How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 22 dezembro 2024
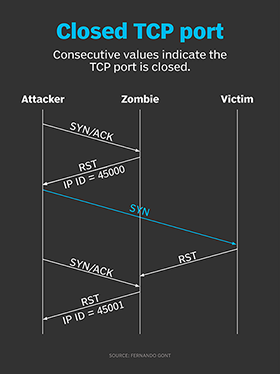
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

How to hide yourself using Idle scan (-sl) - Port scanning tutorial

Hacking techniques

Nmap – How to Use Nmap – Spyboy blog

Port Scanning - an overview
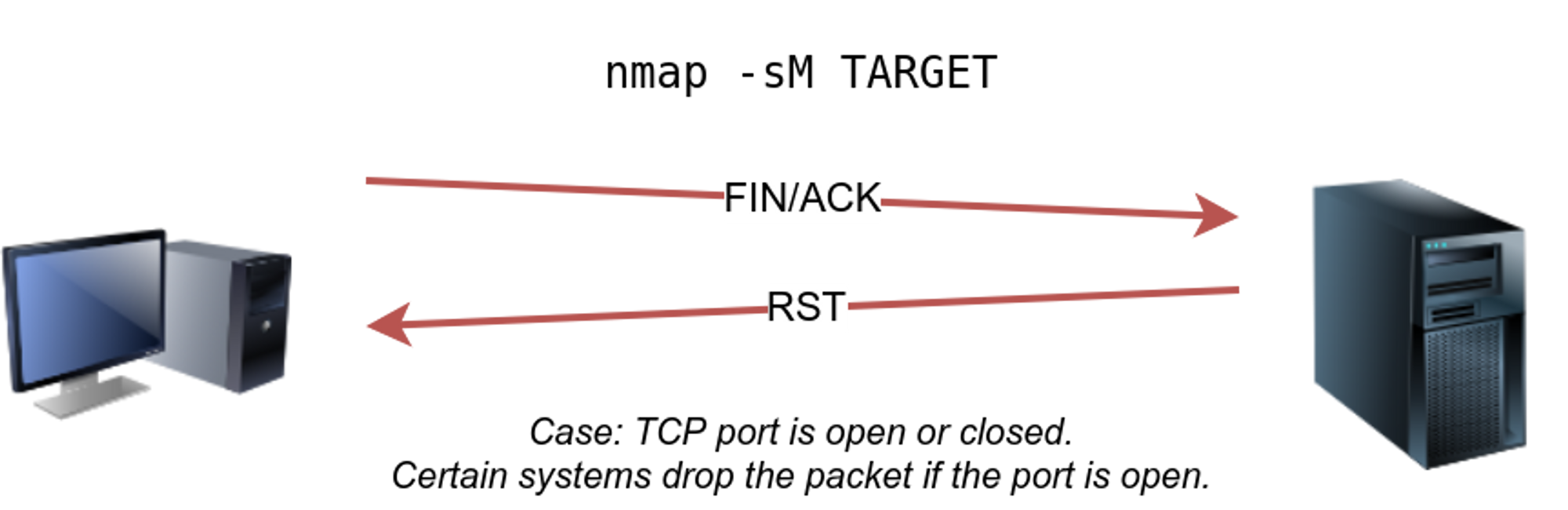
The Ultimate Guide to Port Scanning using Nmap
What is a Cyber Attack? Definition and Related FAQs
Network Scanning Techniques
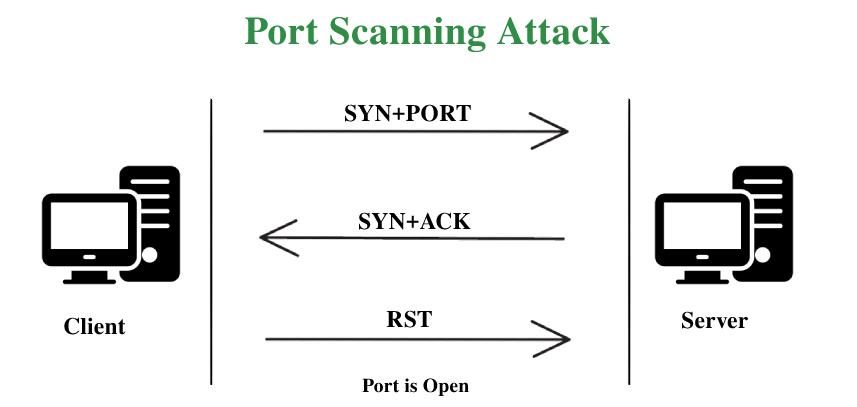
Port Scanning Attack - GeeksforGeeks

PPT - Port Scanning PowerPoint Presentation, free download - ID:4633948
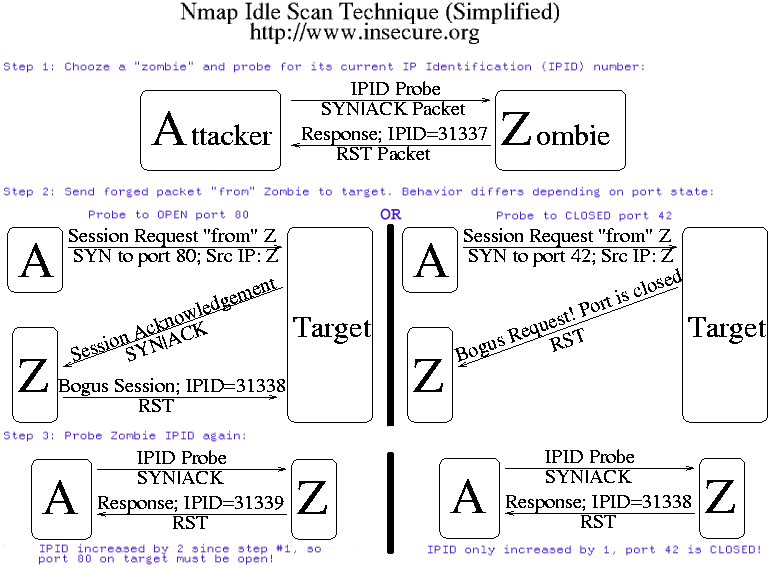
Idle Scanning and related IPID games

PDF) Surveying Port Scans and Their Detection Methodologies
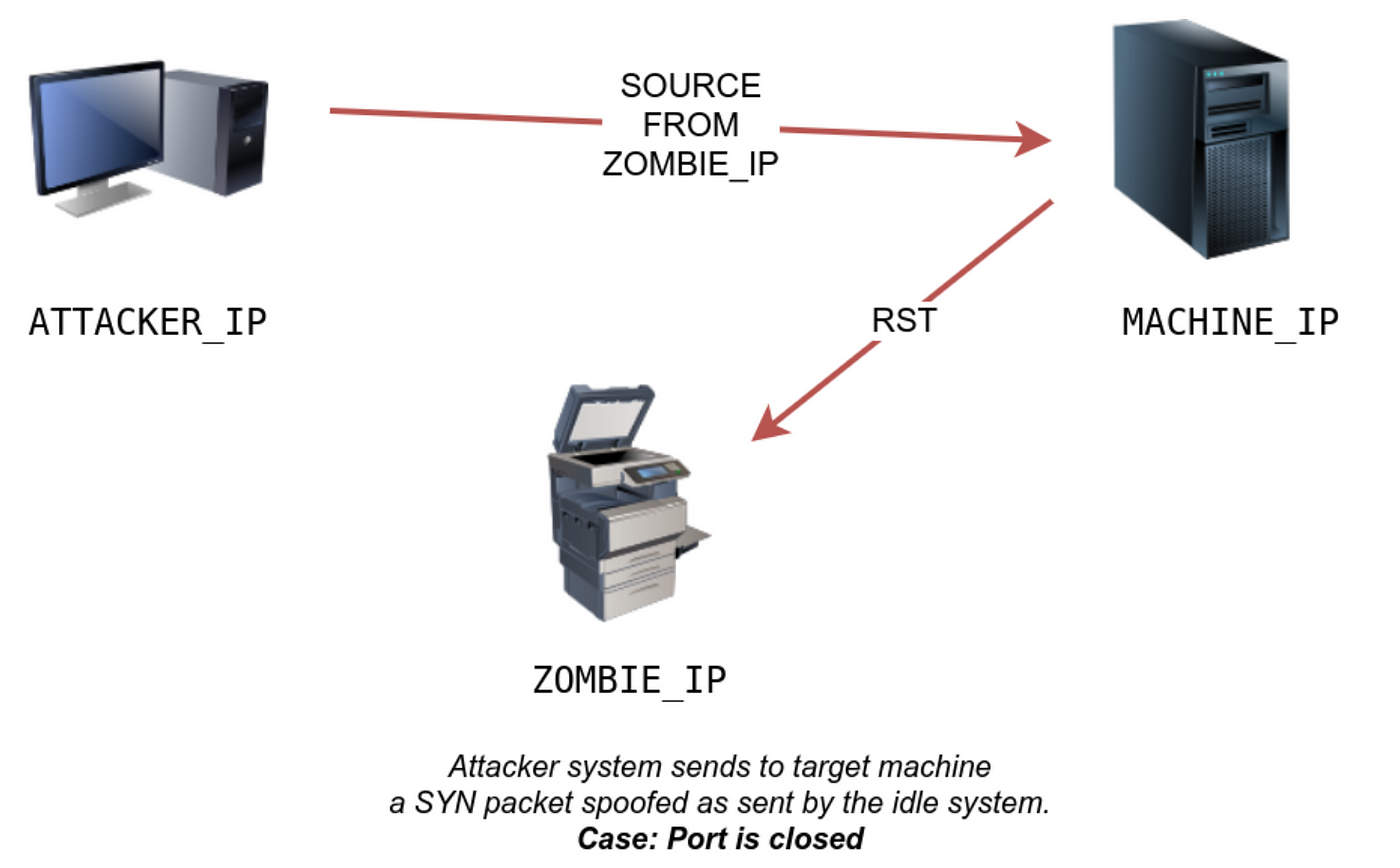
Nmap Advanced Port Scans, TryHackMe (THM), by Aircon
Recomendado para você
-
 The Fuck you Tony P Guide to getting around an IP ban!22 dezembro 2024
The Fuck you Tony P Guide to getting around an IP ban!22 dezembro 2024 -
