Hundreds of Microsoft sub-domains open to hijacking
Por um escritor misterioso
Last updated 22 dezembro 2024

Experts demonstrated that hundreds of Microsoft sub-domains could potentially be hijacked and abused to deliver malware and for phishing attacks

Microsoft has a subdomain hijacking problem

From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud
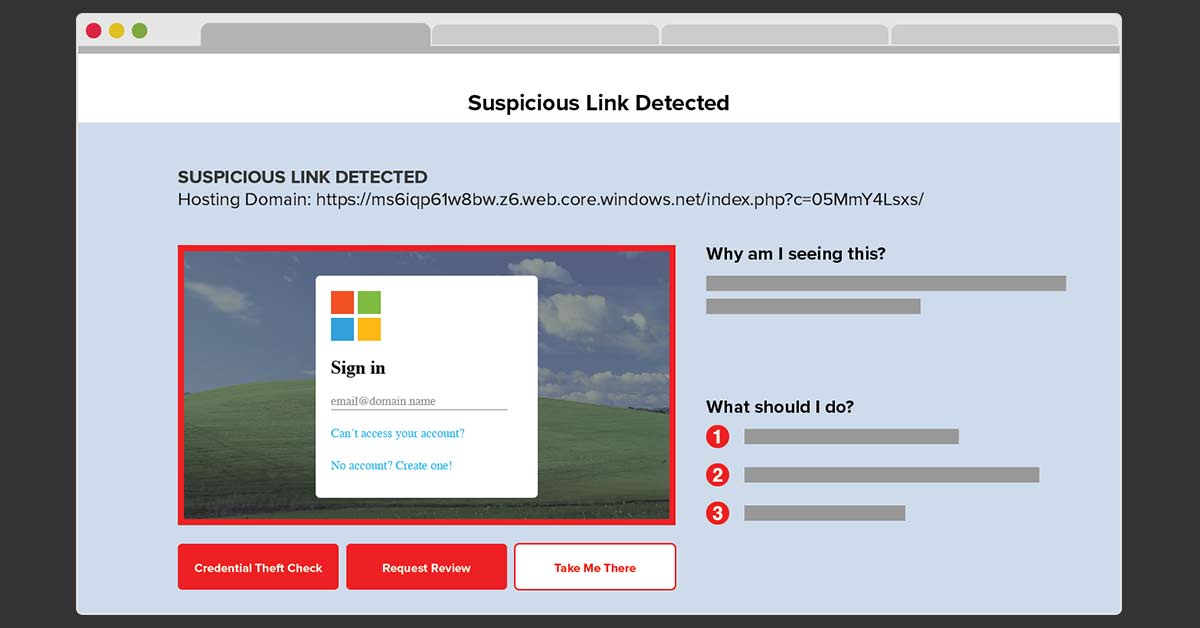
How to Protect Against Microsoft Subdomain Takeover - GreatHorn

A Microsoft 365 feature can ransom files on SharePoint and OneDriveCould

Subdomain takeover attacks on the rise and harder to monitor - Help Net Security

Everything you wanted to know about trusts with AWS Managed Microsoft AD
How Hackers Attack Subdomains and How to Protect Them
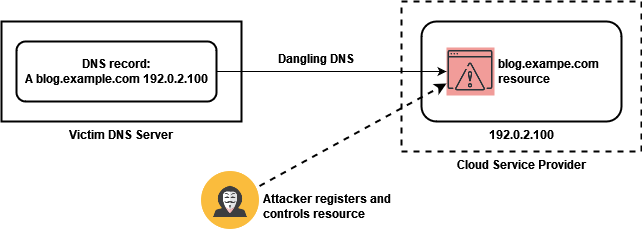
Thousands of Organizations Vulnerable to Subdomain Hijacking – Certitude Blog
Subdomain Hijacking: The Domain's Silent Danger

Crooks compromise Microsoft Exchange servers to hijack internal email chains
Subdomain Hijacking: The Domain's Silent Danger

