Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
Por um escritor misterioso
Last updated 22 dezembro 2024

Malware Analysis: Steps & Examples - CrowdStrike
TryHackMe : AOC 2022 [Day 12] Malware Analysis Forensic McBlue to the REVscue!, by JAMS_

Machine learning in cybersecurity: a comprehensive survey - Dipankar Dasgupta, Zahid Akhtar, Sajib Sen, 2022

PDF) Dynamic malware detection and phylogeny analysis using process mining

Exploring Prompt Injection Attacks, NCC Group Research Blog
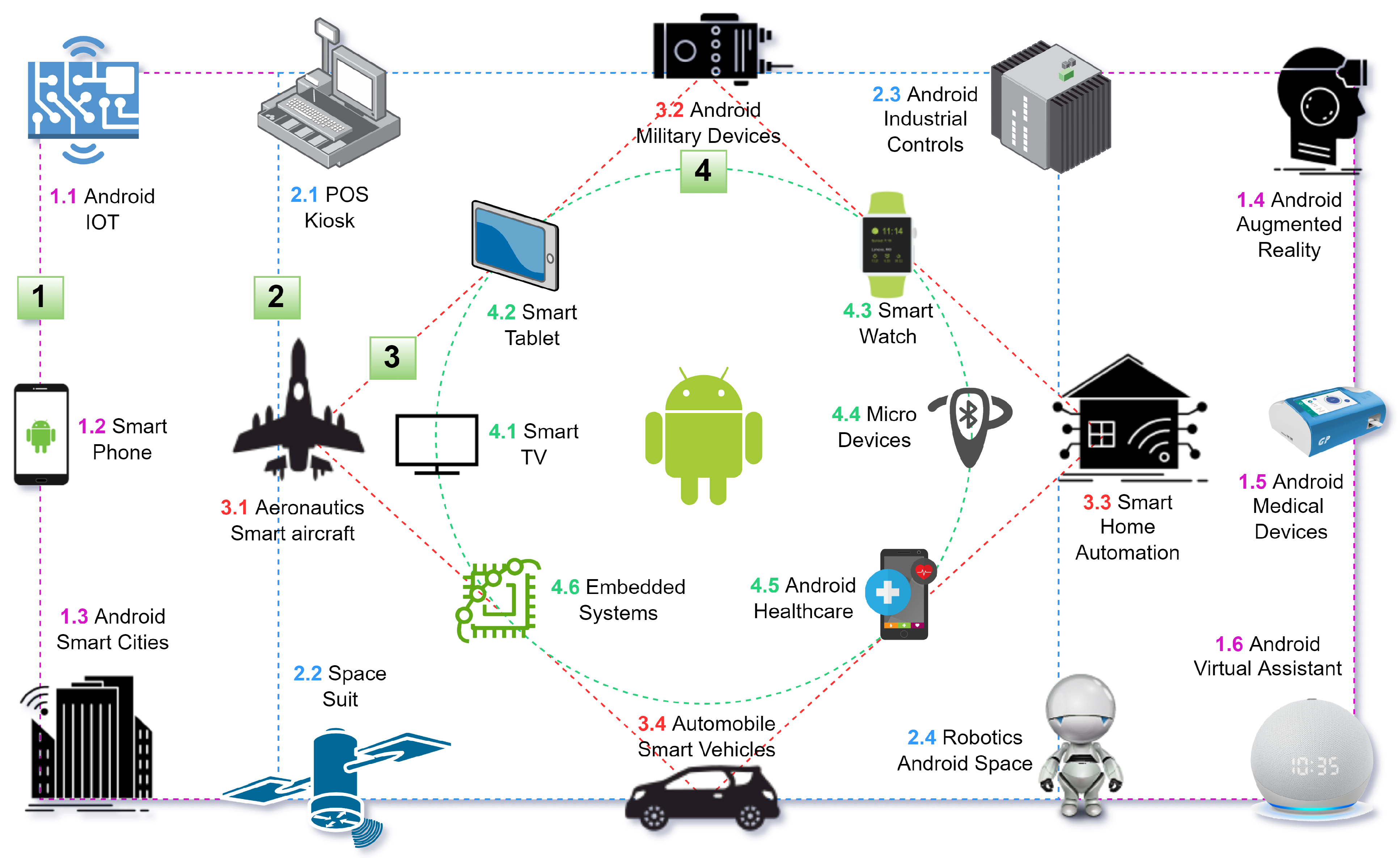
Technologies, Free Full-Text