 Malware analysis Suspicious activity22 dezembro 2024
Malware analysis Suspicious activity22 dezembro 2024 -
After exchanging my SWITCH to a ROUTER, I… - Apple Community22 dezembro 2024
-
 Block ads on all your devices using pfSense, Squid & SquidGuard22 dezembro 2024
Block ads on all your devices using pfSense, Squid & SquidGuard22 dezembro 2024 -
 Port Scan in Ethical Hacking - GeeksforGeeks22 dezembro 2024
Port Scan in Ethical Hacking - GeeksforGeeks22 dezembro 2024 -
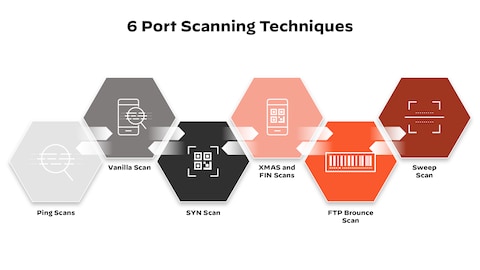 What is a Port Scan? - Palo Alto Networks22 dezembro 2024
What is a Port Scan? - Palo Alto Networks22 dezembro 2024 -
 Port Scanning Attack - GeeksforGeeks22 dezembro 2024
Port Scanning Attack - GeeksforGeeks22 dezembro 2024 -
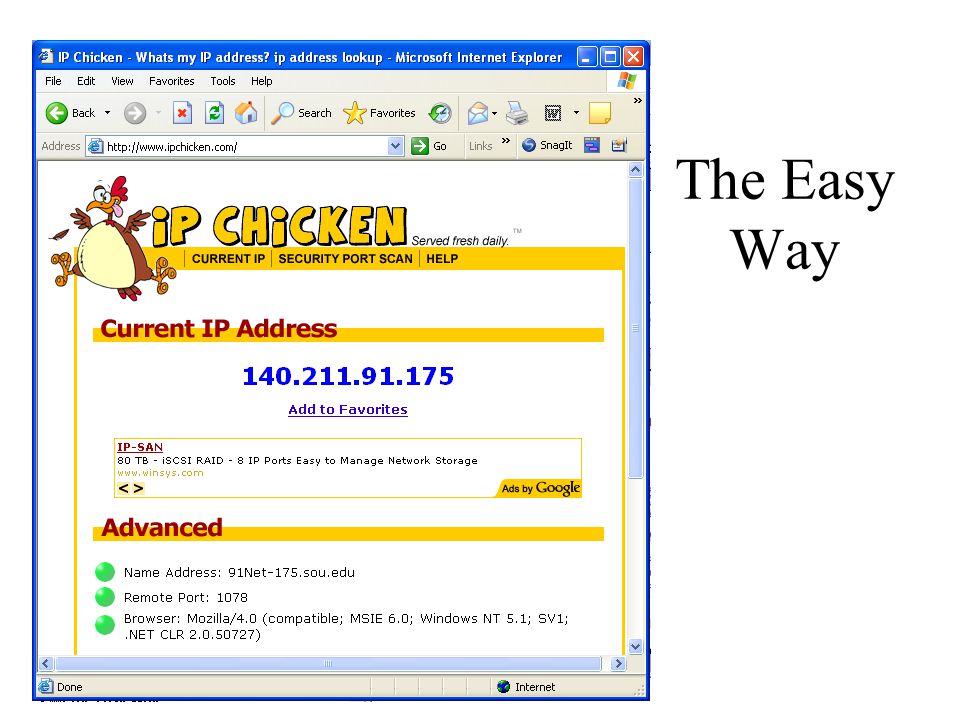 Phishing Analysis. Ojectives Phishing Internet Protocol (IP) addresses Domain Name System (DNS) names Analyse “From” addresses Analyse URL's Trace the. - ppt download22 dezembro 2024
