Bits, Please!: Android linux kernel privilege escalation vulnerability and exploit (CVE-2014-4322)
Por um escritor misterioso
Last updated 10 novembro 2024
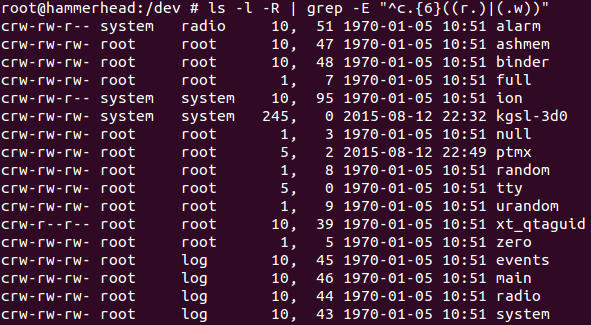

Linux Privilege Escalation With Kernel Exploit – [8572.c] - Yeah Hub

TPS App Sec – Page 2 – TPS ASAG – Application Security Awareness Group

Linux Privilege Escalation via snapd using dirty_sock exploit and

TPS App Sec – Page 2 – TPS ASAG – Application Security Awareness Group
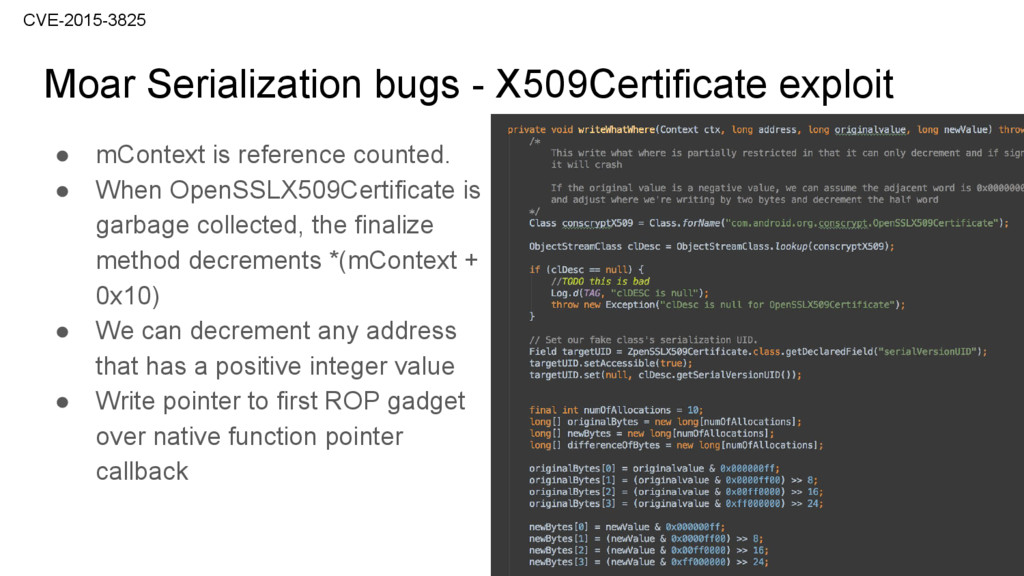
Current State of Android Privilege Escalation - Speaker Deck
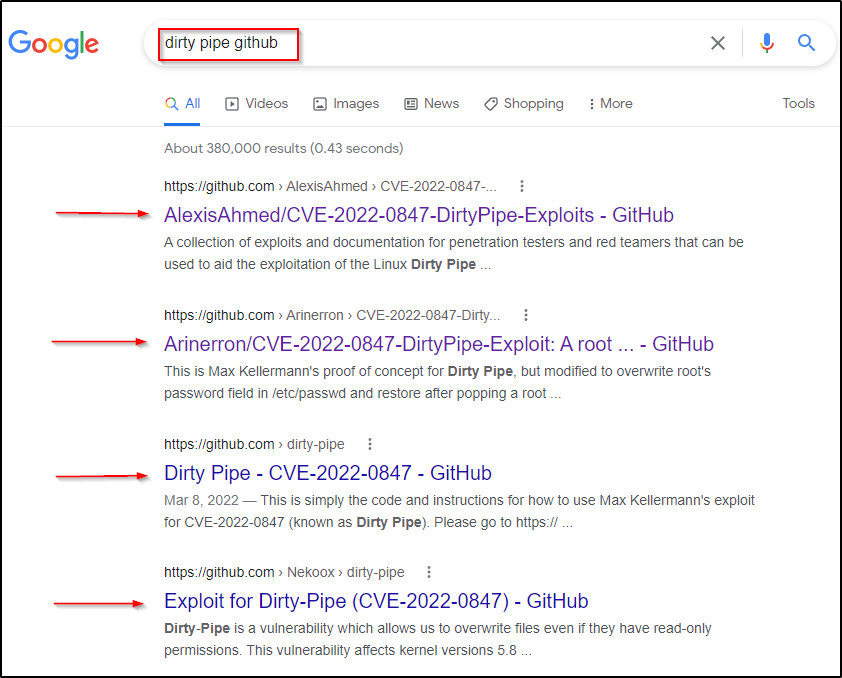
Kernel Exploits – Linux Privilege Escalation