Cryptographic ransomware encryption detection: Survey - ScienceDirect
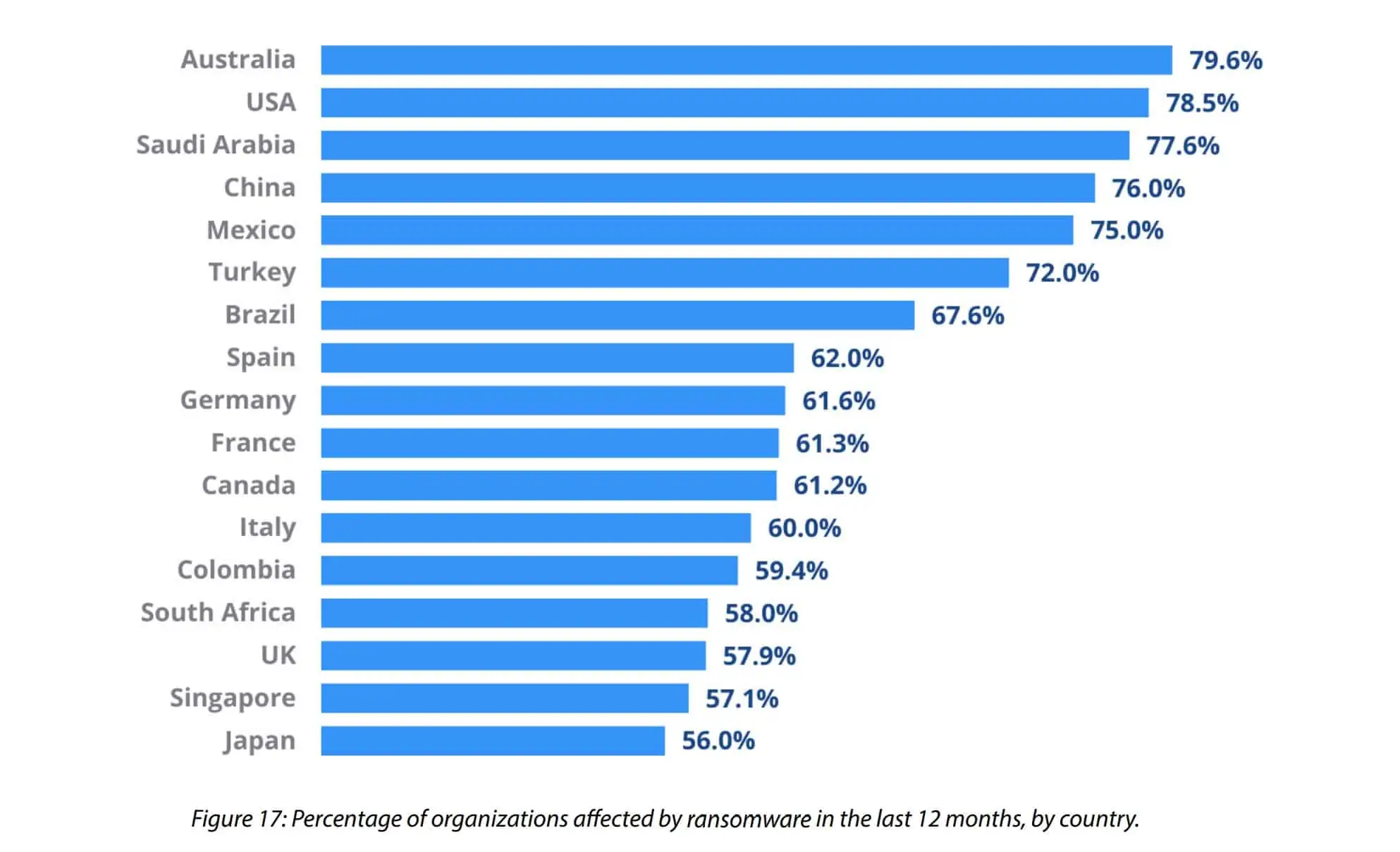
300+ Terrifying Cybercrime & Cybersecurity Statistics (2023)

A Complete List of All Adversarial Example Papers
Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity

Swedish Windows Security User Group » Microsoft Detection and Response Team (DART)

