Breakthrough é a nova invenção de Dragon Ball Heroes22 dezembro 2024 -
Piercing na sobrancelha que eu amoooo fazer, o que acharam? #piercing22 dezembro 2024
-
 تنزيل Jogos de futebol off-line 1.9 من أجل Android مجانًا - Uoldown22 dezembro 2024
تنزيل Jogos de futebol off-line 1.9 من أجل Android مجانًا - Uoldown22 dezembro 2024