Kernel Exploits – Linux Privilege Escalation
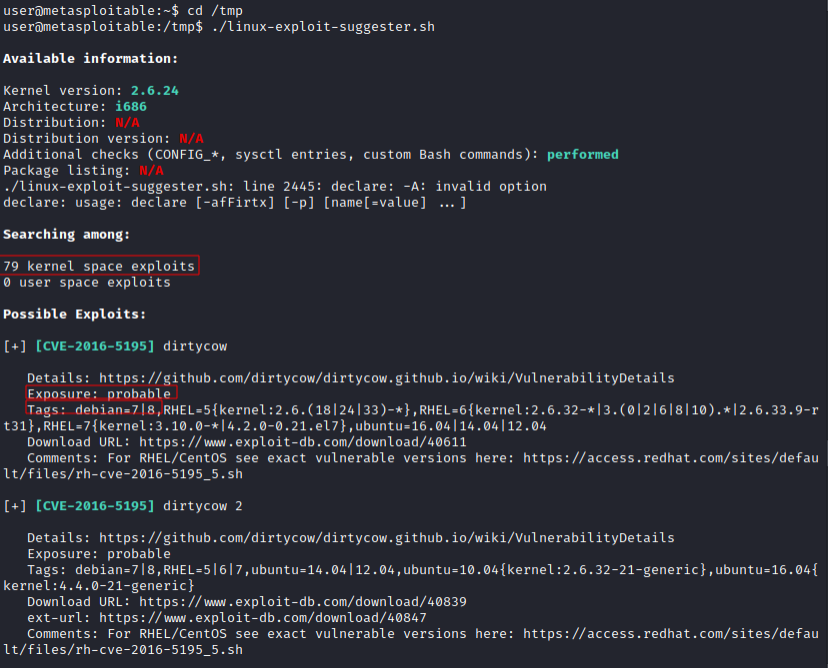
Linux Privilege Escalation: Linux kernel / distribution exploits

POODLE SSL Vulnerability Now Attacking TLS Security Protocol

Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE_POKEDATA' Race
Recomendado para você
-
 Friv®10 novembro 2024
Friv®10 novembro 2024 -
 Papa's Scooperia - 🕹️ Online Game10 novembro 2024
Papa's Scooperia - 🕹️ Online Game10 novembro 2024 -
 GoGy Games - Play Free Online Games10 novembro 2024
GoGy Games - Play Free Online Games10 novembro 2024 -
 6 sites com jogos fantásticos para te divertires!10 novembro 2024
6 sites com jogos fantásticos para te divertires!10 novembro 2024 -
 Papa's Pizzeria - Play Papa's Pizzeria at Friv EZ10 novembro 2024
Papa's Pizzeria - Play Papa's Pizzeria at Friv EZ10 novembro 2024 -
 Resort Empire - 🕹️ Online Game10 novembro 2024
Resort Empire - 🕹️ Online Game10 novembro 2024 -
Desbloqueando uma memória sua #nostalgia #jogos #friv #memoriadesbloqu10 novembro 2024
-
 Gazo10 novembro 2024
Gazo10 novembro 2024 -
 How to: Flash Google Pixel Factory Images10 novembro 2024
How to: Flash Google Pixel Factory Images10 novembro 2024 -
 O CLICK JOGOS ACABA EM 1 MÊS, COMO SALVAR OS JOGOS (+Relembrando10 novembro 2024
O CLICK JOGOS ACABA EM 1 MÊS, COMO SALVAR OS JOGOS (+Relembrando10 novembro 2024
você pode gostar
-
 Pokémon TCG Value Watch: Pokémon GO In July 202310 novembro 2024
Pokémon TCG Value Watch: Pokémon GO In July 202310 novembro 2024 -
 portrait of Rowena Ravenclaw as an embodiment of, Stable Diffusion10 novembro 2024
portrait of Rowena Ravenclaw as an embodiment of, Stable Diffusion10 novembro 2024 -
 Characters appearing in Goblin Slayer Anime10 novembro 2024
Characters appearing in Goblin Slayer Anime10 novembro 2024 -
 The Game Awards 2022 Winners List, With Live Updates10 novembro 2024
The Game Awards 2022 Winners List, With Live Updates10 novembro 2024 -
 Panama vs. El Salvador Highlights, CONCACAF Gold Cup10 novembro 2024
Panama vs. El Salvador Highlights, CONCACAF Gold Cup10 novembro 2024 -
 33 Years After Suffering Devastating Loss, Mike Tyson Makes an10 novembro 2024
33 Years After Suffering Devastating Loss, Mike Tyson Makes an10 novembro 2024 -
 Análise de Personagens - Alola - Trial Captain Mallow10 novembro 2024
Análise de Personagens - Alola - Trial Captain Mallow10 novembro 2024 -
 Frizzle Fraz 1 - Jogo Grátis Online10 novembro 2024
Frizzle Fraz 1 - Jogo Grátis Online10 novembro 2024 -
 Retão_no_Grau_🚀 on X: Minha hora vai chegar10 novembro 2024
Retão_no_Grau_🚀 on X: Minha hora vai chegar10 novembro 2024 -
 BLOOD LAD- Official English Clip- Staz Attacks! Coming 9/2/1410 novembro 2024
BLOOD LAD- Official English Clip- Staz Attacks! Coming 9/2/1410 novembro 2024