Bolster Subdomain Hijacking: How to identify subdomains at risk
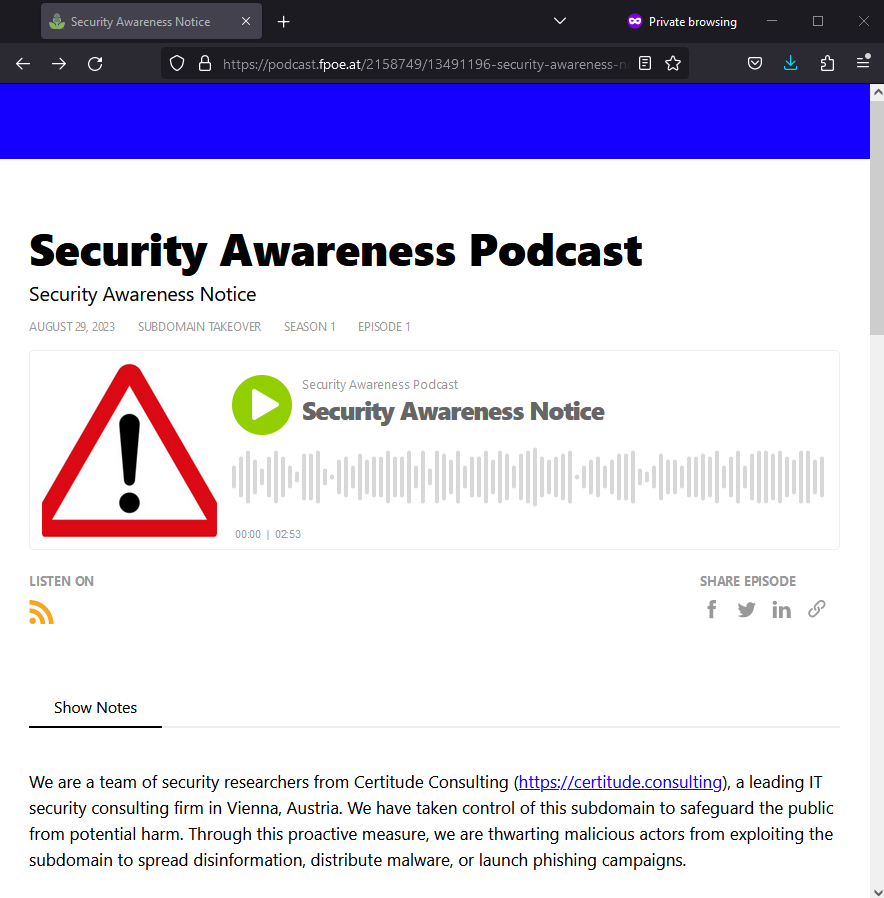
Thousands of Organizations Vulnerable to Subdomain Hijacking – Certitude Blog

New Microsoft Security 'Nightmare': Users Warned Your Passwords Are Now At Risk

How Do Attackers Hijack Old Domains and Subdomains?
Recomendado para você
-
DigDig.IO Minimap22 dezembro 2024
-
 Digdig.io Tips and Tricks22 dezembro 2024
Digdig.io Tips and Tricks22 dezembro 2024 -
 How to get DigDig.io Cheats and how to use GreasyFork22 dezembro 2024
How to get DigDig.io Cheats and how to use GreasyFork22 dezembro 2024 -
 555 Timer - Timer22 dezembro 2024
555 Timer - Timer22 dezembro 2024 -
General Assembly22 dezembro 2024
-
 what do y'all think about my map? 🤔 code: 1213-8312-9625 #viral #fort, meme box fight22 dezembro 2024
what do y'all think about my map? 🤔 code: 1213-8312-9625 #viral #fort, meme box fight22 dezembro 2024 -
.jpg?width=960&name=Shielding%20APIs%20that%20Service%20Mobile%20Apps%20Part%201%20-%20Why%20v2%20(3).jpg) Mobile Application Shielding22 dezembro 2024
Mobile Application Shielding22 dezembro 2024 -
 Slack Shared Channels: The Ultimate Cheat Sheet 202322 dezembro 2024
Slack Shared Channels: The Ultimate Cheat Sheet 202322 dezembro 2024 -
 Funny Irish Gifts Ireland Poster Irish Sayings Digital22 dezembro 2024
Funny Irish Gifts Ireland Poster Irish Sayings Digital22 dezembro 2024 -
 We Tried 4 Best Veed Alternatives - Here's Our Detailed Comparison22 dezembro 2024
We Tried 4 Best Veed Alternatives - Here's Our Detailed Comparison22 dezembro 2024
você pode gostar
-
 Anime – Tengen Toppa Gurren Lagann Wallpaper22 dezembro 2024
Anime – Tengen Toppa Gurren Lagann Wallpaper22 dezembro 2024 -
 Arquidiocese de Maringá22 dezembro 2024
Arquidiocese de Maringá22 dezembro 2024 -
 KAER GT 730 Graphics Card, 4GB DDR3, DirectX 11 128 Bit, VGA/DVI-D/HDMI, PCI Express 2.0 x 16, Nvidia Video Card, Computer GPU22 dezembro 2024
KAER GT 730 Graphics Card, 4GB DDR3, DirectX 11 128 Bit, VGA/DVI-D/HDMI, PCI Express 2.0 x 16, Nvidia Video Card, Computer GPU22 dezembro 2024 -
 Roblox Peace Love T-Shirt22 dezembro 2024
Roblox Peace Love T-Shirt22 dezembro 2024 -
Can the Xbox Series X play Fortnite? - Quora22 dezembro 2024
-
 Nintendo Switch Online Patch Brings Back Ocarina of Time's Missing22 dezembro 2024
Nintendo Switch Online Patch Brings Back Ocarina of Time's Missing22 dezembro 2024 -
 Dragon Ball Super: Broly is an Action-Packed Triumph with a Surprising Amount of Heart, by M S Rayed, UpThrust.co22 dezembro 2024
Dragon Ball Super: Broly is an Action-Packed Triumph with a Surprising Amount of Heart, by M S Rayed, UpThrust.co22 dezembro 2024 -
 Spiritual Lollygagging – six5mom22 dezembro 2024
Spiritual Lollygagging – six5mom22 dezembro 2024 -
 Friday The 13th Wallpaper Mobile - iXpap22 dezembro 2024
Friday The 13th Wallpaper Mobile - iXpap22 dezembro 2024 -
wfuzz/wordlist/fuzzdb/discovery/PredictableRes/raft-small-words-lowercase.txt at master · tjomk/wfuzz · GitHub22 dezembro 2024