PDF) Accurate and Robust Malware Analysis through Similarity of External Calls Dependency Graphs (ECDG)

Machine learning in cybersecurity: a comprehensive survey - Dipankar Dasgupta, Zahid Akhtar, Sajib Sen, 2022
Recomendado para você
-
Rob Bux - DK 2122 dezembro 2024
-
 Roblox Comforward Help Form - Fill Out and Sign Printable PDF Template22 dezembro 2024
Roblox Comforward Help Form - Fill Out and Sign Printable PDF Template22 dezembro 2024 -
 My GUIs for disaster game - Creations Feedback - Developer Forum22 dezembro 2024
My GUIs for disaster game - Creations Feedback - Developer Forum22 dezembro 2024 -
 CPA Build on X: Roblox Robux Generator 2023 Robux Generator 2023 Robux Generator / X22 dezembro 2024
CPA Build on X: Roblox Robux Generator 2023 Robux Generator 2023 Robux Generator / X22 dezembro 2024 -
 Past Events Organized by Free Robux 2020 Working Robux Generator - Townscript22 dezembro 2024
Past Events Organized by Free Robux 2020 Working Robux Generator - Townscript22 dezembro 2024 -
 Roblox Robux Generator: Are They Safe? Do They Give Out Free Robux?22 dezembro 2024
Roblox Robux Generator: Are They Safe? Do They Give Out Free Robux?22 dezembro 2024 -
 Get unlimited robux. (Working + Proof)22 dezembro 2024
Get unlimited robux. (Working + Proof)22 dezembro 2024 -
![NewS] Roblox Generator No Human Verification Update Methods 2023 No Human Verification free Update Methods ! 16 December 2023, live scores, player stats, standings, fantasy games9212](https://i.ytimg.com/vi/ox2rT1KRkFI/maxresdefault_live.jpg) NewS] Roblox Generator No Human Verification Update Methods 2023 No Human Verification free Update Methods ! 16 December 2023, live scores, player stats, standings, fantasy games921222 dezembro 2024
NewS] Roblox Generator No Human Verification Update Methods 2023 No Human Verification free Update Methods ! 16 December 2023, live scores, player stats, standings, fantasy games921222 dezembro 2024 -
Robux-Generator 2023 No Human-Verification22 dezembro 2024
-
 Hackgenerator memes. Best Collection of funny Hackgenerator pictures on iFunny Brazil22 dezembro 2024
Hackgenerator memes. Best Collection of funny Hackgenerator pictures on iFunny Brazil22 dezembro 2024
você pode gostar
-
 This player definitely rage quit and uninstalled after what I did22 dezembro 2024
This player definitely rage quit and uninstalled after what I did22 dezembro 2024 -
 EDP445 Responds22 dezembro 2024
EDP445 Responds22 dezembro 2024 -
 BAKEMONOGATARI (manga) 13 (Paperback)22 dezembro 2024
BAKEMONOGATARI (manga) 13 (Paperback)22 dezembro 2024 -
Survival And Rise é um novo jogo de sobrevivência para jogadores móbil22 dezembro 2024
-
 Protogen - Insert Batteries Here - Blue/Purple Sticker for Sale22 dezembro 2024
Protogen - Insert Batteries Here - Blue/Purple Sticker for Sale22 dezembro 2024 -
 How To Claim Hazem's FREE ROBUX Codes FAST (Roblox Pls Donate)22 dezembro 2024
How To Claim Hazem's FREE ROBUX Codes FAST (Roblox Pls Donate)22 dezembro 2024 -
 Chainsawman22 dezembro 2024
Chainsawman22 dezembro 2024 -
 Race Predictor Running Time Calculator22 dezembro 2024
Race Predictor Running Time Calculator22 dezembro 2024 -
 Edição Premium Mortal Kombat 1 PS5 I MÍDIA DIGITAL - Diamond Games22 dezembro 2024
Edição Premium Mortal Kombat 1 PS5 I MÍDIA DIGITAL - Diamond Games22 dezembro 2024 -
 NOVIDADES INCRÍVEIS SOBRE O 6° ANIVERSÁRIO DO FLEE THE FACILITY!!!😱🎉 Roblox22 dezembro 2024
NOVIDADES INCRÍVEIS SOBRE O 6° ANIVERSÁRIO DO FLEE THE FACILITY!!!😱🎉 Roblox22 dezembro 2024


