Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Last updated 22 dezembro 2024

Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

Could Brute Force Attacks in a Post-Quantum Computing World Lessen

115 cybersecurity statistics + trends to know in 2024
Fileless Malware Detection with Sysdig Secure – Sysdig

Cyber Reconnaissance Techniques, March 2021

Computer security - Wikipedia

What is a Fileless Malware Attack (with examples)

Five Reasons Memory-Based Cyberattacks Continue to Succeed

How Hackers Rob Banks, 2018-05-21

Privilege Escalation Attack and Defense Explained

Red Teams vs. Blue Teams: What's The Difference?

CrowdStrike Uses Similarity Search to Detect Script-Based Malware

Cyber Attack - an overview
Types of Cyber Attacks - GeeksforGeeks
Recomendado para você
-
 Evade Script/GUI Review22 dezembro 2024
Evade Script/GUI Review22 dezembro 2024 -
Evade-script/script at main · Lux11111111/Evade-script · GitHub22 dezembro 2024
-
 Evade script - (Godmode, FullBright)22 dezembro 2024
Evade script - (Godmode, FullBright)22 dezembro 2024 -
evade script|TikTok Search22 dezembro 2024
-
![Selling] 🔥the best external lol script🔥, ✓undetected](https://i.imgur.com/2mBXxFQ.jpg) Selling] 🔥the best external lol script🔥, ✓undetected22 dezembro 2024
Selling] 🔥the best external lol script🔥, ✓undetected22 dezembro 2024 -
 CanHub Evade Script Download 100% Free22 dezembro 2024
CanHub Evade Script Download 100% Free22 dezembro 2024 -
 Security warning: Beep malware can evade detection22 dezembro 2024
Security warning: Beep malware can evade detection22 dezembro 2024 -
 Reference attack model: an attacker embeds a malicious script into22 dezembro 2024
Reference attack model: an attacker embeds a malicious script into22 dezembro 2024 -
 lol script guard22 dezembro 2024
lol script guard22 dezembro 2024 -
 Malicious Python Package Uses Unicode Trickery to Evade Detection22 dezembro 2024
Malicious Python Package Uses Unicode Trickery to Evade Detection22 dezembro 2024
você pode gostar
-
 1 Hour of Wise Mystical Tree_哔哩哔哩_bilibili22 dezembro 2024
1 Hour of Wise Mystical Tree_哔哩哔哩_bilibili22 dezembro 2024 -
 Whats the best fruit for angel v4 user? : r/bloxfruits22 dezembro 2024
Whats the best fruit for angel v4 user? : r/bloxfruits22 dezembro 2024 -
 Jogo Barbie Bike Game no Jogos 36022 dezembro 2024
Jogo Barbie Bike Game no Jogos 36022 dezembro 2024 -
 Smothered Mate Examples22 dezembro 2024
Smothered Mate Examples22 dezembro 2024 -
 E se a Coca Cola22 dezembro 2024
E se a Coca Cola22 dezembro 2024 -
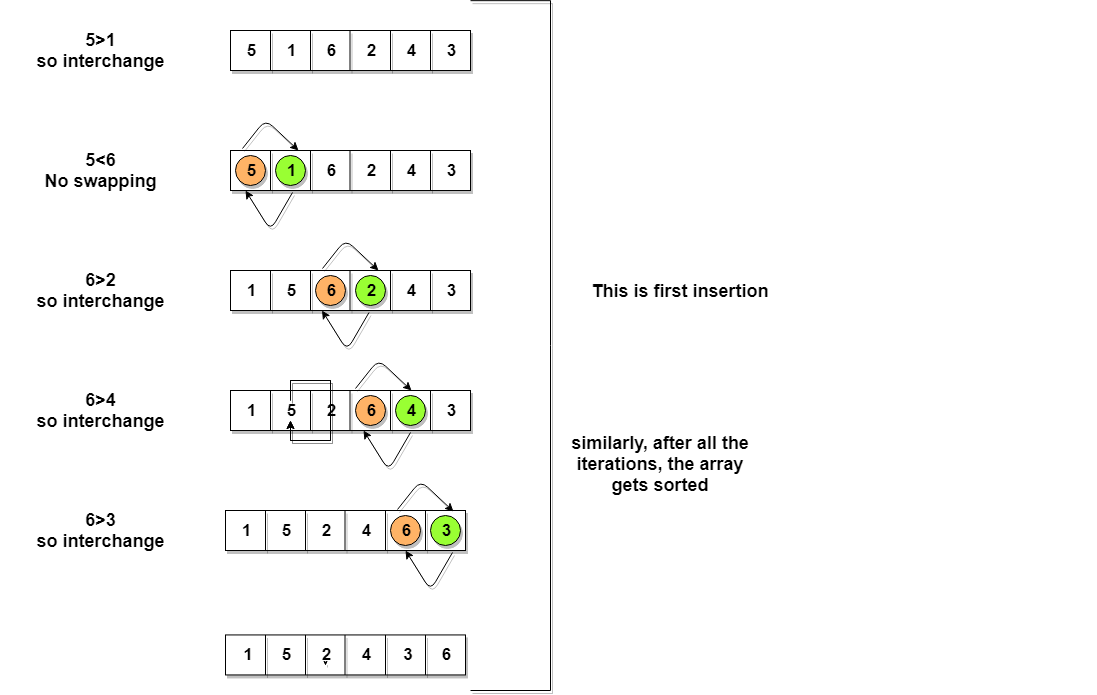 Bubble Sort, Data Structures Tutorial22 dezembro 2024
Bubble Sort, Data Structures Tutorial22 dezembro 2024 -
 p16-sign.tiktokcdn-us.com/tos-useast5-p-0068-tx/5122 dezembro 2024
p16-sign.tiktokcdn-us.com/tos-useast5-p-0068-tx/5122 dezembro 2024 -
How many rooks can be placed on a chessboard so that no two rooks are attacking each other? - Quora22 dezembro 2024
-
 Tower Defense Simulator Wiki - Shoot Rifle, HD Png Download , Transparent Png Image - PNGitem22 dezembro 2024
Tower Defense Simulator Wiki - Shoot Rifle, HD Png Download , Transparent Png Image - PNGitem22 dezembro 2024 -
 Shrek and Shadow OTP Pin for Sale by witapepsi22 dezembro 2024
Shrek and Shadow OTP Pin for Sale by witapepsi22 dezembro 2024