Phishing Analysis. Ojectives Phishing Internet Protocol (IP) addresses Domain Name System (DNS) names Analyse “From” addresses Analyse URL's Trace the. - ppt download22 dezembro 2024 -
 Hacking Package Pickup22 dezembro 2024
Hacking Package Pickup22 dezembro 2024 -
 PoC Guide: Citrix Secure Internet Access with Citrix SD-WAN22 dezembro 2024
PoC Guide: Citrix Secure Internet Access with Citrix SD-WAN22 dezembro 2024
você pode gostar
-
 Como ser um conservador (Portuguese Edition) - Kindle edition by Scruton, Roger. Politics & Social Sciences Kindle eBooks @ .22 dezembro 2024
Como ser um conservador (Portuguese Edition) - Kindle edition by Scruton, Roger. Politics & Social Sciences Kindle eBooks @ .22 dezembro 2024 -
 A Rewatch further than the Universe! Sora Yori mo Tooi Basho rewatch - EPISODE 7 DISCUSSION : r/anime22 dezembro 2024
A Rewatch further than the Universe! Sora Yori mo Tooi Basho rewatch - EPISODE 7 DISCUSSION : r/anime22 dezembro 2024 -
 Dónde está la caja negra del avión que se ha estrellado en Fortnite22 dezembro 2024
Dónde está la caja negra del avión que se ha estrellado en Fortnite22 dezembro 2024 -
𝕄𝕦𝕟𝕕𝕠 𝕕𝕒 𝟟ª 𝔸𝕣𝕥𝕖 - O ator Alfred Molina tem 68 anos, e22 dezembro 2024
-
 Definição: O que são jogos esportivos, jogos populares e jogos de22 dezembro 2024
Definição: O que são jogos esportivos, jogos populares e jogos de22 dezembro 2024 -
 Pokémon Scarlet & Violet ganhará duas expansões; veja datas e mais22 dezembro 2024
Pokémon Scarlet & Violet ganhará duas expansões; veja datas e mais22 dezembro 2024 -
 Stream College Brawl APK: The Latest Version of the Popular Game for Android from Imerrezo22 dezembro 2024
Stream College Brawl APK: The Latest Version of the Popular Game for Android from Imerrezo22 dezembro 2024 -
 Heapside Prison Baldurs Gate 3 Wiki22 dezembro 2024
Heapside Prison Baldurs Gate 3 Wiki22 dezembro 2024 -
 Anime Reviews: Berserk - HubPages22 dezembro 2024
Anime Reviews: Berserk - HubPages22 dezembro 2024 -
 Diecast model cars Ford GT 1/18 Autoart lm spec race car # 422 dezembro 2024
Diecast model cars Ford GT 1/18 Autoart lm spec race car # 422 dezembro 2024
